Juniper Networks SSG 5 and SSG 20 Security Policy
Physical Security Policy
Before carrying out any steps to deploy a Juniper Networks security appliance, the end-user must
verify the security of the product with the following observations:
1. Confirm that the product received matches the version that is validated as FIPS 140-2
compliant.
2. The outside packaging does not show damage or evidence that is has been opened. If
the cardboard shows damage that would allow the device to be removed or exchanged,
this may be evidence of tampering.
3. Each box is packaged with custom tape to indicate that the device was packaged by
Juniper Networks or an authorized manufacturer. The tape is unique, with the words
Juniper Networks printed repeatedly along the tape. If the tape is not present, the device
may have been tampered with.
4. The internal packaging does not show damage or evidence of tampering. The plastic
bag should not have a large hole and the label that seals the plastic bag should not be
detached or missing. If the bag or seal are damaged in any way, the device may have
been tampered with.
The security appliance is contained within a metal production-grade enclosure that is opaque to visible
spectrum radiation. The enclosure includes a removable cover that must be protected by a tamper-
evident seal.
The Cryptographic Officer is responsible for securing and having control at all times of any unused
seals and the direct control and observation of any changes to the module such as reconfigurations
where the tamper evident seals or security appliances are removed or installed to ensure the security
of the module is maintained during such changes and the module is returned to a FIPS Approved
state.
Tamper seals are applied in the same fashion regardless of the part number of the device.
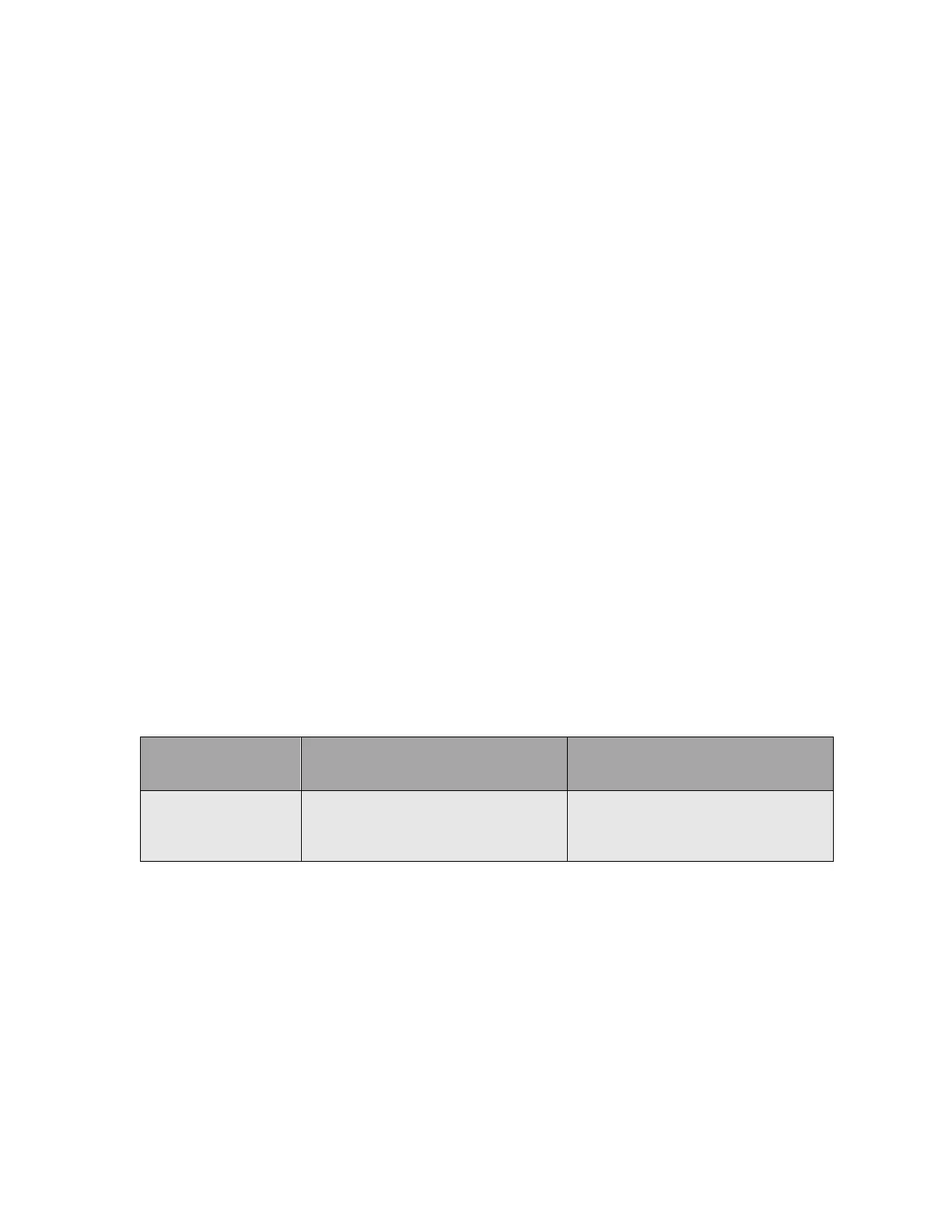
Inspection/Testing of Physical Security Mechanisms
Physical Security
Mechanisms
Recommended Frequency of
Inspection/Test
Inspection/Test Guidance Details
Tamper labels,
opaque metal
enclosure.
Upon receipt of the module and per
security policy by the Cryptographic
Officer.
Labels should be free of any tamper
evidence.
Seals are available for order via part number JNPR-FIPS-TAMPER-LBLS. If a seal is missing or
damaged, the device may have been tampered with. Tamper-evident seals should be applied as
described below.
For all seal applications, the Cryptographic Officer should observe the following instructions.
• Handle the seals with care. Do not touch the adhesive side.
• All surfaces to which the seals are to be applied must be prepared by using an alcohol wipe to
ensure that all surfaces are clean and clear of any residue.
• Apply with firm pressure across the seal to ensure adhesion. Allow at least 1 hour for the
adhesive to cure.
 Loading...
Loading...