8-11
Configuring Port-Based and Client-Based Access Control (802.1X)
General 802.1X Authenticator Operation
• If 802.1X (port-access) on the switch is configured for local authenti-
cation, then:
i. The switch compares the client’s credentials with the username
and password configured in the switch (Operator or Manager
level).
ii. If the client is successfully authenticated and authorized to con-
nect to the network, then the switch allows access to the client.
Otherwise, access is denied and the port remains blocked.
Switch-Port Supplicant Operation
This operation provides security on links between 802.1X-aware switches. For
example, suppose that you want to connect two switches, where:
■ Switch “A” has port A1 configured for 802.1X supplicant operation.
■ You want to connect port A1 on switch “A” to port B5 on switch “B”.
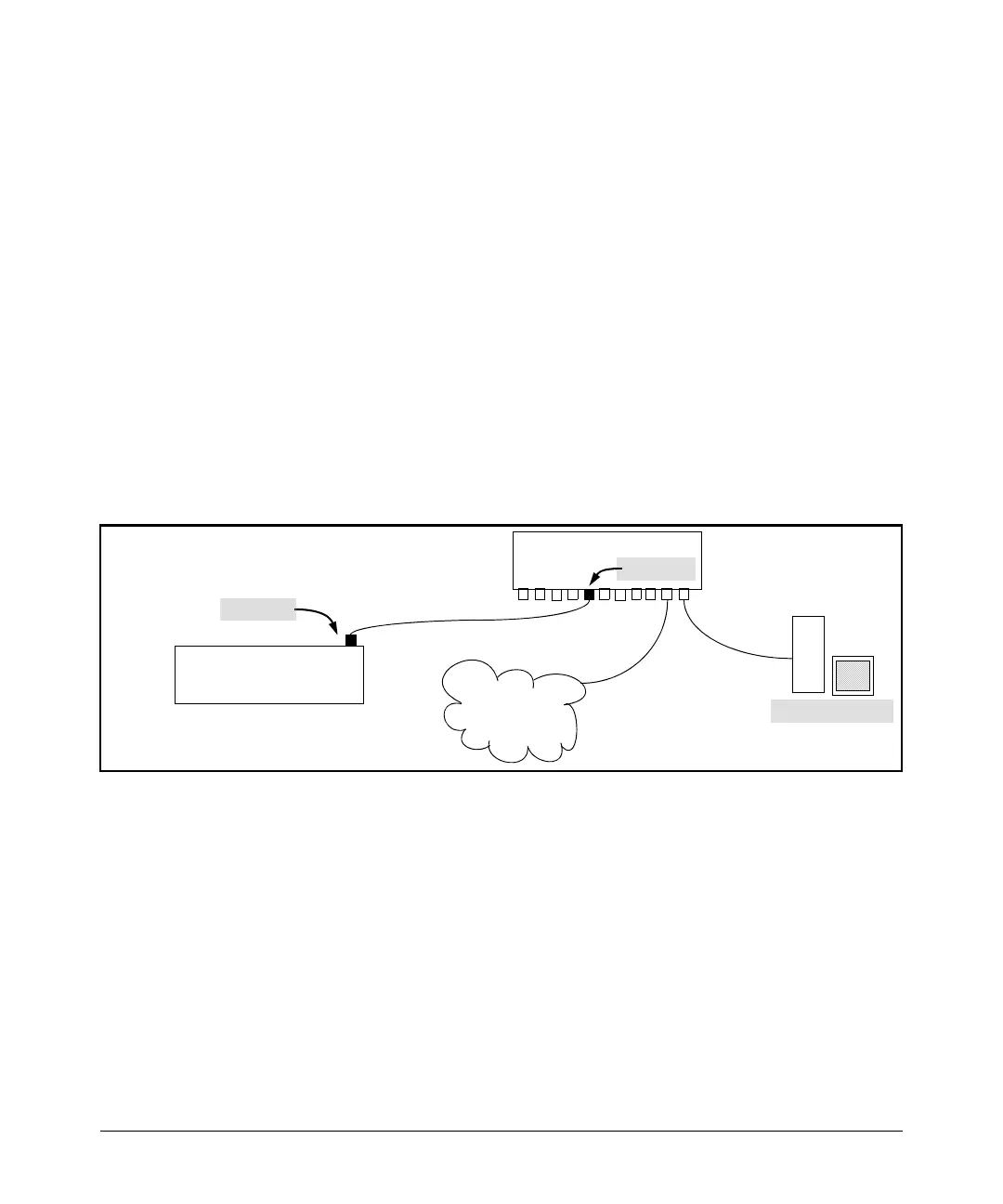
Figure 8-2. Example of Supplicant Operation
1. When port A1 on switch “A” is first connected to a port on switch “B”, or
if the ports are already connected and either switch reboots, port A1
begins sending start packets to port B5 on switch “B”.
• If, after the supplicant port sends the configured number of start
packets, it does not receive a response, it assumes that switch “B” is
not 802.1X-aware, and transitions to the authenticated state. If switch
“B” is operating properly and is not 802.1X-aware, then the link should
begin functioning normally, but without 802.1X security.
• If, after sending one or more start packets, port A1 receives a request
packet from port B5, then switch “B” is operating as an 802.1X
authenticator. The supplicant port then sends a response/ID packet.
Switch “B” forwards this request to a RADIUS server.
RADIUS Server
Switch “A”
Port A1 Configured as an
802.1X Supplicant
Port A1
Switch “B”
Port B5
LAN Core

 Loading...
Loading...











