4-2
TACACS+ Authentication
Configuring TACACS+ on the Switch
Overview
TACACS+ (Terminal Access Controller Access Control System+) authentica-
tion enables you to use a central server to allow or deny access to the switch
(and other TACACS-aware devices) in your network. This means that you can
use a central database to create multiple unique username/password sets with
associated privilege levels for use by individuals who have reason to access
the switch either locally (from the switch’s console port) or remotely (Telnet
or SSH).
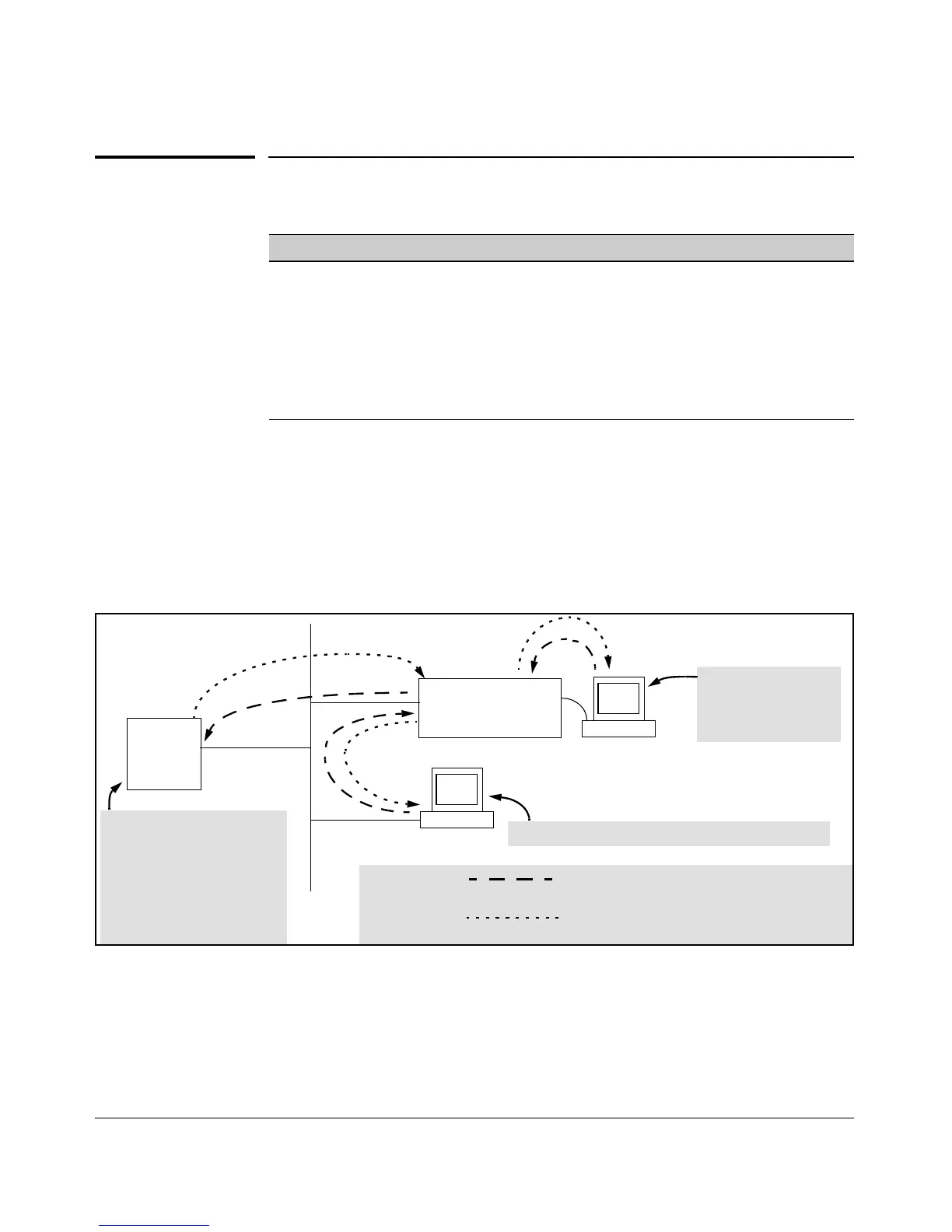
Figure 4-1. Example of TACACS+ Operation
TACACS+ in the switch manages authentication of logon attempts through
either the Console port or remote connection (Telnet, SSH). TACACS+ uses
an authentication hierarchy consisting of (1) remote passwords assigned in a
TACACS+ server and (2) local passwords configured on the switch. That is,
Feature Default Menu CLI Web
view the switch’s authentication configuration n/a — page 4-9 —
view the switch’s TACACS+ server contact
configuration
n/a — page
4-10
—
configure the switch’s authentication methods disabled — page
4-11
—
configure the switch to contact TACACS+ server(s) disabled — page
4-18
—
B
ProCurve Switch
Configured for
TACACS+ Operation
Terminal “A” Directly
Accessing the Switch
Via Switch’s Console
Port
Terminal “B” Remotely Accessing The Switch Via Telnet
A
Primary
TACACS+
Server
The switch passes the login
requests from terminals A and B
to the TACACS+ server for
authentication. The TACACS+
server determines whether to
allow access to the switch and
what privilege level to allow for
a given access request.
Access Request A1 - A4: Path for Request from
Terminal A (Through Console Port)
TACACS Server B1 - B4: Path for Request from
Response Terminal B (Through Telnet)
B1
A2 or
B2
A3 or
B3
B4
A1
A4
 Loading...
Loading...