7-33
Configuring RADIUS Server Support for Switch Services
Configuring and Using Dynamic (RADIUS-Assigned) Access Control Lists
• Permit http (TCP port 80) traffic from the client to the device at
10.10.10.117.
• Deny http (TCP port 80) traffic from the client to all other IPv4
addresses.
• Deny Telnet (TCP port 23) traffic from the client to any IPv4 address.
• Permit all other IPv4 traffic from the client to all other devices.
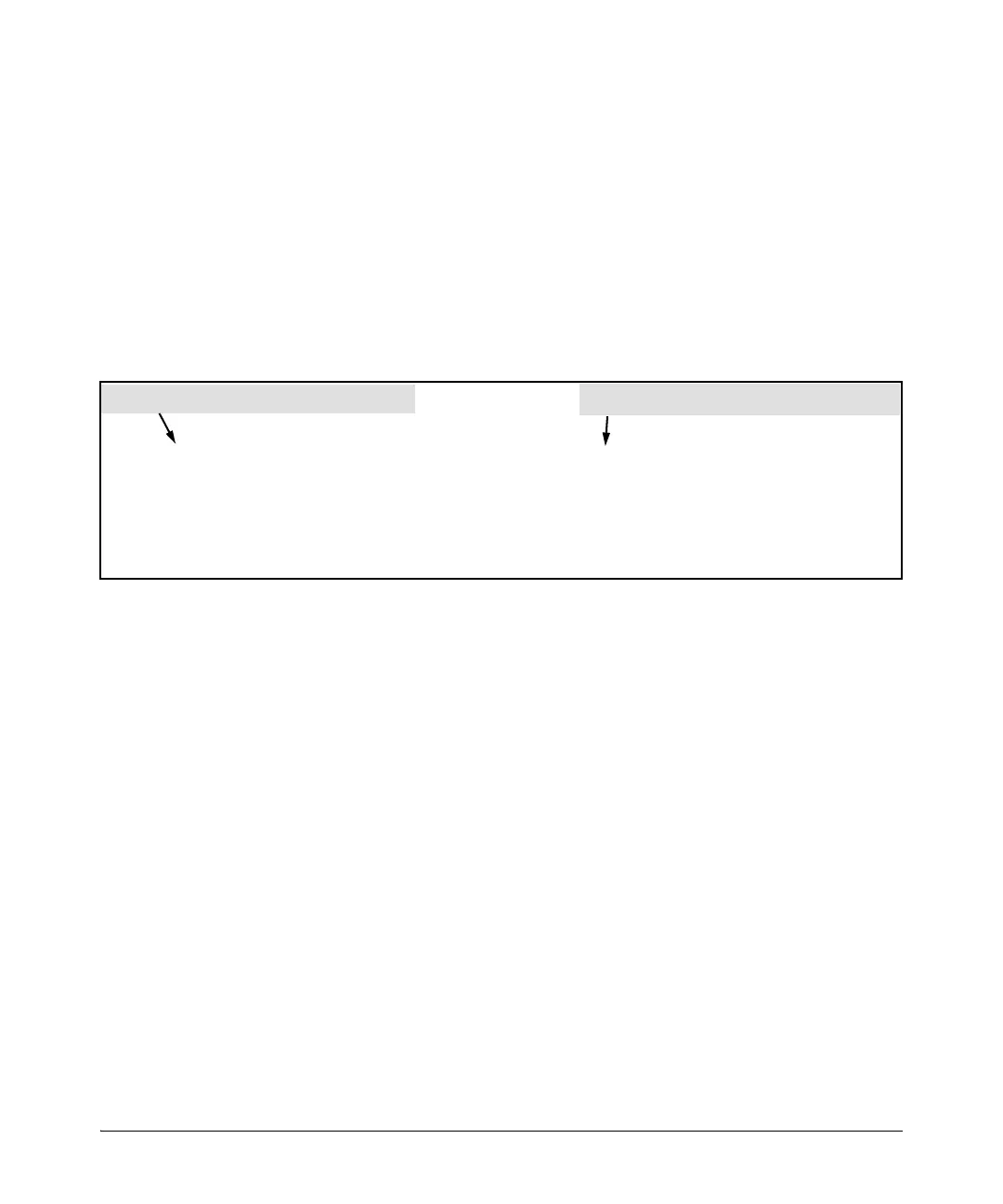
To configure the above ACL, you would enter the username/password and
ACE information shown in figure 7-11 into the FreeRADIUS “users” file.
Figure 7-11. Example of Configuring a FreeRADIUS Server To Filter IPv4 Traffic for a Client Using the Correct
Username and Password Credentials.
User-10 Auth-Type:= Local, User-Password == auth7X
HP-Nas-Rules-IPv6 = 1,
HP-Nas-filter-Rule = “permit in tcp from any to 10.10.10.117 80”,
HP-Nas-filter-Rule += “deny in tcp from any to any 80”,
HP-Nas-filter-Rule += “deny in tcp from any to any 23”,
HP-Nas-filter-Rule += “permit in ip from any to any”
Client’s Username (802.1X or Web Authentication)
Client’s Password (802.1X or Web Authentication)
 Loading...
Loading...











