Configuration Guide 7. IPSec Tunneling
Version 7.2 31 Security Setup
7.1 Configuration Examples
This section provides configuration examples for IPSec.
7.1.1 Configuring IPSec
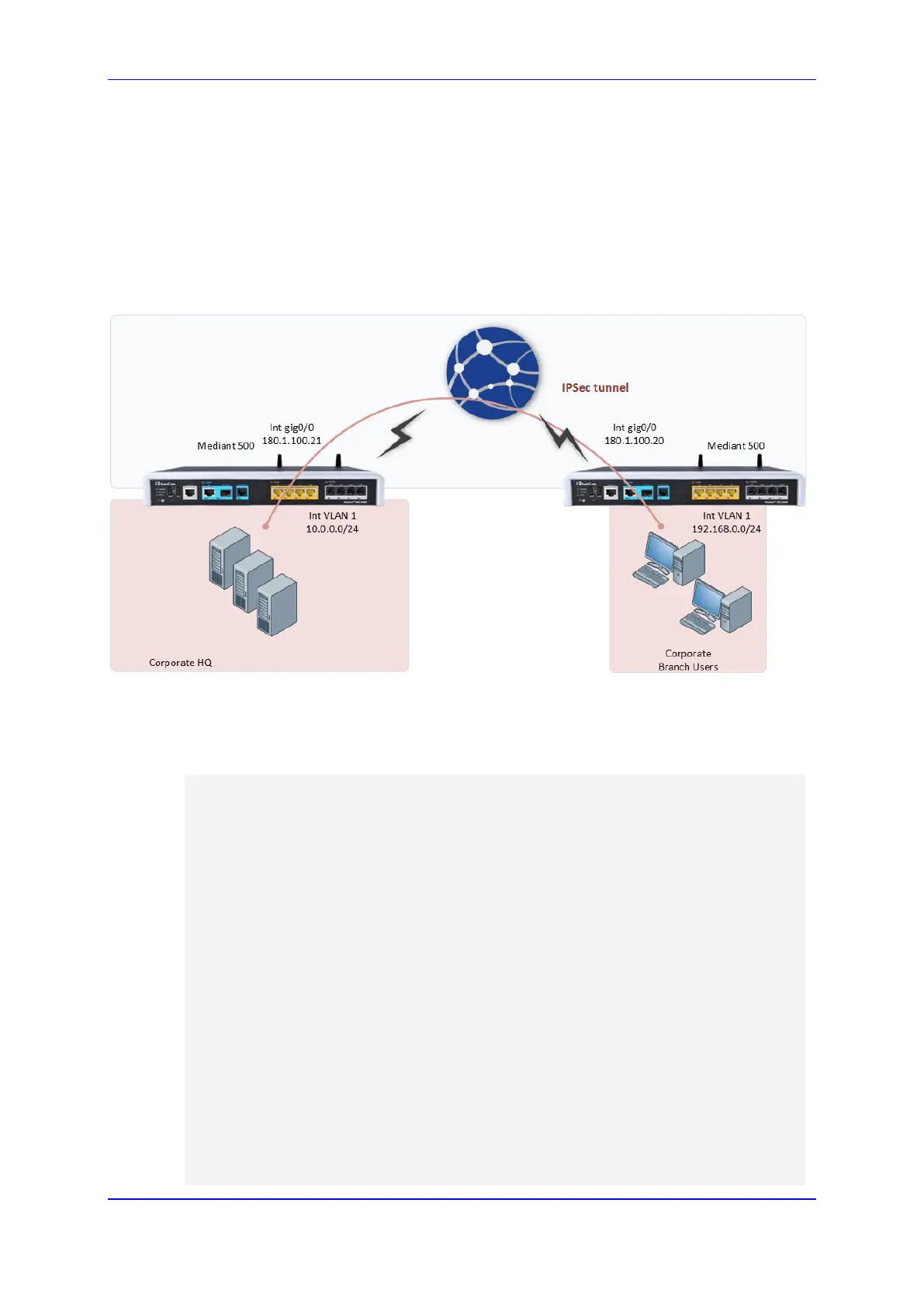
This example includes two routers connected back to back using interface
Gigabitethernet0/0, as shown in Figure 7-2: IPSec Example. All traffic captured in the
access-list is encrypted.
Figure 7-2: IPSec Example
IPSec configuration of the device on the right-hand side (Corporate Branch Users) is as
follows:
access-list ipsec permit ip 192.168.0.0 0.0.0.255 10.0.0.0
0.0.0.255
crypto isakmp policy 1
encryption aes 128
authentication pre-share
hash sha
group 2
lifetime 3600
exit
crypto ipsec transform-set crypto_set1 esp-aes 128 esp-sha-hmac
mode tunnel
exit
crypto map MAP1 1 ipsec-isakmp
set peer 180.1.100.21
set transform-set crypto_set1
set security-association lifetime seconds 28000
match address ipsec
exit

 Loading...
Loading...