3-3
Virus Throttling (Connection-Rate Filtering)
Overview of Connection-Rate Filtering
Note When configured on a port, connection-rate filtering is triggered by IPv4
traffic received inbound with a relatively high rate of IP connection attempts.
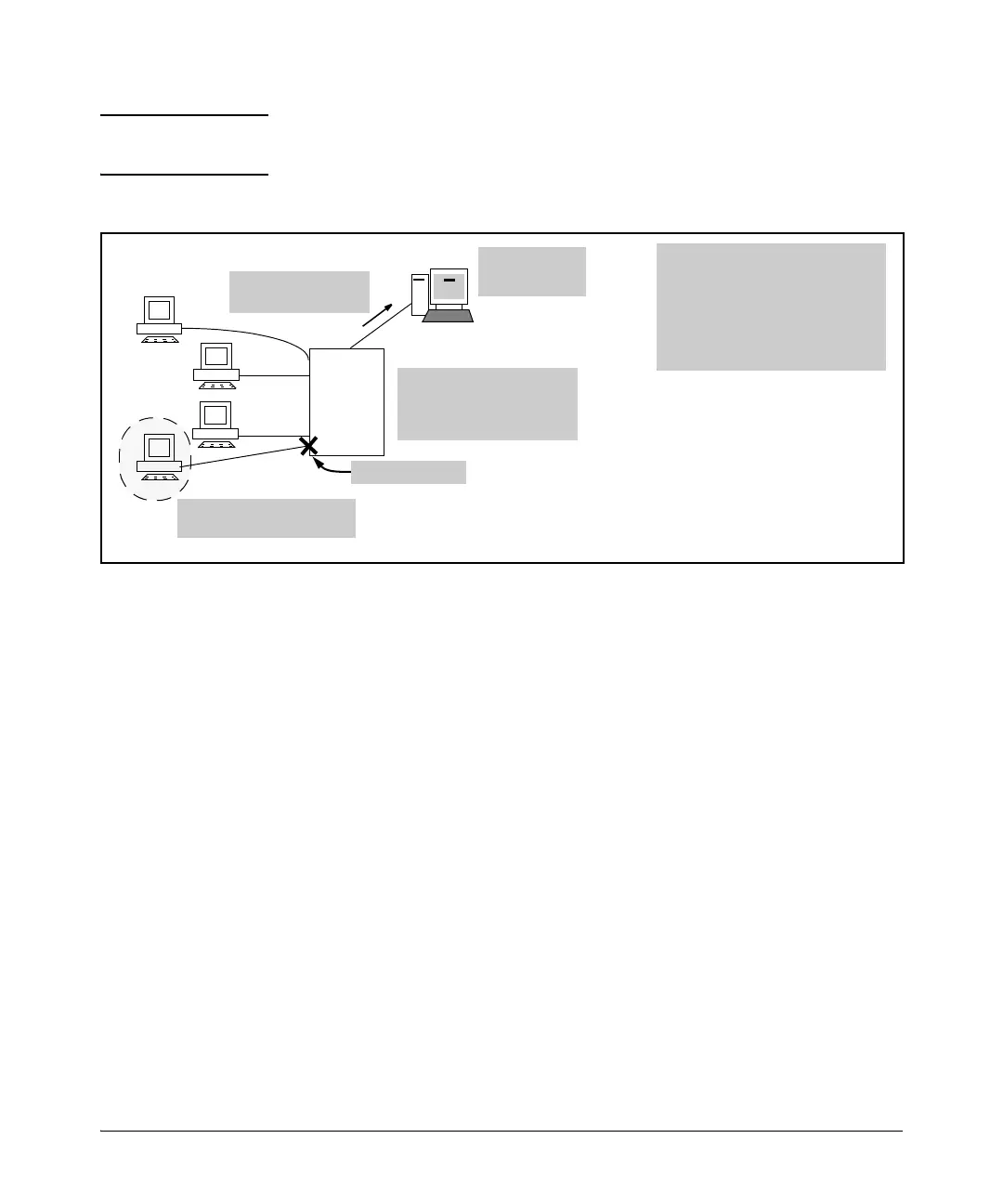
Figure 3-1. Example of Protecting a Network from Agents Using a High IP Connection Rate To Propagate
General Operation
Connection-rate filtering enables notification of worm-like behavior detected
in inbound IP traffic and, depending on how you configure the feature, also
throttles or blocks such traffic. This feature also provides a method for
allowing legitimate, high connection-rate traffic from a given host while still
protecting your network from possibly malicious traffic from other hosts.
Filtering Options
In the default configuration, connection-rate filtering is disabled. When
enabled on a port, connection-rate filtering monitors inbound IP traffic for a
high rate of connection requests from any given host on the port. If a host
appears to exhibit the worm-like behavior of attempting to establish a large
number of outbound IP connections in a short period of time, the switch
responds in one of the following ways, depending on how connection-rate
filtering is configured:
HP switch with
connection-rate filtering
configured, and block
spreading option enabled.
Configuring connection-rate
filtering on the switch protects the
other devices on the network from
the high connection-rate traffic
(characteristic of worm attacks)
that is detected on the edge port
connected to device D.
Device infected with
worm-like malicious code
A
B
C
D
Port is blocked
SNMP Trap and/or
Event Log message
Management
Station
 Loading...
Loading...


