User Manual of Network Fisheye Camera
70
Surveillance Center, Send Email, Upload to FTP, Trigger Channel and Trigger
Alarm Output.
11. Click Save to save the settings.
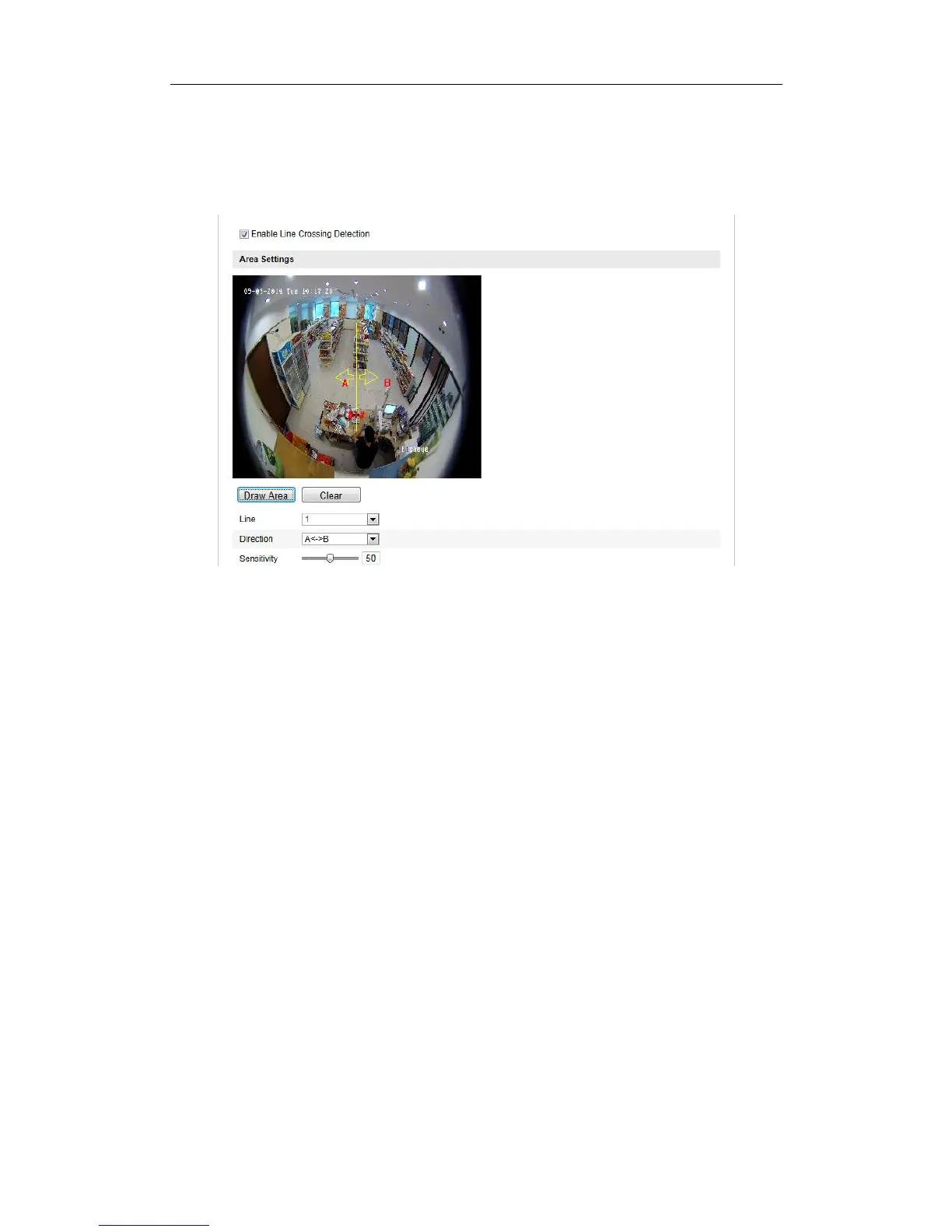
Figure 5-49 Line Crossing Detection Settings
5.6.7 Configuring Intrusion Detection
Purpose:
Intrusion detection function detects people, vehicle or other objects which enter and
loiter in a pre-defined virtual region, and some certain actions can be taken when the
alarm is triggered.
Steps:
1. Enter the Intrusion Detection settings interface:
Configuration > Advanced Configuration > Events > Intrusion Detection
2. Check the checkbox of Enable Intrusion Detection to enable the function.
3. Click the Draw Area button to start the region drawing.
4. Click on the live video to specify the four vertexes of the detection region, and
right click to complete drawing.
5. Set the time threshold, detection sensitivity and object percentage for intrusion

 Loading...
Loading...











