Page 60 of 81
Copyright (c) 2010 RICOH COMPANY, LTD. All Rights Reserved.
O.GENUINE Protection of integrity of MFP Control Software integrity
Following are the rationale behind the functional requirements corresponding to O.GENUINE in Table 22,
and these requirements are included to fulfil the O.GENUINE specification.
a) Check the integrity of the MFP Control Software.
To fulfil O.GENUINE, the integrity of the MFP Control Software, which is installed in FlashROM,
shall be verified. For this, FPT_TST.1 tests the integrity of the executable code of the MFP Control
Software, which is installed in the FlashROM, and verifies its integrity at TOE start-up.
O.LINE_PROTECT Protection from intrusion via telephone line
Following are the rationale behind the functional requirements corresponding to O.LINE.PROTECT in Table
22, and these requirements are included to fulfil the O.LINE.PROTECT specification.
a) Prohibit intrusion via the fax line.
To fulfil O.LINE_PROTECT, unauthorised access by an attacker to the TOE via telephone line shall be
prevented.
For this, FDP_IFC.1 and FDP_IFF.1 allow fax data to pass from the fax process on the Fax Unit to the
fax reception process on the Controller Board only if the data received from the telephone line is fax
data.
6.3.3 Dependency Analysis
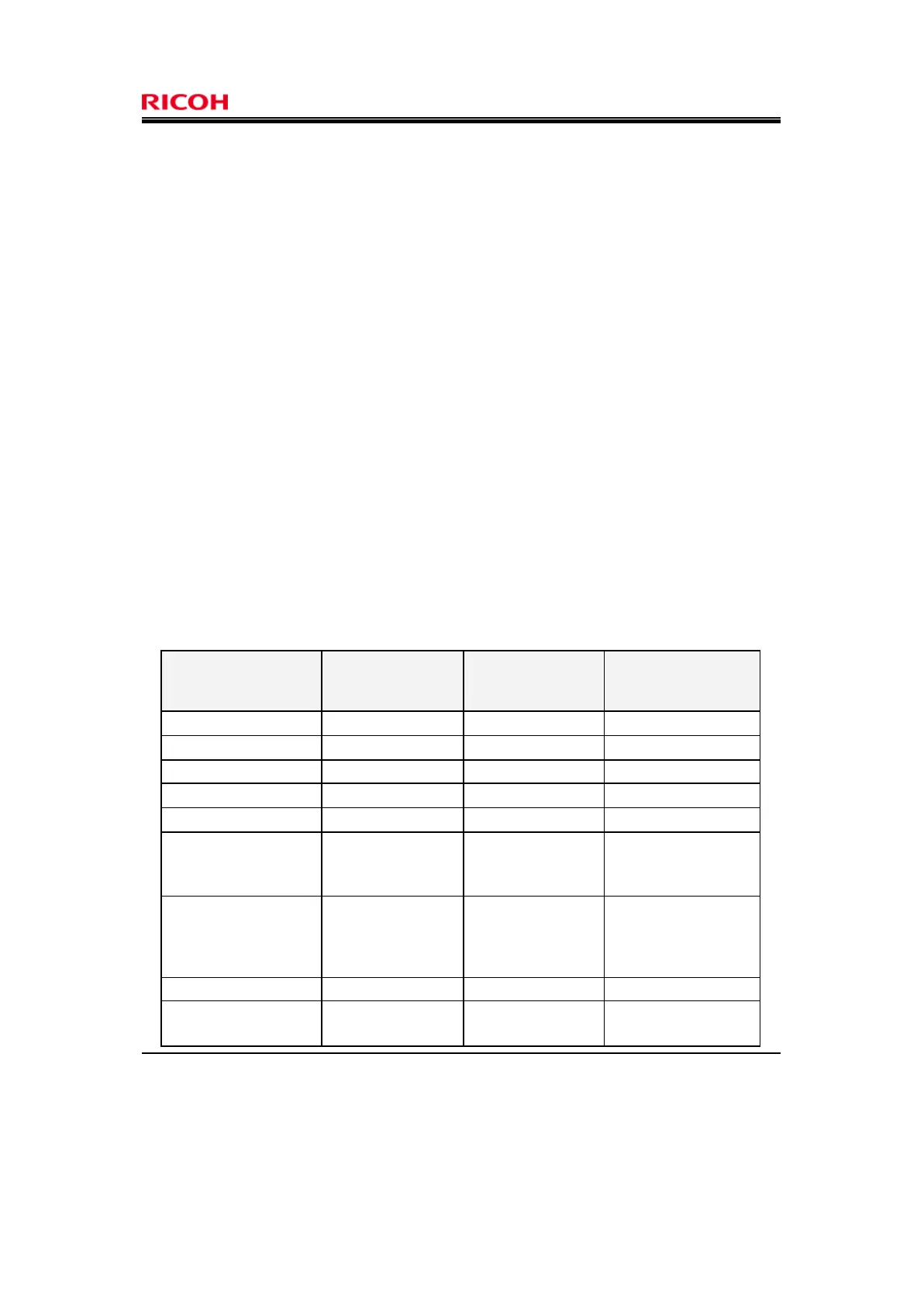
Table 23 shows the correspondence of dependencies in this ST for the TOE security functional requirements.
Table 23: Correspondence of dependencies of TOE security functional requirements
TOE security
functional
requirements
Dependencies
claimed by CC
Dependencies
satisfied in ST
Dependencies not
satisfied in ST
FAU_GEN.1 FPT_STM.1 FPT_STM.1 None
FAU_SAR.1 FAU_GEN.1 FAU_GEN.1 None
FAU_SAR.2 FAU_SAR.1 FAU_SAR.1 None
FAU_STG.1 FAU_GEN.1 FAU_GEN.1 None
FAU_STG.4 FAU_STG.1 FAU_STG.1 None
FCS_CKM.1
[FCS_CKM.2 or
FCS_COP.1]
FCS_CKM.4
FCS_COP.1 FCS_CKM.4
FCS_COP.1
[FDP_ITC.1 or
FDP_ITC.2 or
FCS_CKM.1]
FCS_CKM.4
FCS_CKM.1 FCS_CKM.4
FDP_ACC.1 FDP_ACF.1 FDP_ACF.1 None
FDP_ACF.1 FDP_ACC.1
FMT_MSA.3
FDP_ACC.1
FMT_MSA.3
None

 Loading...
Loading...