Xerox Multi-Function Device Security Target
44
Copyright
2013 Xerox Corporation. All rights reserved.
Digital signature generation
and verification
FIPS 198 (cert #644 and
#1076)
*Cryptographic Algortithm Validation Program (CAVP) certificates
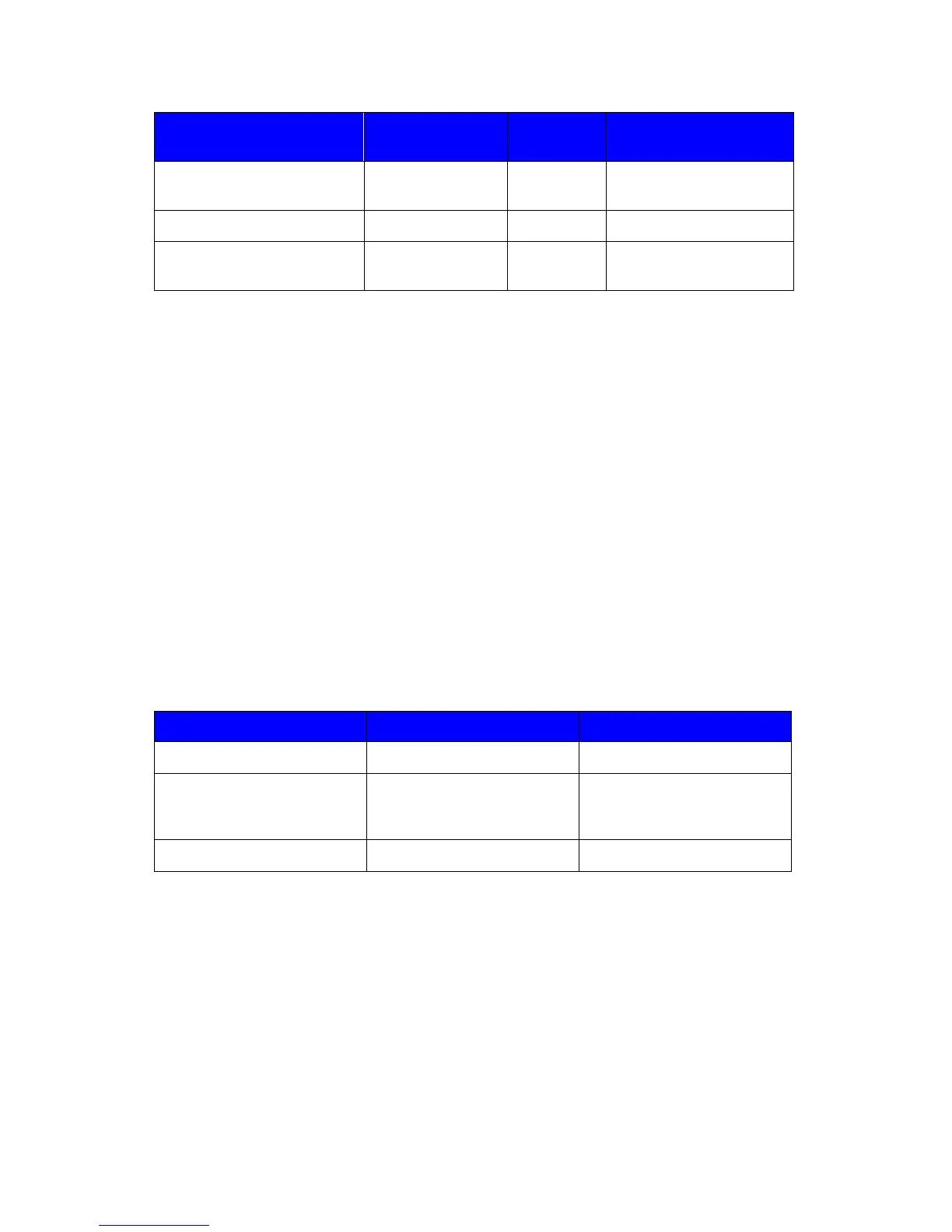
6.3.3.2. FCS_CKM.1 Cryptographic key generation
Hierarchical to: No other components.
Dependencies: [FCS_CKM.2 Cryptographic key distribution, or
FCS_COP.1 Cryptographic operation]
FCS_CKM.4 Cryptographic key destruction
FCS_CKM.1.1 The TSF shall generate cryptographic keys in accordance
with a specified cryptographic key generation algorithm
[the cryptographic algorithms listed in the Cryptographic
Algorithm column of Table 26] and specified
cryptographic key sizes [the cryptographic key sizes
listed in the Key Sizes (bits) column of Table 26] that
meet the following: [the standards in the Standards
column of Table 26].
Table 26: Cryptographic key generation
Randomization of network
interface MAC address
upon boot up.
6.3.3.3. FCS_CKM.2 Cryptographic key distribution
Hierarchical to: No other components.
Dependencies: [FDP_ITC.1 Import of user data without security
attributes, or
FDP_ITC.2 Import of user data with security attributes, or
FCS_CKM.1 Cryptographic key generation]
FCS_CKM.4 Cryptographic key destruction

 Loading...
Loading...















