7
COMMUNICATION USING BUILT-IN ETHERNET
PORTS OF CPU MODULE
7.7 Remote Password
7 - 47
1
Overview
2
Performance
Specification
3
Sequence Program
Configuration and
Execution Conditions
4
I/O Nunber Assignment
5
Memories and Files
Handled by CPU Module
6
Functions
7
Communication using
built-in Ethernet ports of
CPU module
8
Communication with
Intelligent Function
Module
(b) Enabling parameter settings
After writing parameter settings to the CPU module, settings are enabled by
powering the programmable controller ON or resetting the CPU module.
(c) Performing remote password unlock/lock processing
Perform the remote password unlock/lock processing from an external device
using respective protocol as follows.
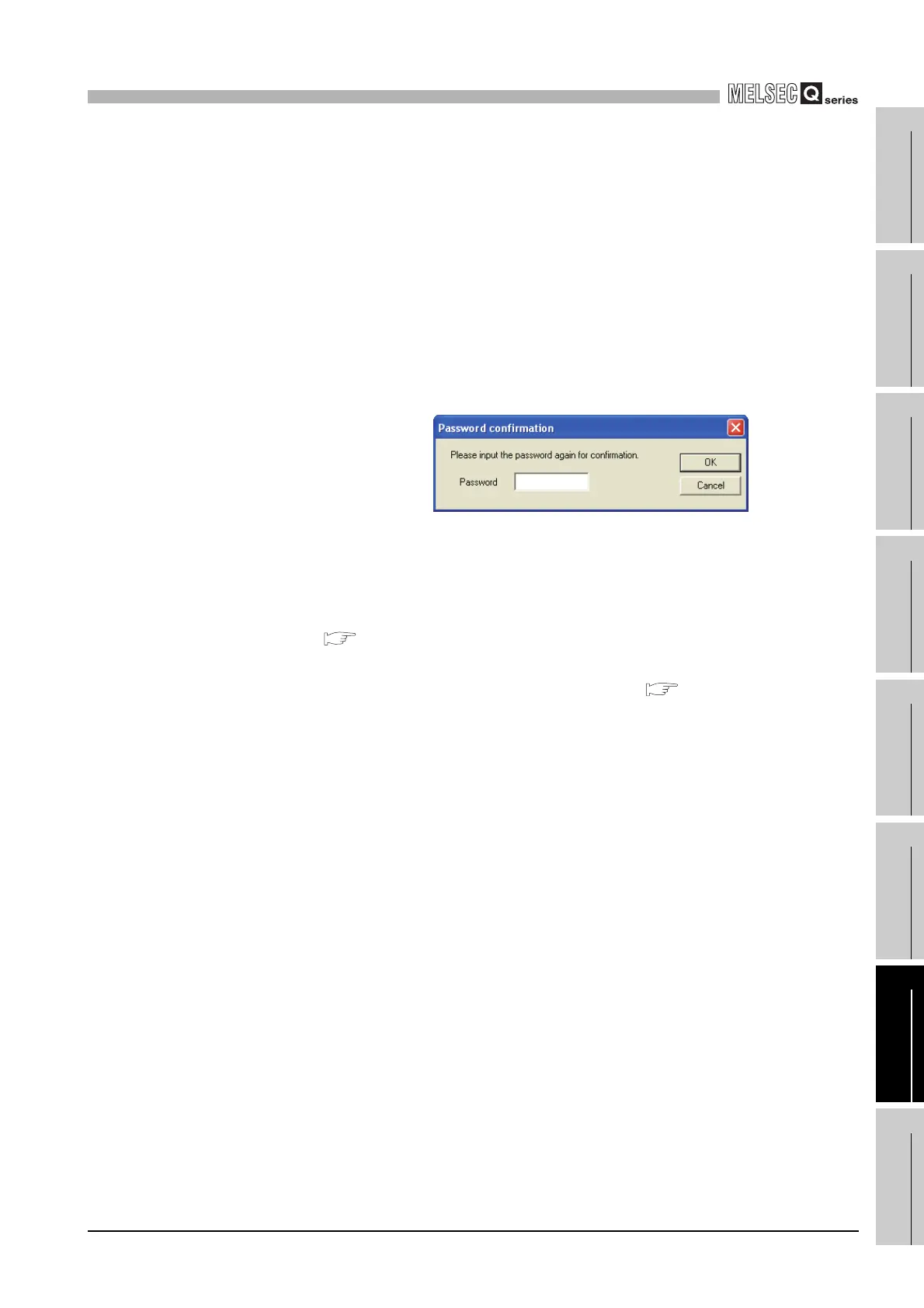
1) Using MELSOFT connection
Enter the remote password in the following dialog box that appears during
communication.
GX Developer performs unlock processing upon entering the remote
password and then access the CPU module.
2) Using MC protocol
Use the dedicated commands for the MC protocol.
For details on the MC protocol dedicated commands, refer to the following
manual.
Q Corresponding MELSEC Communication Protocol Reference Manual
3) Using file transfer (FTP server) function
Use the "password-lock"/"unlock" commands. ( Section 7.6 (5))
(3) Precautions for remote password
Precautions for the remote password check function are described below.
(a) Setting remote password to UDP connections
• Determine the communication target external device and do not
communicate with unspecified external devices. (The communication target
external device needs to be determined since UDP/IP connections can
communicate with any other devices, including the device that has performed
unlock processing, after the remote password unlocking processing is
completed normally.)
• At the end of data communication, always perform the remote password lock
processing. (If lock processing is not performed, unlock status is held until a
time-out occurs. When there is no communication for 10 minutes, the CPU
module automatically performs time-out based lock processing.)
To prevent unauthorized access more strictly using the remote password, it is
recommended to set all connection protocols to TCP/IP and disable GX
Developer direct connection in parameter.
(b) Performing close processing before lock processing for TCP/IP
connections
When close processing is performed before lock processing for TCP/IP
connections, the CPU module automatically performs lock processing.
Figure 7.30 Password confirmation screen

 Loading...
Loading...











