Page 63 of 72
6 Network Services and Protocols
The table below lists the network services/protocols available on the ASR as a client (initiated outbound) and/or server (listening for
inbound connections), all of which run as system-level processes. The table indicates whether each service or protocol is allowed to
be used in the certified configuration.
For more detail about each service, including whether the service is limited by firewall mode (routed or transparent), or by context
(single, multiple, system), refer to Command Reference guides listed in Table 2.
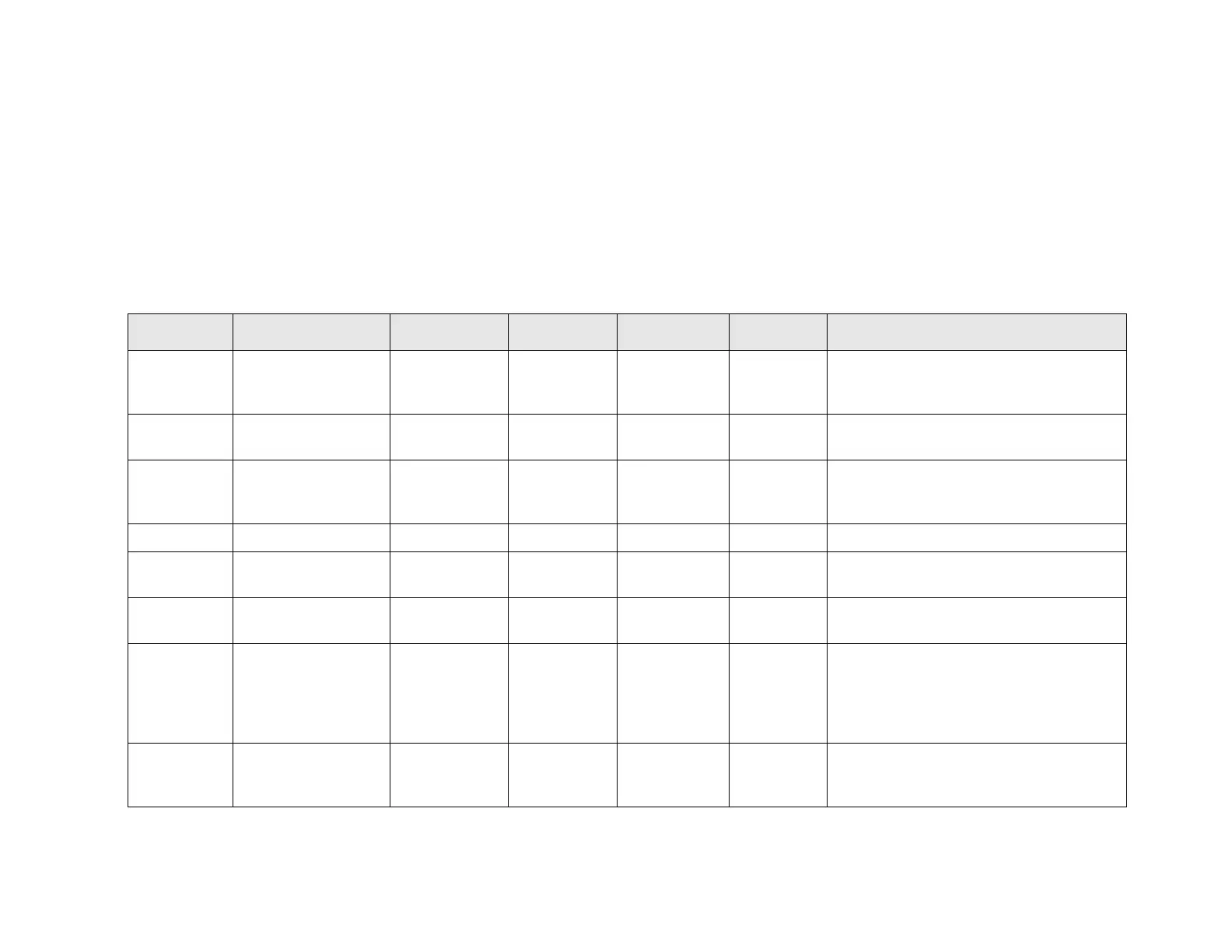
Table 9: Protocols and Services
Allowed use in the certified configuration
Dynamic Host
Configuration
Protocol
Encapsulating
Security Payload (part
of IPsec)
Configure ESP as described in the section
Error! Reference source not found.of this
document.
Use SCP or HTTPS instead.
Internet Control
Message Protocol
As described in section Error! Reference
source not found. of this document.
Internet Protocol
Security (suite of
protocols including
IKE, ESP and AH)
Only to be used for securing traffic that
originates from or terminates at the ASA, not
for “VPN Gateway” functionality to secure
traffic through the ASA. See IKE and ESP
for other usage restrictions.
A ticket-based
authentication
protocol
If used for authentication of ASA
administrators, tunnel this authentication
protocol secure with IPsec.

 Loading...
Loading...











