Xerox D110/D125 Copier/Printer
セキュリティターゲット
- 47 – Copyright
2012 by Fuji Xerox Co., Ltd
Hierarchical to: No other components
Dependencies: [FDP_ITC.1 Import of user data without security attributes, or
FDP_ITC.2 Import of user data with security attributes, or
FCS_CKM.1 Cryptographic key generation]
FCS_CKM.4 Cryptographic key destruction
FCS_COP.1.1 The TSF shall perform [assignment: list of cryptographic
operations] in accordance with a specified cryptographic
algorithm [assignment: cryptographic algorithm] and
cryptographic key sizes [assignment: cryptographic key sizes]
that meet the following: [assignment: list of standards].
[assignment: list of standards]
- FIPS PUB 197
[assignment: cryptographic algorithm]
- AES
[assignment: cryptographic key sizes]
- 256bits
[assignment: list of cryptographic operations]
- encryption of the document data to be stored in the internal
HDD and decryption of the document data retrieved from the
internal HDD.
6.1.3. Class FDP: User Data Protection
The Security Function Policy (SFP) described in Table16 is referenced by the Class
FDP SFRs in this clause.
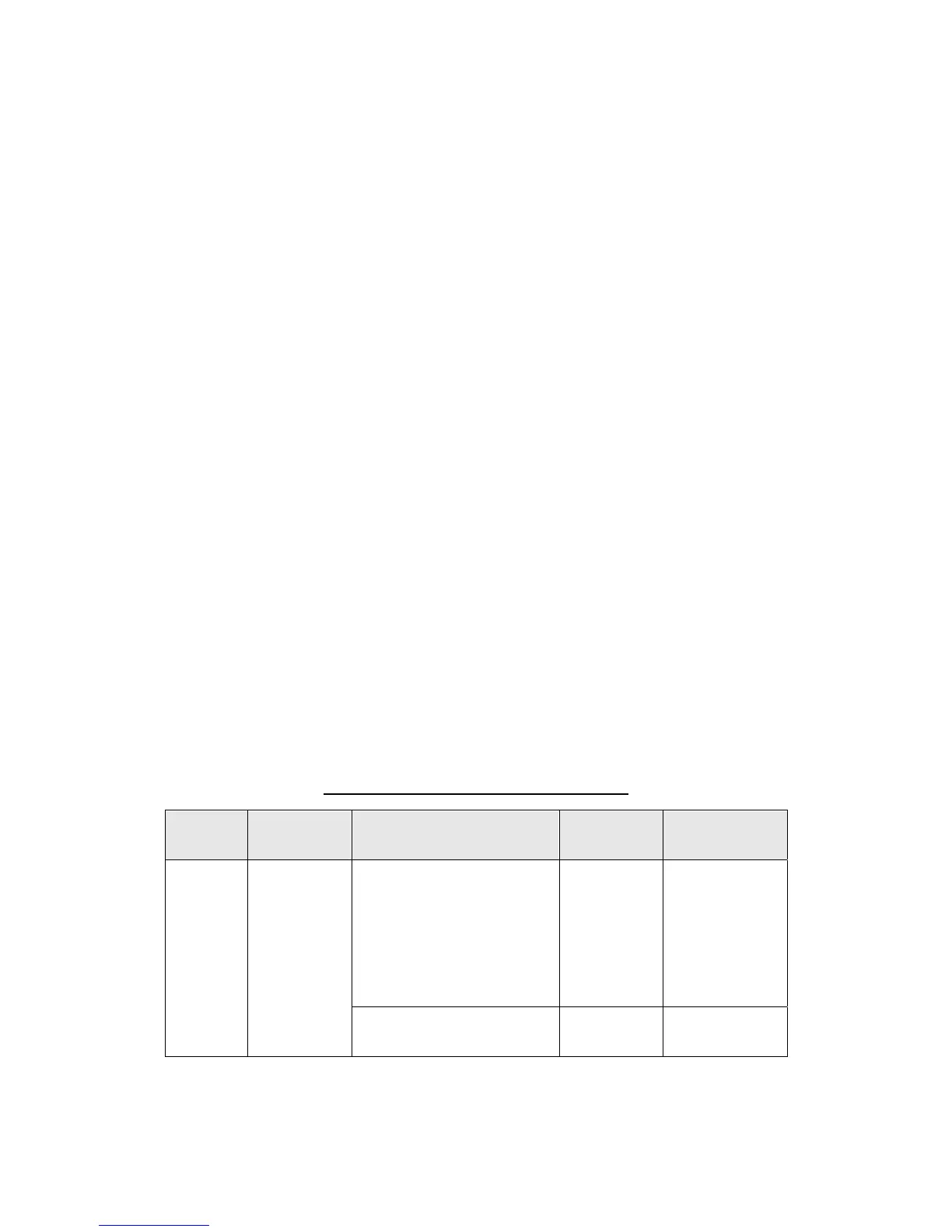
Table 16 Common Access Control SFP
Object Attribute Operation(s) Subject *Access
control rule
D.DOC attributes
from Table
17
Delete
- Delete the document
data in Mailbox and
Private Print
U.USER Denied,
except for
his/her own
documents
- R1
- R2
- Register the document
data to the Mailbox
U.USER - R3
 Loading...
Loading...



















