IEC12000210 V2 EN-US
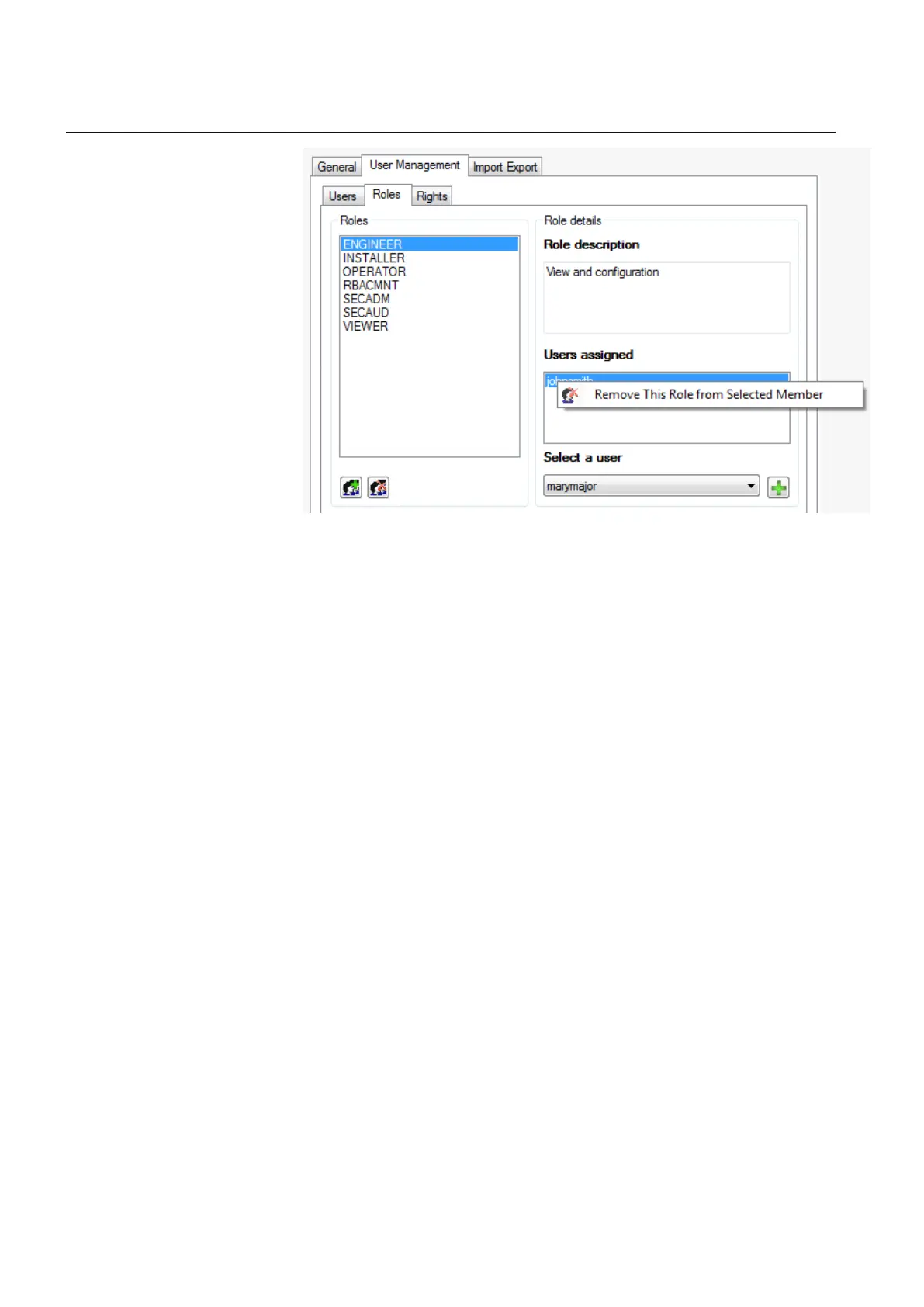
Figure 18: Remove Role from User
4.4.4.3 Reusing user accounts
GUID-C28C87EC-7027-440C-BB38-2C8EC14ECA40 v2
IED user account data can be exported from one IED and imported to another. The
data is stored in an encrypted file.
Exported passwords are hashed and not in clear text.
To export IED user account data from an IED
1. Click the Import Export tab in the IED User tool in PCM600.
2. Click Export IED account data.
The user account data is exported to a file with user defined filename and location.
Import IED user rights to an IED
1. Click Import IED account data.
2. Open the previously exported file.
Only users who have the right to change the user account data in PCM600 are
allowed to export and import.
Section 4 1MRK 511 399-UEN B
Local user account management
38 670 series 2.2 IEC
Cyber security deployment guideline