2-21
Configuring Username and Password Security
Saving Security Credentials in a Config File
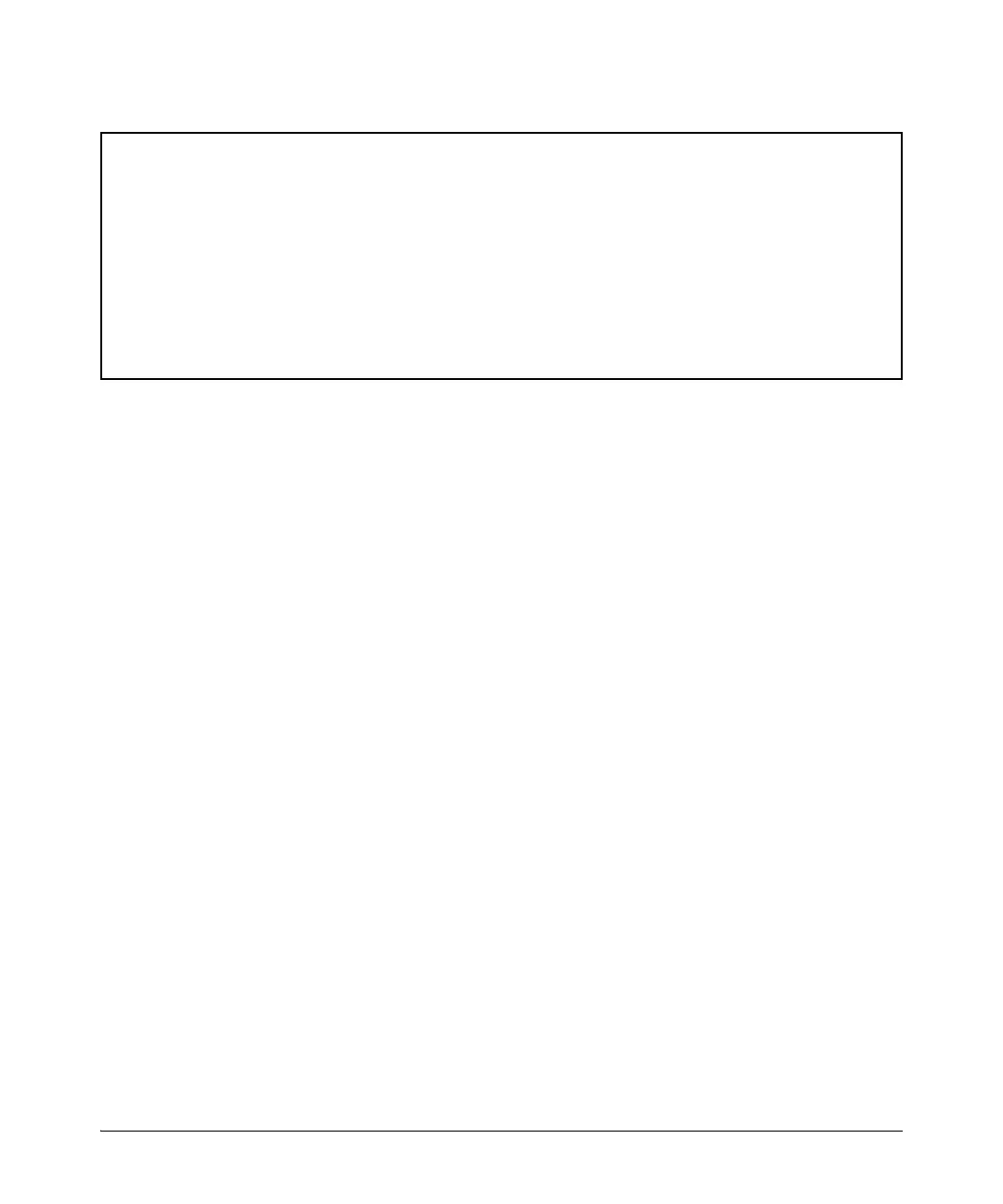
Figure 2-8. Example of Caution Message Displayed for radius-tacacs-only Option
SSH Client Public-Key Authentication
Secure Shell version 2 (SSHv2) is used by HP switches to provide remote
access to SSH-enabled management stations. Although SSH provides Telnet-
like functions, unlike Telnet, SSH provides encrypted, two-way authenticated
transactions. SSH client public-key authentication is one of the types of
authentication used.
Client public-key authentication uses one or more public keys (from clients)
that must be stored on the switch. Only a client with a private key that matches
a public key stored on the switch can gain access at the manager or operator
level. For more information about how to configure and use SSH public keys
to authenticate SSH clients that try to connect to the switch, refer to
“Configuring Secure Shell (SSH)” on page 8-1 in this guide.
The SSH security credential that is stored in the running configuration file is
configured with the ip ssh public-key command used to authenticate SSH
clients for manager or operator access, along with the hashed content of each
SSH client public-key.
HP Switch(config)# include-credentials radius-tacacs-only
**** CAUTION ****
This will insert possibly sensitive information in switch configuration files,
and as a part of some CLI commands output. It is strongly recommended that you
use SFTP rather than TFTP for transfer of the configuration over the network,
and that you use the web configuration interface only with SSL enabled.
Erasing configurations with ‘include-credentials’ enabled will erase stored
passwords and security credentials. The system will reboot with the factory
default configuration.
Syntax: ip ssh public-key <manager |operator> keystring
Set a key for public-key authentication.
manager: allows manager-level access using SSH public-key
authentication.
operator: allows operator-level access using SSH public-key
authentication.

 Loading...
Loading...











