Juniper Networks SSG 320M and 350M Security Policy
Below is a list of the public keys utilized by the module:
Firmware Authentication Key: Used by the device to verify DSA signatures over
firmware images.
CA DSA/RSA Public Key: Used by IKE to authenticate a peer’s certificate.
Local DSA/RSA/ECDSA Public Key: Used by the IKE peer to verify digital signatures.
SSH Server/Host DSA Public Key: Used by the SSH client to verify digital signatures.
SSH Client DSA Public Key: Used by the device to verify digital signatures.
Diffie Hellman Public Key Components: Used by the DH Key Agreement protocol.
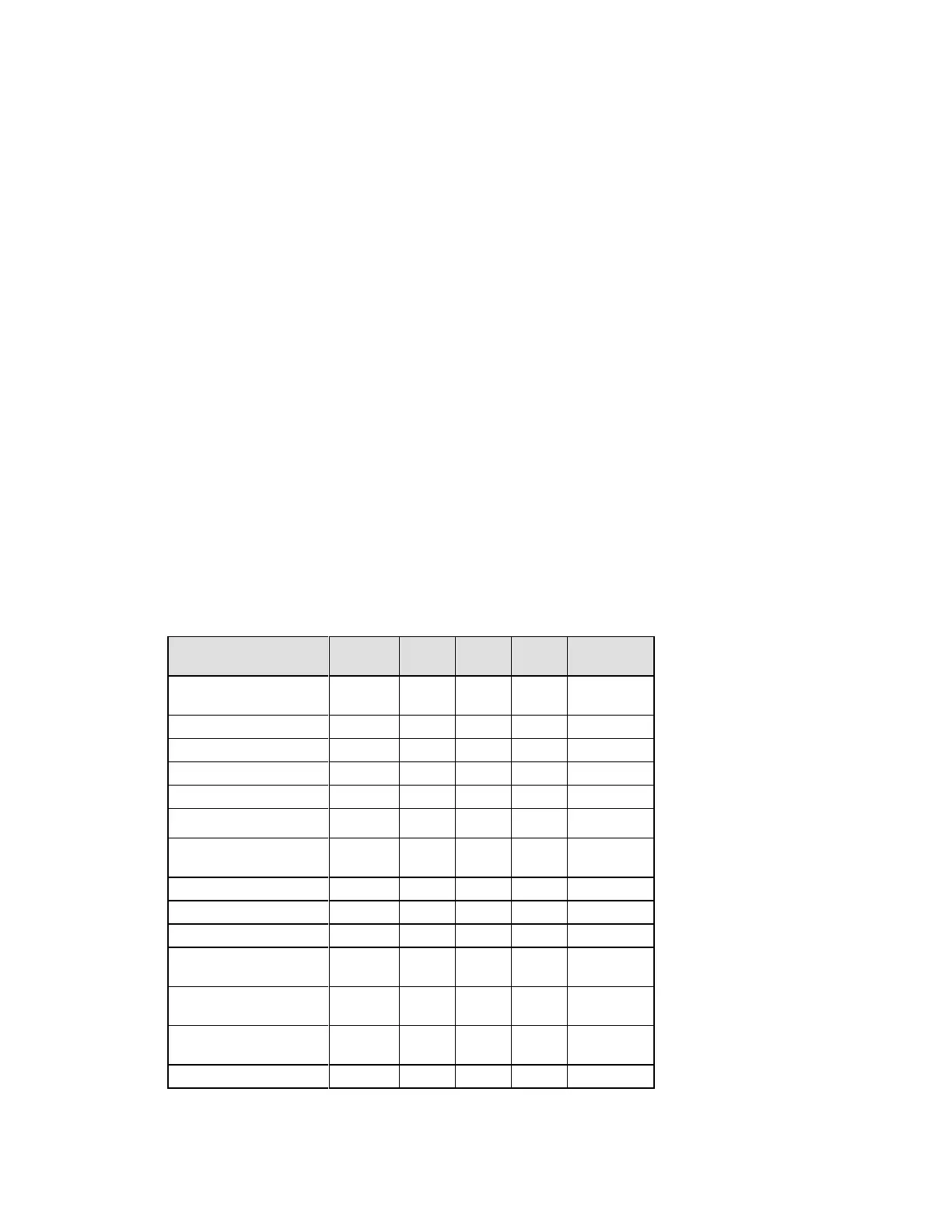
Matrix Creation of Critical Security Parameter (CSP) versus the
Services (Roles & Identity)
The following matrices define the set of services to the CSP of the module, providing information on
generation, destruction and usage. They also correlate the User roles and the Crypto-Officer roles to
the set of services to which they have privileges.
The matrices use the following convention:
G: Generate
D: Delete
U: Usage
N/A: Not Available
Table A: Crypto-Officer
SSH Server/Host DSA
Private Key
IKE RSA/DSA/ECDSA
Private Key
Diffie Hellman Private
Key Components
 Loading...
Loading...