31
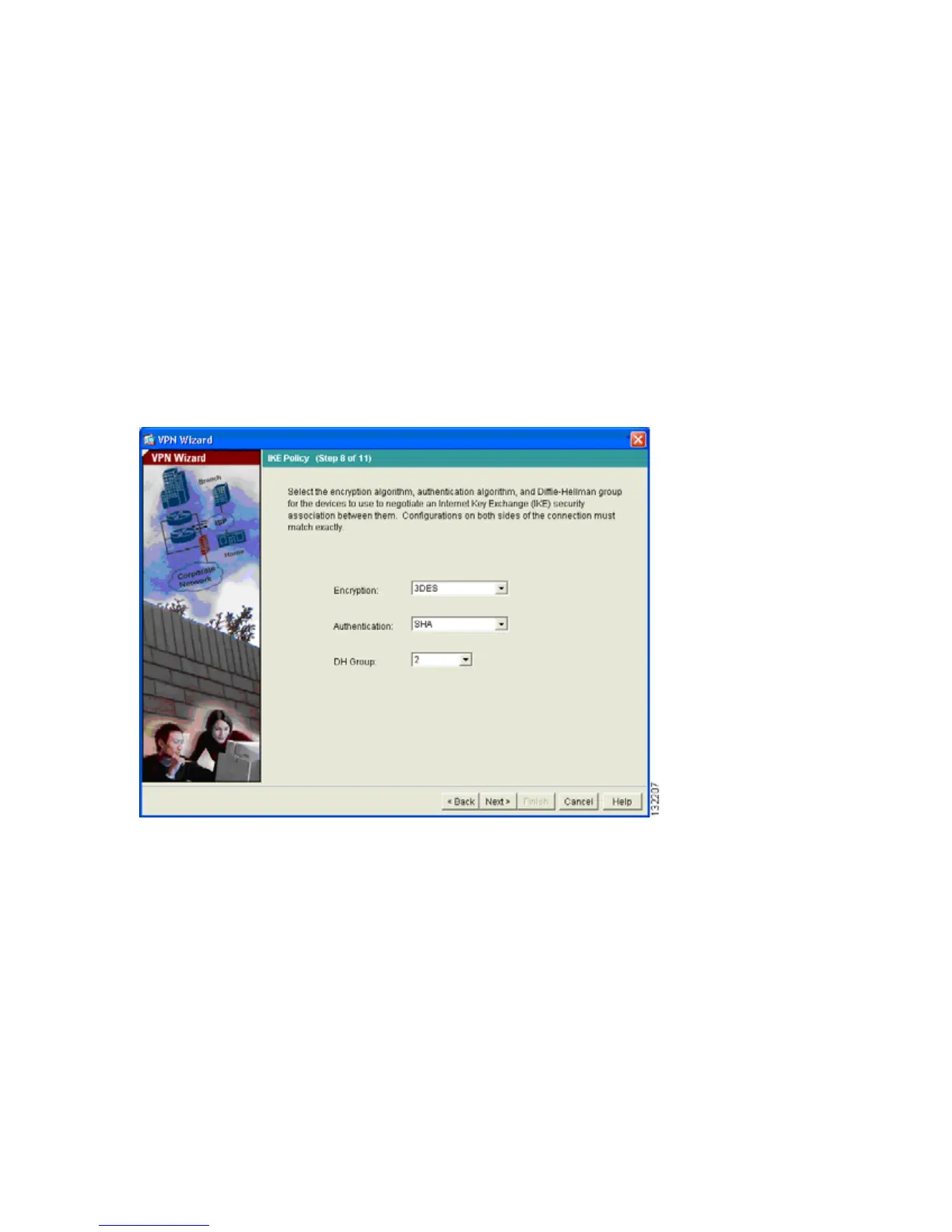
Step 8: Configure the IKE Policy.
IKE is a negotiation protocol that includes an encryption method to protect data and ensure privacy;
it is also an authentication method to ensure the identity of the peers. In most cases, the ASDM default
values are sufficient to establish secure VPN tunnels.
To specify the IKE policy, perform the following steps:
1. Select the Encryption (DES/3DES/AES), authentication algorithms (MD5/SHA), and the
Diffie-Hellman group (1/2/5/7) used by the adaptive security appliance during an IKE security
association.
2. Click Next to continue.
 Loading...
Loading...











