
 Loading...
Loading...
Do you have a question about the TP-Link SafeStream TL-ER6020 and is the answer not in the manual?
| Ethernet LAN | Yes |
|---|---|
| Cabling technology | 10/100/1000Base-T(X) |
| Networking standards | IEEE 802.3, IEEE 802.3ab, IEEE 802.3u |
| VPN tunnels quantity | 50 |
| Ethernet LAN data rates | 10, 100, 1000 Mbit/s |
| Ethernet LAN interface type | Gigabit Ethernet |
| Maximum indoor range | 100 m |
| RS-232 ports | 1 |
| Ethernet LAN (RJ-45) ports | 3 |
| Form factor | 1U |
| USB ports quantity | 0 |
| Management platform | Web/CLI/Telnet |
| Filtering description | MAC, URL/Keywords, WebContent |
| Compatible operating systems | Microsoft Windows 98SE, NT, 2000, XP, Vista, Windows 7\\r MAC OS\\r NetWare, UNIX, Linux |
| Routing protocols | RIP-1, RIP-2 |
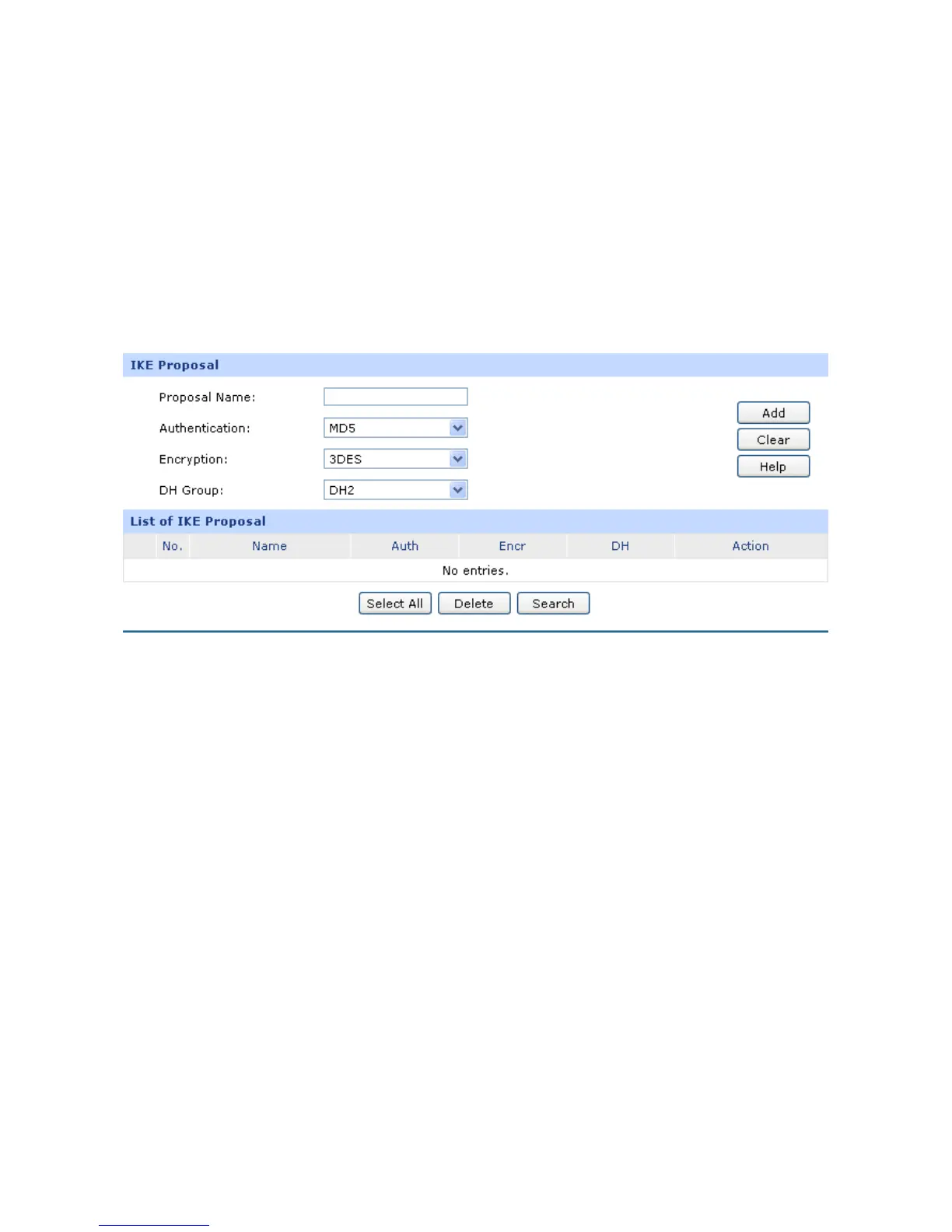
| Supported protocols | IPsec/PPTP/L2TP |
| Supported network protocols | TCP/IP, DHCP, ICMP, NAT, PPPoE, SNTP, HTTP, DNS, IPsec, PPTP, L2TP |
| VPN support | 50 IPsec VPN Tunnels LAN-to-LAN, Client-to-LAN Main, Aggressive Negotiation Mode DES, 3DES, AES128, AES192, AES256 Encryption Algorithm MD5, SHA1 Authentication Algorithm IPsec NAT Traversal (NAT-T) Dead Peer Detection (DPD) Perfect Forward Secrecy (PFS) 16 PPTP VPN Tunnels PPTP VPN Server/Client PPTP with MPPE Encryption 16 L2TP VPN Tunnels L2TP VPN Server/Client L2TP over IPsec |
| NAT functionality | One-to-One NAT\\r Multi-nets NAT\\r Virtual Server, DMZ Host, Port_Triggering, UPnP\\r FTP/H.323/SIP/IPsec/PPTP ALG |
| Security algorithms | 128-bit AES, 256-bit AES, 3DES, DES |
| Authentication method | MD5, SHA-1 |
| Network Address Translation (NAT) sessions (max) | 30000 |
| Flash memory | 16 MB |
| Certification | CE, FCC, RoHS |
| Internal memory | 128 MB |
| Internal memory type | DDR2 |
| Mac operating systems supported | macOS |
| Windows operating systems supported | Windows 10, Windows 2000, Windows 7, Windows 8, Windows 8.1, Windows 98SE, Windows NT, Windows Vista, Windows XP |
| AC input voltage | 100 - 240 V |
| Power source type | AC |
| AC input frequency | 50 - 60 Hz |
| Power over Ethernet (PoE) | No |
| Power consumption (typical) | - W |
| Storage temperature (T-T) | -40 - 70 °C |
| Operating temperature (T-T) | 0 - 40 °C |
| Storage relative humidity (H-H) | 5 - 90 % |
| Operating relative humidity (H-H) | 10 - 90 % |
| Product color | Black |
| Sustainability certificates | RoHS |
| Package depth | 250 mm |
| Package width | 400 mm |
| Package height | 80 mm |
| Package weight | 1810 g |
| Depth | 180 mm |
|---|---|
| Width | 294 mm |
| Height | 44 mm |
| Weight | - g |











