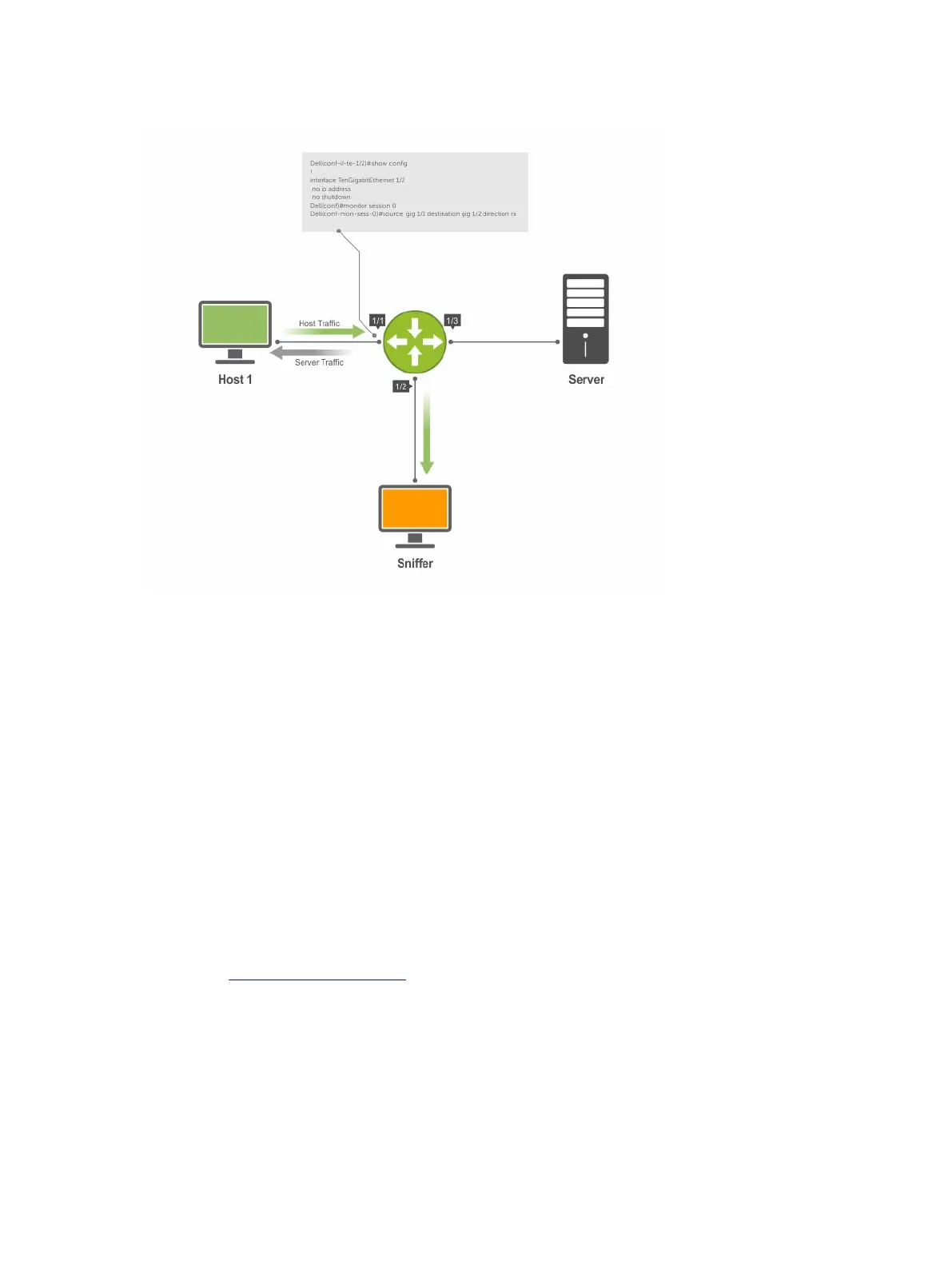
Figure 100. Port Monitoring Example
Enabling Flow-Based Monitoring
Flow-based monitoring is supported only on the S-Series platform.
Flow-based monitoring conserves bandwidth by monitoring only specified traffic instead of all traffic on
the interface. This feature is particularly useful when looking for malicious traffic. It is available for Layer 2
and Layer 3 ingress and egress traffic. You can specify traffic using standard or extended access-lists.
1. Enable flow-based monitoring for a monitoring session.
MONITOR SESSION mode
flow-based enable
2. Define in access-list rules that include the keyword monitor. For port monitoring, Dell Networking
OS only considers traffic matching rules with the keyword
monitor.
CONFIGURATION mode
ip access-list
Refer to Access Control Lists (ACLs).
3. Apply the ACL to the monitored port.
INTERFACE mode
ip access-group access-list
756
Port Monitoring
 Loading...
Loading...











