3-2
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 3 Access Control Lists
About ACLs
• Webtype ACLs—Webtype ACLs are used for filtering clientless SSL VPN traffic. These ACLs can
deny access based on URLs or destination addresses. See Configure Webtype ACLs, page 3-14.
• Standard ACLs—Standard ACLs identify traffic by destination address only. There are few features
that use them: route maps and VPN filters. Because VPN filters also allow extended access lists,
limit standard ACL use to route maps. See Configure Standard ACLs, page 3-13.
The following table lists some common uses for ACLs and the type to use.
ACL Names
Each ACL has a name or numeric ID, such as outside_in, OUTSIDE_IN, or 101. Limit the names to 241
characters or fewer.Consider using all uppercase letters to make it easier to find the name when viewing
a running configuration.
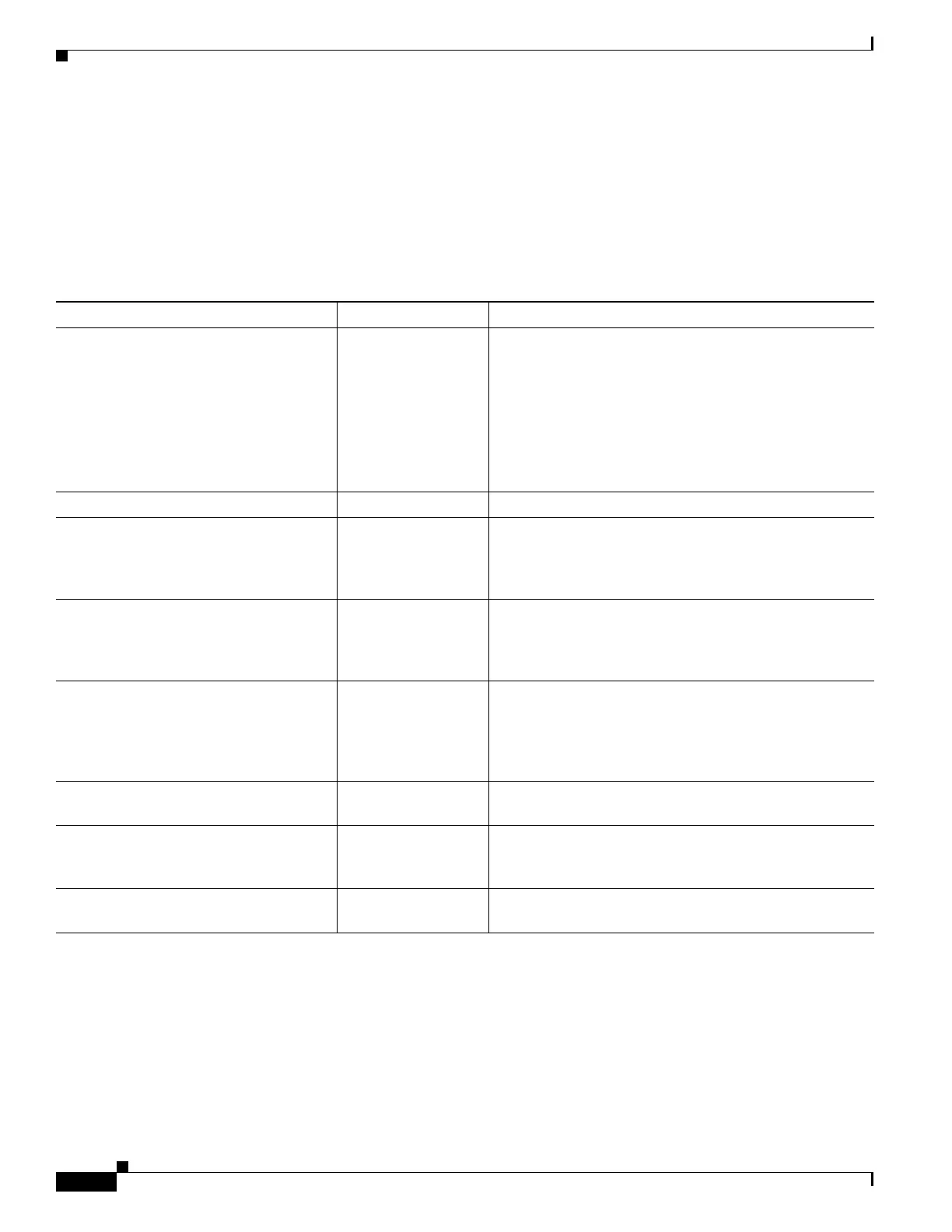
Table 3-1 ACL Types and Common Uses
ACL Use ACL Type Description
Control network access for IP traffic
(routed and transparent mode)
Extended The ASA does not allow any traffic from a lower security
interface to a higher security interface unless it is
explicitly permitted by an extended ACL.
Note To access the ASA interface for management
access, you do not also need an ACL allowing the
host IP address. You only need to configure
management access according to the general
operations configuration guide.
Identify traffic for AAA rules Extended AAA rules use ACLs to identify traffic.
Augment network access control for IP
traffic for a given user
Extended,
downloaded from a
AAA server per user
You can configure the RADIUS server to download a
dynamic ACL to be applied to the user, or the server can
send the name of an ACL that you already configured on
the ASA.
VPN access and filtering Extended
Standard
Group policies for remote access and site to site VPNs use
standard or extended ACLs for filtering. Remote access
VPNs also use extended ACLs for client firewall
configurations and dynamic access policies.
Identify traffic in a traffic class map for
Modular Policy Framework
Extended ACLs can be used to identify traffic in a class map, which
is used for features that support Modular Policy
Framework. Features that support Modular Policy
Framework include TCP and general connection settings,
and inspection.
For transparent firewall mode, control
network access for non-IP traffic
EtherType You can configure an ACL that controls traffic based on
its EtherType.
Identify route filtering and redistribution Standard
Extended
Various routing protocols use standard ACLs for route
filtering and redistribution (through route maps) for IPv4
addresses, and extended ACLs for IPv6.
Filtering for clientless SSL VPN Webtype You can configure a webtype ACL to filter URLs and
destinations.

 Loading...
Loading...











