Version 2.1 (May 2016) 46
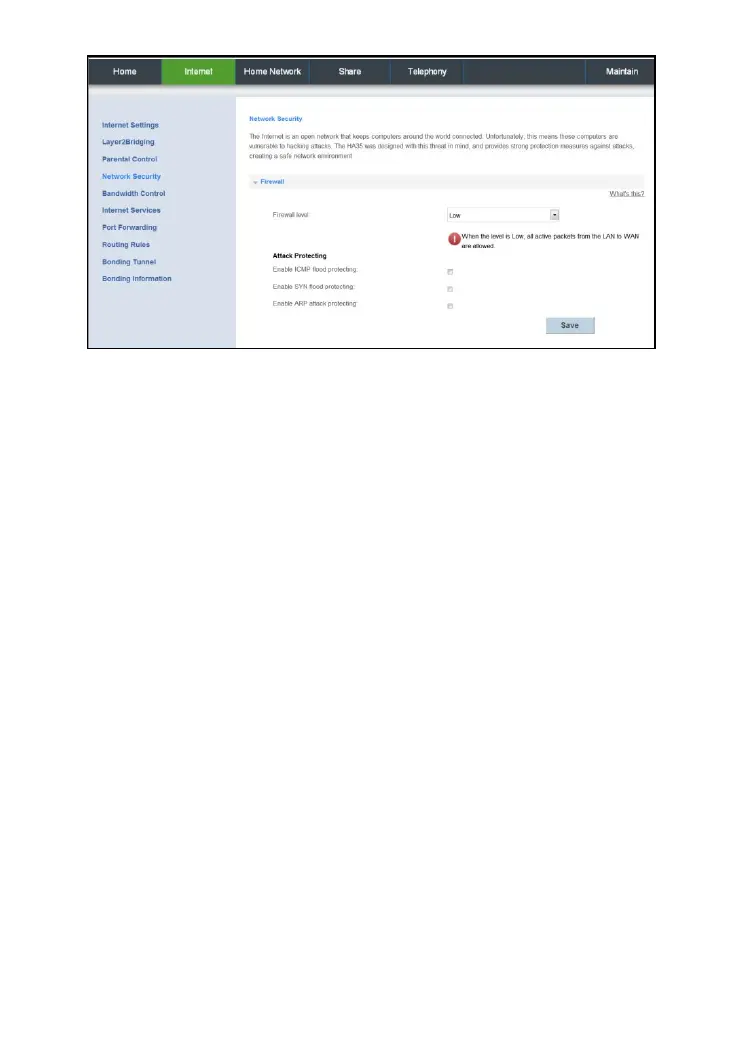
Picture 6-14 firewall
ICMP Flood: The attacker sends plenty of ICMP packets to the specific target within a
short time period to request responses, causing the target system unduly burdened and
unable to process legitimate transmissions.
SYN Flood: The TCP/IP protocol stack only permits a limited number of TCP connections
due to resource restrictions. SYN Flood attacks utilize this feature. The attacker forges a
SYN packet whose source address is forged or nonexistent, and initiates a connection to
the server. Upon receipt of this packet, the server replies with a SYN-ACK packet. Because
there is no receiver of the SYN-ACK packet, a half-connection is established. If the attacker
sends large numbers of such packets, a lot of half-connections are established on the
attacked host and the resources of the attacked host are exhausted; therefore, normal
users cannot access the host until the half-connections expire. In some implementations
where connections can be created without restrictions, SYN Flood has similar influences
that consume the system resources such as the memory.
ARP attack: In ARP attacks, through the vulnerability of ARP, the attacker makes hosts on
a LAN unable to access the Internet by forging data to refresh the dynamic ARP table.
Alternatively, the attacker causes network breakdown or data disclosure by spoofing to
steal sensitive information.
6.6. Configure an ACL
After ACL is enabled, you can limit the access rights of unauthorized users and prevent
network resources from being used improperly.
1. Log in to the web management page.
2. Choose Internet tab.
3. In the navigation tree, choose Network Security.
4. Select the ACL configuration page.
5. Click New ACL.
 Loading...
Loading...