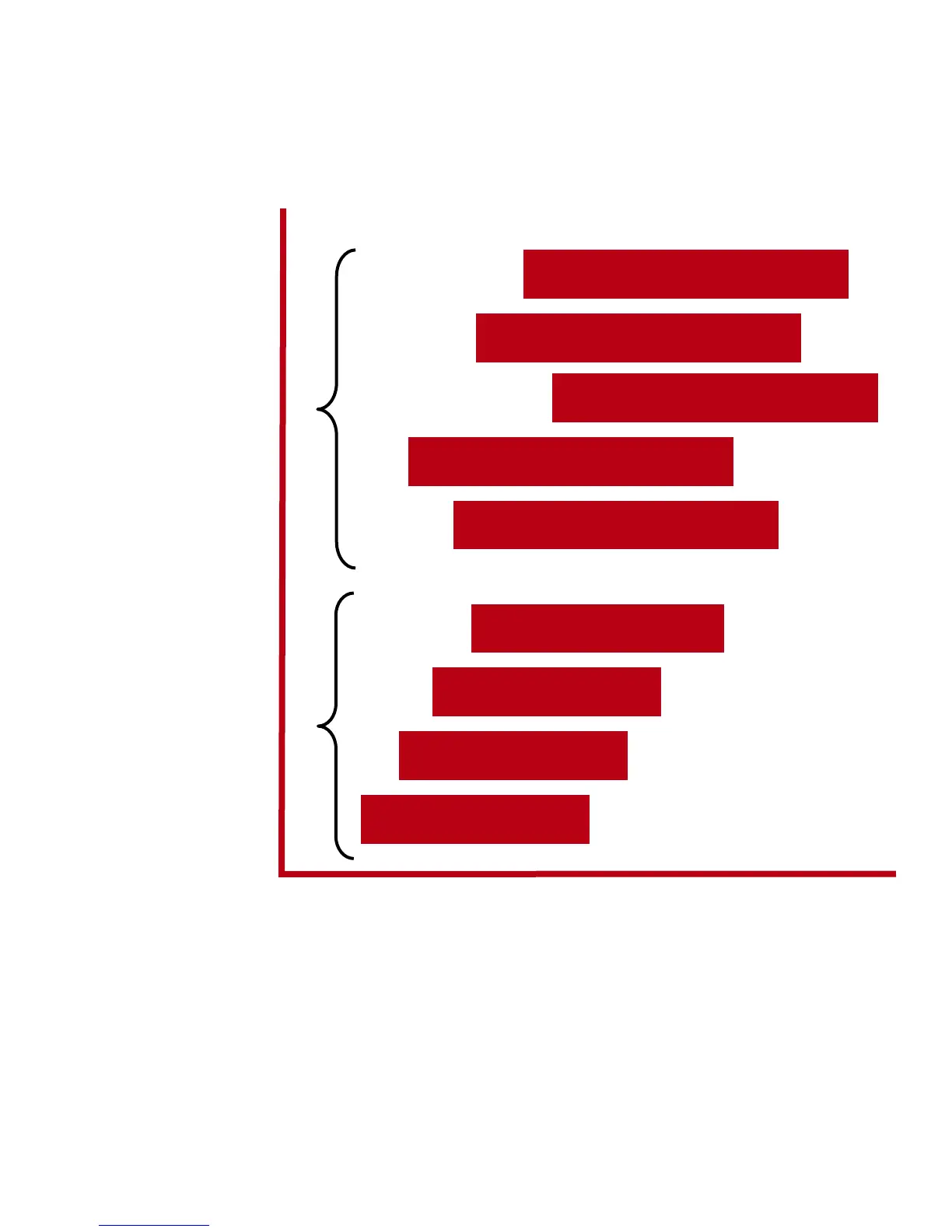
Suitability to Task
Each authentication device provides a tradeoff between ease of use, administrative complexity and
level of security. The following graph visually represents where these devices fit in the administrative
complexity versus level of security spectrum.
More Secure Less Secure
Level of Security
Simple Complex
Administrative Complexity
Weak Password
Biometrics (Local)
Biometric (Enterprise)
Hardware Token (Smartcard
USB
with Stored PIN
Hardware Token (Smartcard,
USB
with PKI
TPM
Two factor (Biometric and
Stron
Password
Three factor (Biometric,
Token and PIN
Multi-Factor Authentication
Sin
le-Factor Authentication
Stron
Password
8
 Loading...
Loading...















