This guide provides information about basic configuration of security policies (ac-
cess control policies) on the Cisco ASA Firepower module, using the Cisco Adap-
tive Security Device Manager (ASDM). Before proceeding, make sure that you have
completed the initial configuration of the Cisco ASA with Firepower Services, refer
to the separate "Cisco ASA with Firepower Services Easy Setup Guide" and so on.
Some configurations in this guide require having optional licenses installed. In those
cases, "MEMO" or "Caution" columns specify the necessary licenses.
The Cisco ASA with Firepower Services ship with a base license for Application
Visibility and Control (AVC). Optional subscriptions for Next-Generation IPS
(
N-
GIPS
)
, Cisco Advanced Malware Protection
(
AMP
)
, and URL Filtering (URL) can
be added to the base configuration for advanced functionality.
●
AVC
:
Supports more than 3,000 application-layer and risk-based controls that
can launch tailored intrusion prevention system (IPS) threat detection policies to
optimize security effectiveness.
●
NGIPS
:
Provides highly effective threat prevention and full contextual awareness
of users, infrastructure, applications, and content to detect multivector threats
and automate defense response.
●
AMP
:
Delivers inline network protection against sophisticated malware and Cisco
Threat Grid sandboxing.
●
URL
:
Adds the capability to filter more than 280 million top-level domains by risk
level and more than 82 categories.
Redirect traffic to the ASA Firepower module by creating a service policy on the
ASA that identifies specific traffic that you want to send.
Preconfiguring
1
1-1 Before You Begin
1-2 Configuring Service Policy
1
1
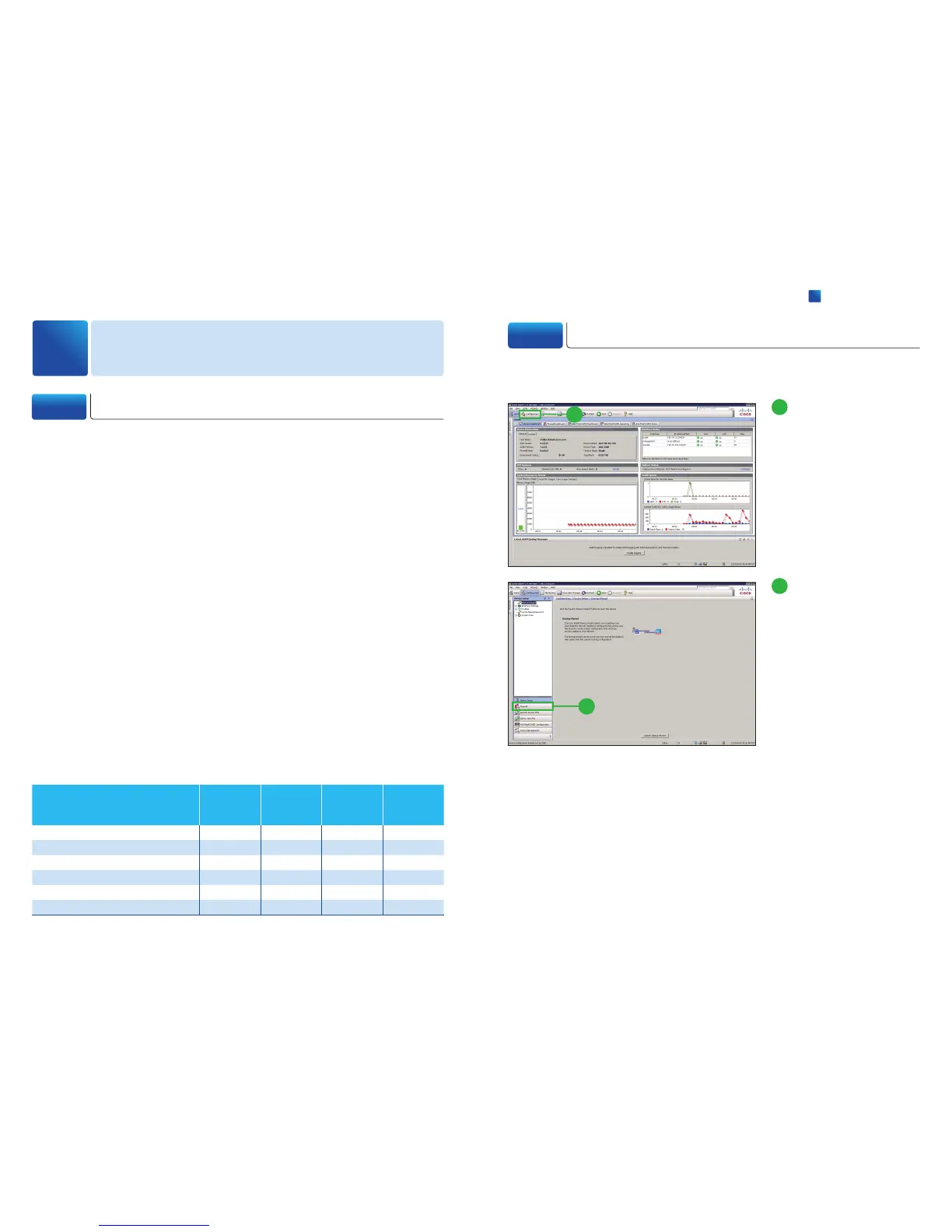
Click [Configuration].
2
2
Click [Firewall].
Optional Licenses
Characters
Included
in SKU
NGIPS AMP URL
NGIPS License TA
●
- -
AMP License AMP -
●
-
URL License URL - -
●
NGIPS & AMP License TAM
● ●
-
NGIPS & URL License TAC
●
-
●
NGIPS & AMP & URL License TAMC
● ● ●

 Loading...
Loading...











