10-124
IPv4 Access Control Lists (ACLs)
Enable ACL “Deny” Logging
has multiple assignments as an RACL, then a match with an ACE in any RACL
instance of the ACL increments that same counter on all RACL-assigned
instances of that ACL. (The ACE counters for VACL and PACL instances of an
ACL are not affected by counter activity in RACL instances of the same ACL.)
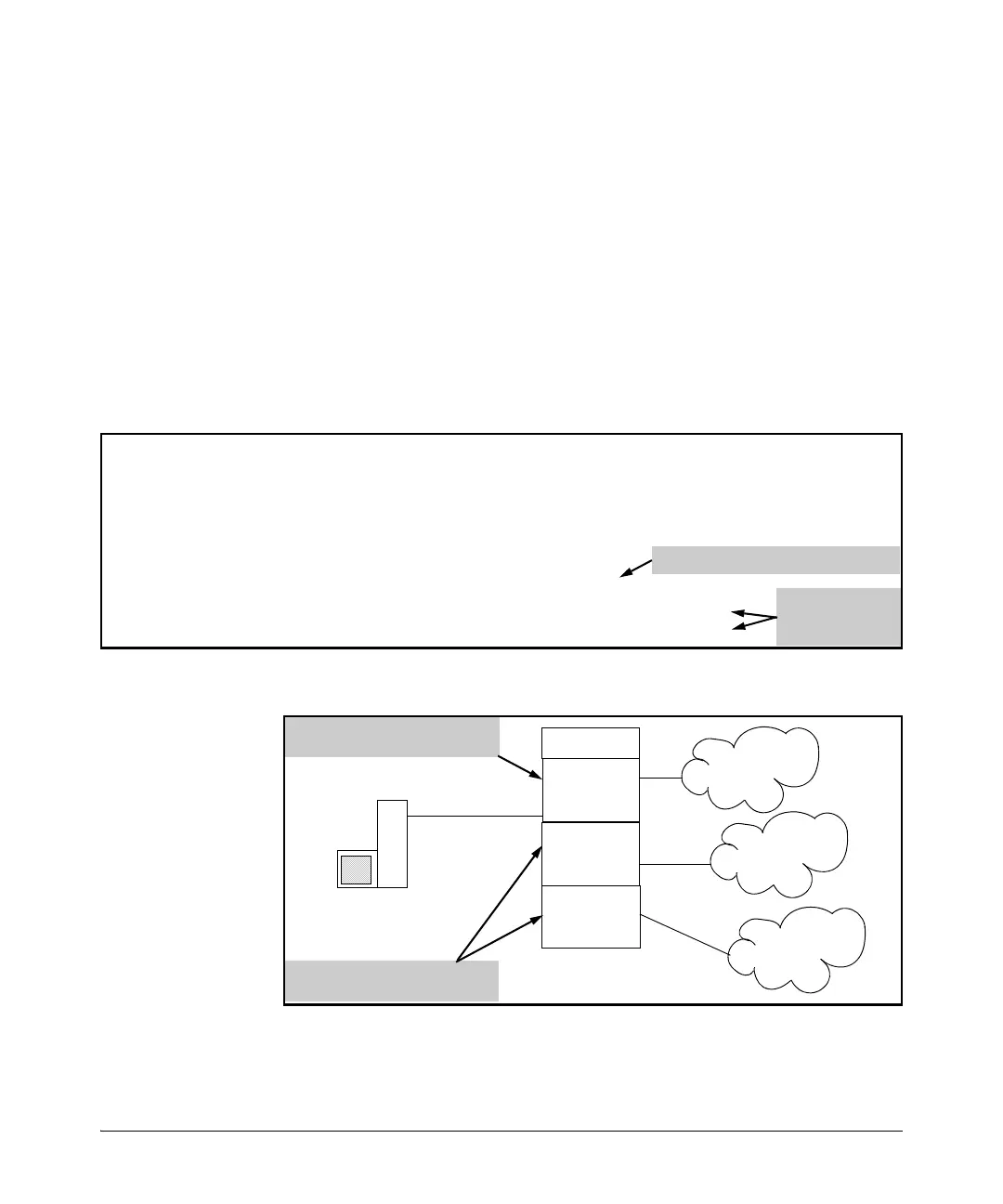
For example, suppose that an IPv4 ACL named “Test-1” is configured as shown
in figure 10-54 to block Telnet access to a server at 10.10.20.12 on VLAN 20,
and that the Test-1 ACL is assigned to VLANs as follows:
■ VLAN 20: VACL
■ VLAN 50: RACL
■ VLAN 70: RACL
Figure 10-54. ACL “Test-1” and Interface Assignment Commands
Figure 10-55. Example of Using the Same ACL for VACL and RACL Applications
HP Switch(config)# show access-list config
ip access-list extended “Test1”
10 deny tcp 0.0.0.0 255.255.255.255 10.10.20.12 0.0.0.0 eq 23 log
20 permit ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
exit
HP Switch(config)# vlan 20 ip access-group Test-1 vlan
HP Switch(config)# vlan 50 ip access-group Test-1 in
HP Switch(config)# vlan 70 ip access-group Test-1 in
Assigns the ACL as a VACL to VLAN 20.
Assigns the ACL as
an RACL to VLANs
50 and 70.
VLAN 20
10.10.20.1
VLAN 50
10.10.55.1
5400zl Switch
1
0
.
1
0
.
2
0
.
0
1
0
.
1
0
.
3
0
.
0
10.10.20.12
ACL “Test-1” assigned as an RACL
to both VLAN 50 and VLAN 70.
VLAN 70
10.10.70.1
1
0
.
1
0
.
7
0
.
0
ACL “Test-1” assigned as a VACL
to VLAN 20.
 Loading...
Loading...











