Chapter 13. Encryption 793
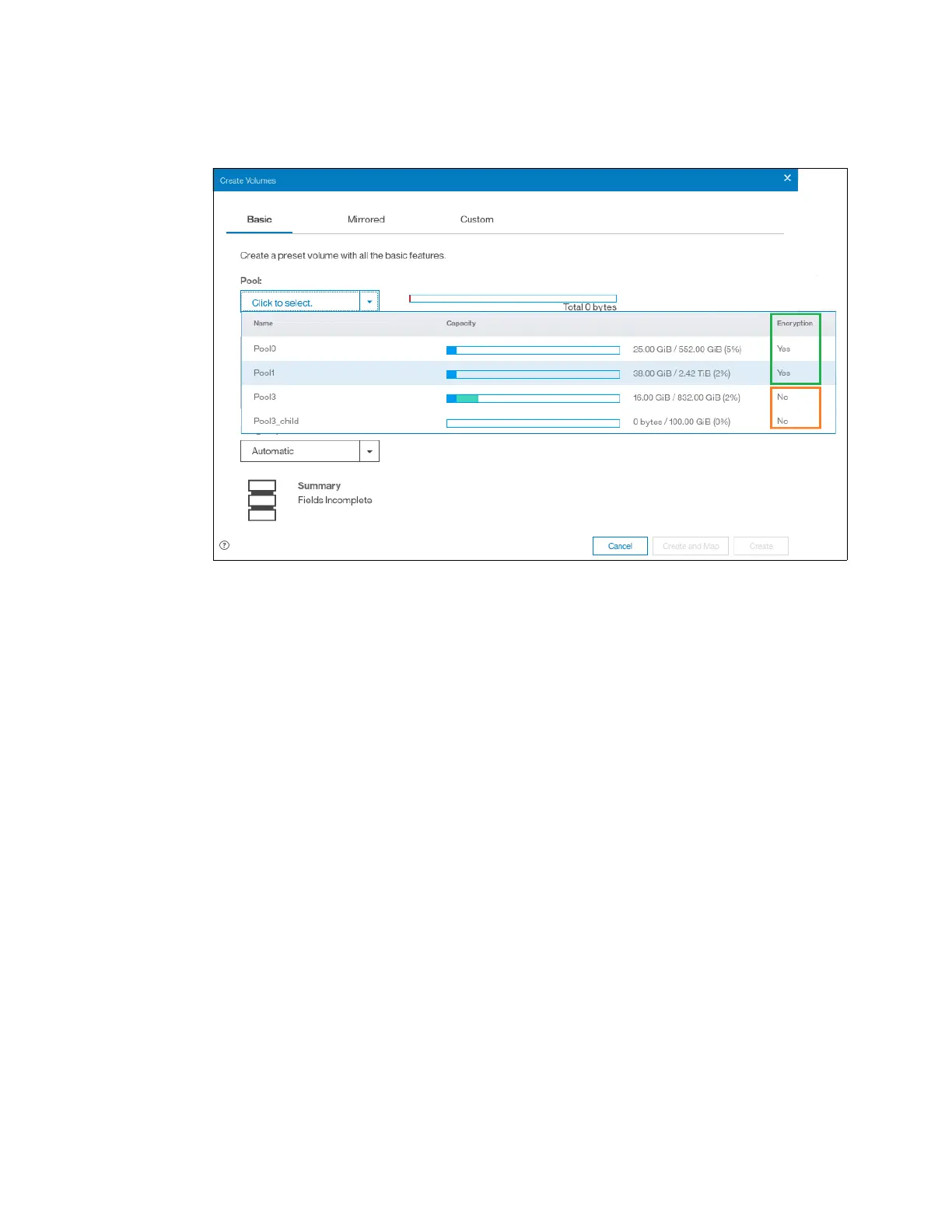
When creating volumes make sure to select encrypted pools to create encrypted volumes, as
shown in Figure 13-73.
Figure 13-73 Create an encrypted volume by selecting an encrypted pool
You cannot change an existing unencrypted volume to an encrypted version of itself
dynamically. However, this conversion is possible by using two migration options:
Migrate a volume to an encrypted pool or child pool.
Mirror a volume to an encrypted pool or child pool and delete the unencrypted copy.
For more information about either method, see Chapter 6, “Volume configuration” on
page 287.
13.8.6 Restrictions
The following restrictions apply to encryption:
Image mode volumes cannot be in encrypted pools.
You cannot add external non self-encrypting MDisks to encrypted pools unless all nodes
in the cluster support encryption.
Nodes that cannot perform software encryption cannot be added to systems with
encrypted pools that contain external MDisks that are not self-encrypting.
13.9 Rekeying an encryption-enabled system
Changing the master access key is a security requirement. Rekeying is the process of
replacing current master access key with a newly generated one. The rekey operation works
whether or not encrypted objects already exist. The rekeying operation requires access to a
valid copy of the original master access key on an encryption key provider which you plan to
rekey. Use the rekey operation according to the schedule defined in your organization’s
security policy and whenever you suspect that the key might have been compromised.
 Loading...
Loading...











