16
GENERAL
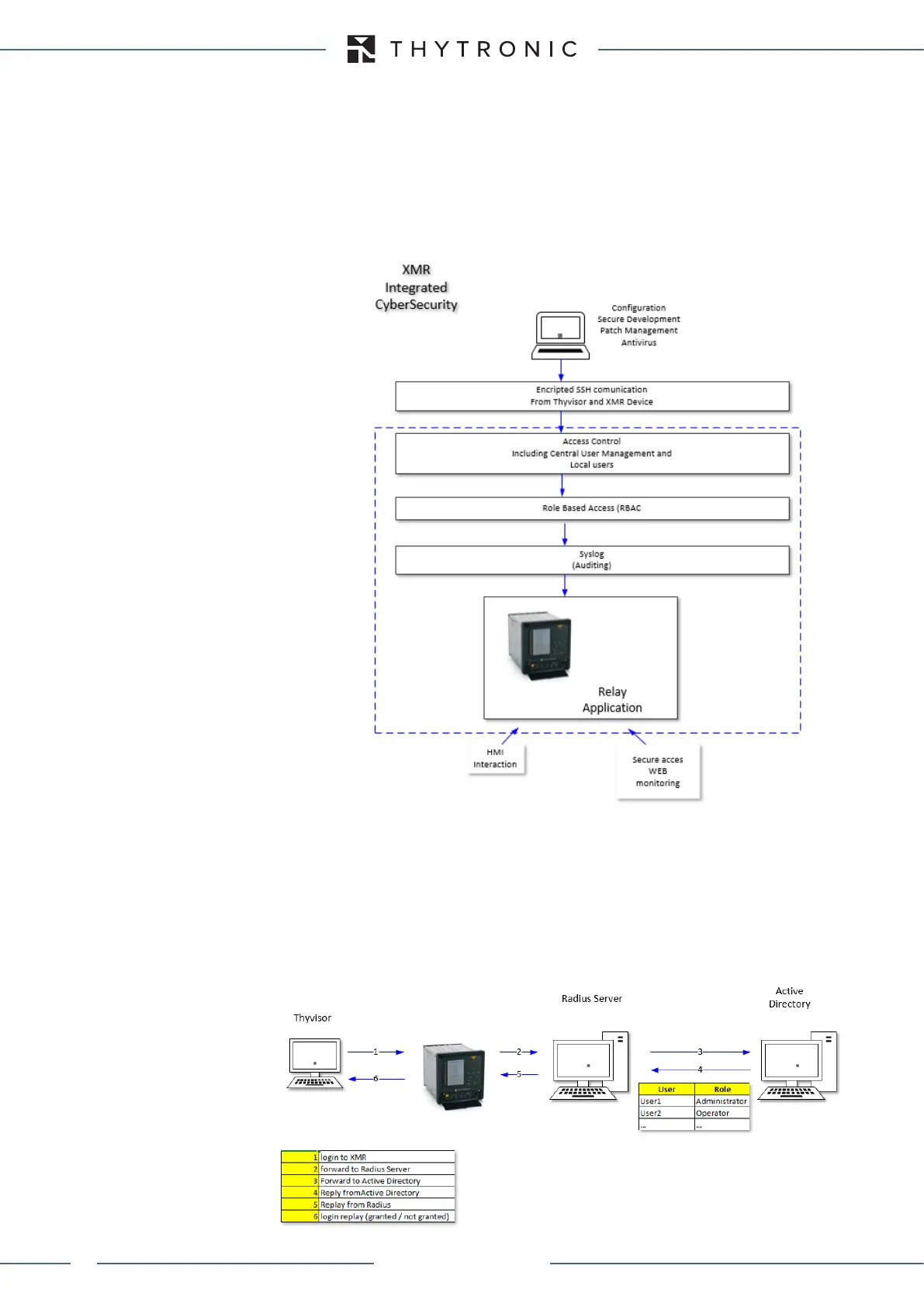
XMR Cybersecurity basic scheme
XMR protection relay configuration capabilities and monitoring functionalities set problems related
to the security and privacy of the data traffic exchanged between equipment and remote control
centre.
The aspects to consider in this regard are:
• Traffic encryption, so it cannot be intercepted, analysed and eventually modified freely by third
parties
• Authentication mechanism implementation in order to prevent any third parties false messages
generation avoiding that they can be recognized as valid
User access procedure
Authentication mechanism expects to send authentication requests coming inbound card to a
remote RADIUS authentication server that takes care user validation and it sends to CPU unit a
positive or negative feedback based on the fact that the credentials provided by the user are
correct or not and relevant associated user privilege level information
The RADIUS authentication as a reference to a remote server and uses a shared secret between
card and server for validation of access requests. The configurator provides the possibility to define
all parameters necessary for this authentication mode.
XMR-D EQUIPMENT MANUAL
Ed. 2.9 - 02/2021

 Loading...
Loading...