The administrator can limit devices or protocols that can be connected to the machine to avoid unintended access.
Also, the administrator can select a security level at which to enable or disable a protocol and to configure the port
status.
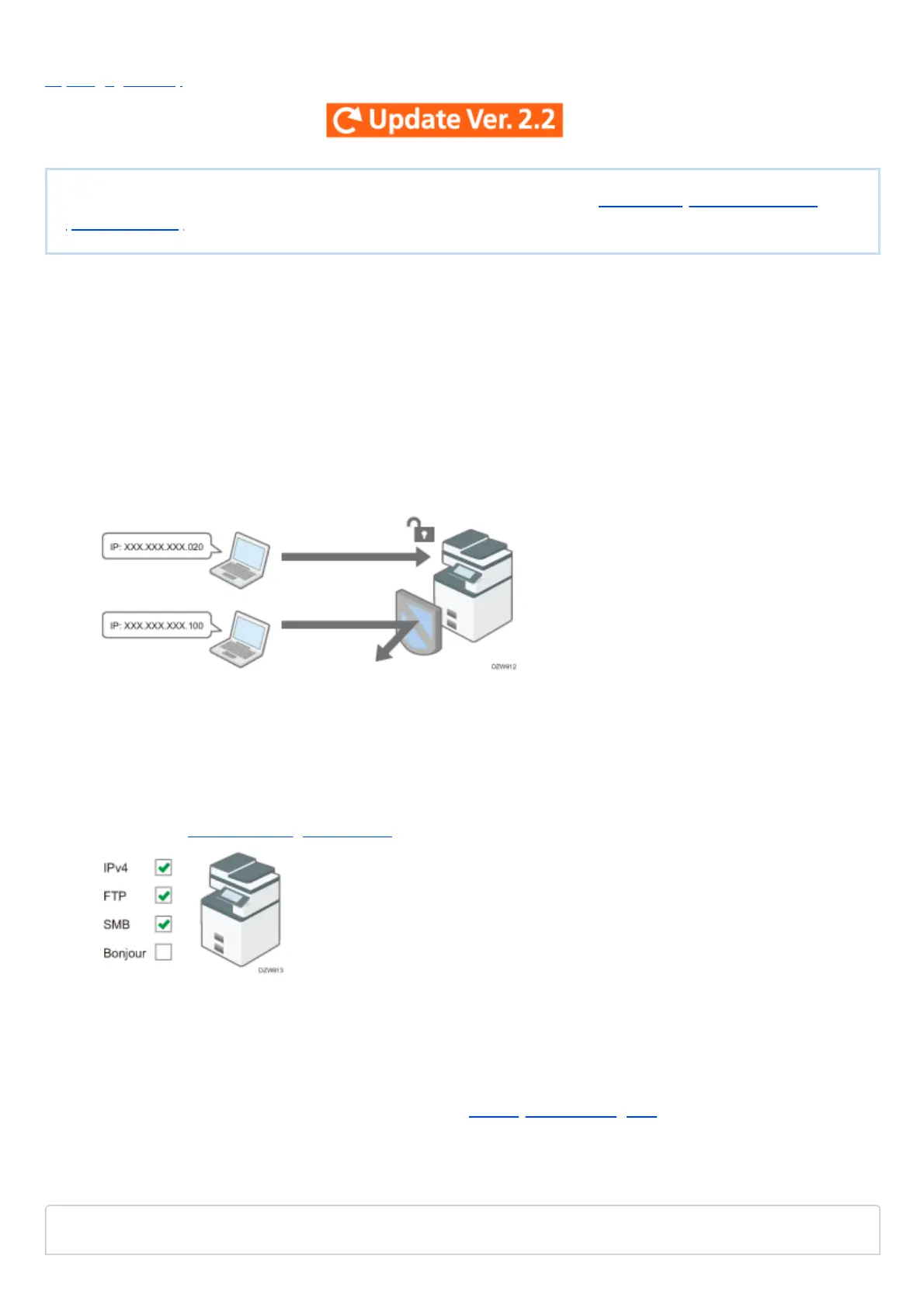
Limiting the IP addresses from which devices can access the
machine (access control)
For example, when specifying the range of IP address from "192.168.15.1" to "192.168.15.99", the machine
cannot be accessed from IP addresses in the range from 192.168.15.100 to 255.
Disabling unused protocols
The protocol setting can be changed on the control panel, in Web Image Monitor, or by using other setting
methods. The protocols that can be configured vary depending on the method. Confirm the protocol to
configure in Protocol Setting Method List and follow the instruction.
Specifying the security level
You can select from among four security levels combining different protocols, ports, and encryption
algorithms. Confirm the description of each level in Security Level Setting List.
You can customize the security setting based on the selected level setting to suit your condition.
 Loading...
Loading...