Measured Boot
XAPP1309 (v1.0) March 7, 2017 8
www.xilinx.com
In Zynq-7000 AP SoCs, the term secure boot is used to define the secure loading of the
bitstream and software at power-on. The bitstream is loaded into on-chip configuration
memory. Software partitions encrypted in non-volatile memory (NVM) are generally
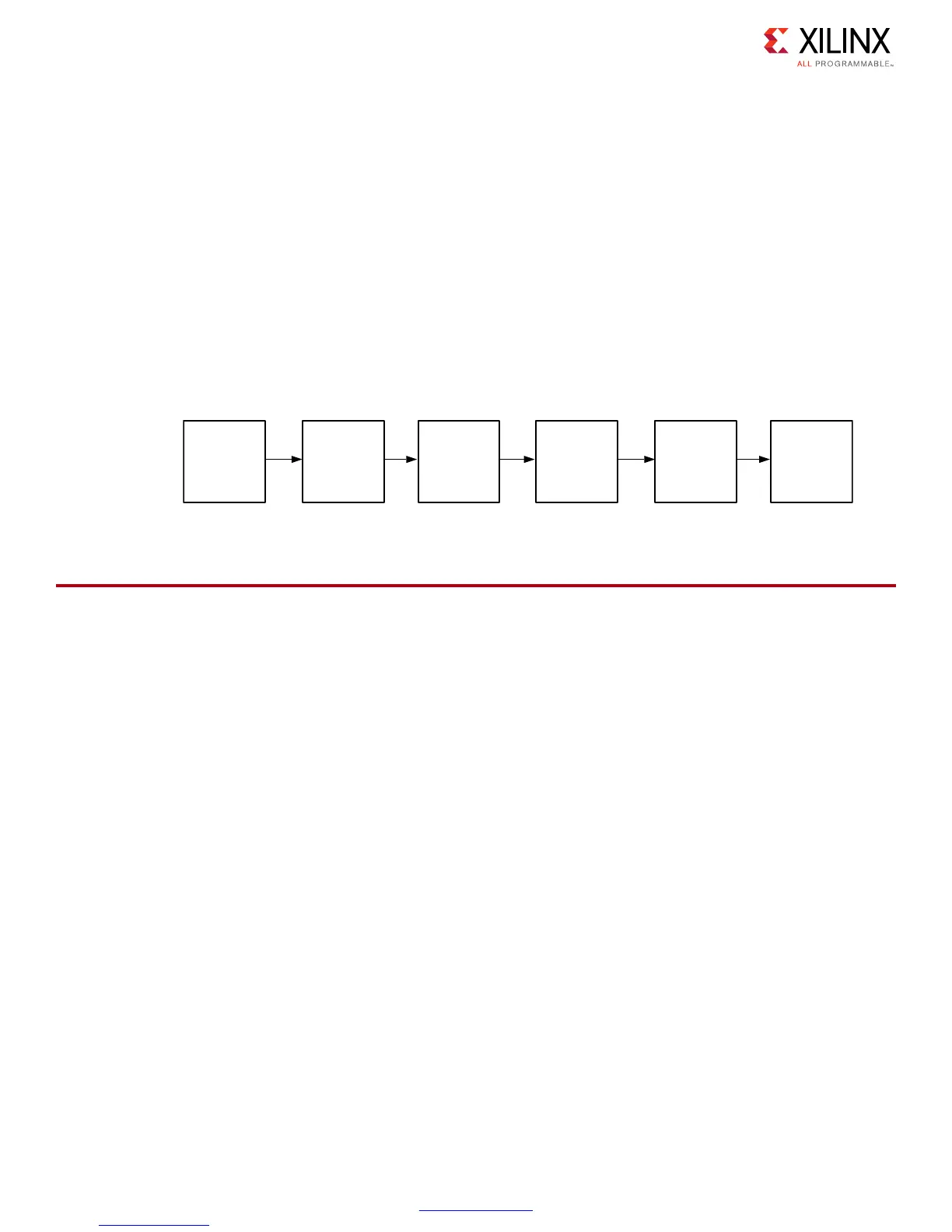
authenticated, decrypted, and copied to DDR memory. As shown in Figure 6, the RSA-2048
authentication uses a chain of trust sequentially on each partition loaded. Each partition can
use its own private/public key pair. Partitions can optionally be authenticated using keyed-hash
message authentication code (HMAC). In its simplest form, all partitions loaded by the FSBL are
authenticated using RSA-2048 from the XILRSA library. In an alternative boot flow, U-Boot has
access to the XILRSA library. In secure boot, if either RSA or HMAC authentication fails, the
Zynq-7000 AP SoC transitions to a lockdown state.
A malicious actor needs to steal the RSA private key, which is not stored in the device, and the
HMAC key. To protect against an insider attack, the SDK Bootgen key management can be split
so that independent parties handle RSA, AES, and HMAC keys.
Measured Boot
Measured boot is recommended when embedded systems are connected to a network. Secure
boot should still be used in systems which use measured boot. Secure boot and measured boot
functionality are complementary. Connecting embedded systems to a network provides a
method for firmware updates. Embedded systems connected to a network have a wider attack
surface than closed systems. Hackers with network access are a common security threat.
Remote attestation addresses this vulnerability during boot and run time. In secure and
measured boot, all files/partitions are authenticated and measured.
The basics of measured boot are discussed in Integrity Measurement Architecture. The
measured boot in the reference design uses a TPM for added security. Trusted Platform Module,
Zynq 7000 SoC-TPM Interface, and Network Security in Measured Boot discuss measured boot
using a TPM. Secure boot and measured boot do not use programmable logic resources, so the
Zynq-7000 AP SoC unit cost is not affected when measured boot is used.
Using measurements, an attestation server can periodically execute run-time integrity checks
on clients, and execute a policy based on the results. This is important in connected systems
because the probability of an attack during run time is high. The ability to implement a policy
is an improvement over the runtime integrity checker (RTIC) described in Run Time Integrity and
Authentication Check of Zynq-7000 AP SoC System Memory (XAPP1225) [Ref 2].
X-Ref Target - Figure 6
Figure 6: Zynq-7000 AP SoC Chain of Trust Boot
BootROM
FSBL
U-Boot
Linux
Kernel
Root
File
System
Linux
App(s)
X18731-020317

 Loading...
Loading...











