125
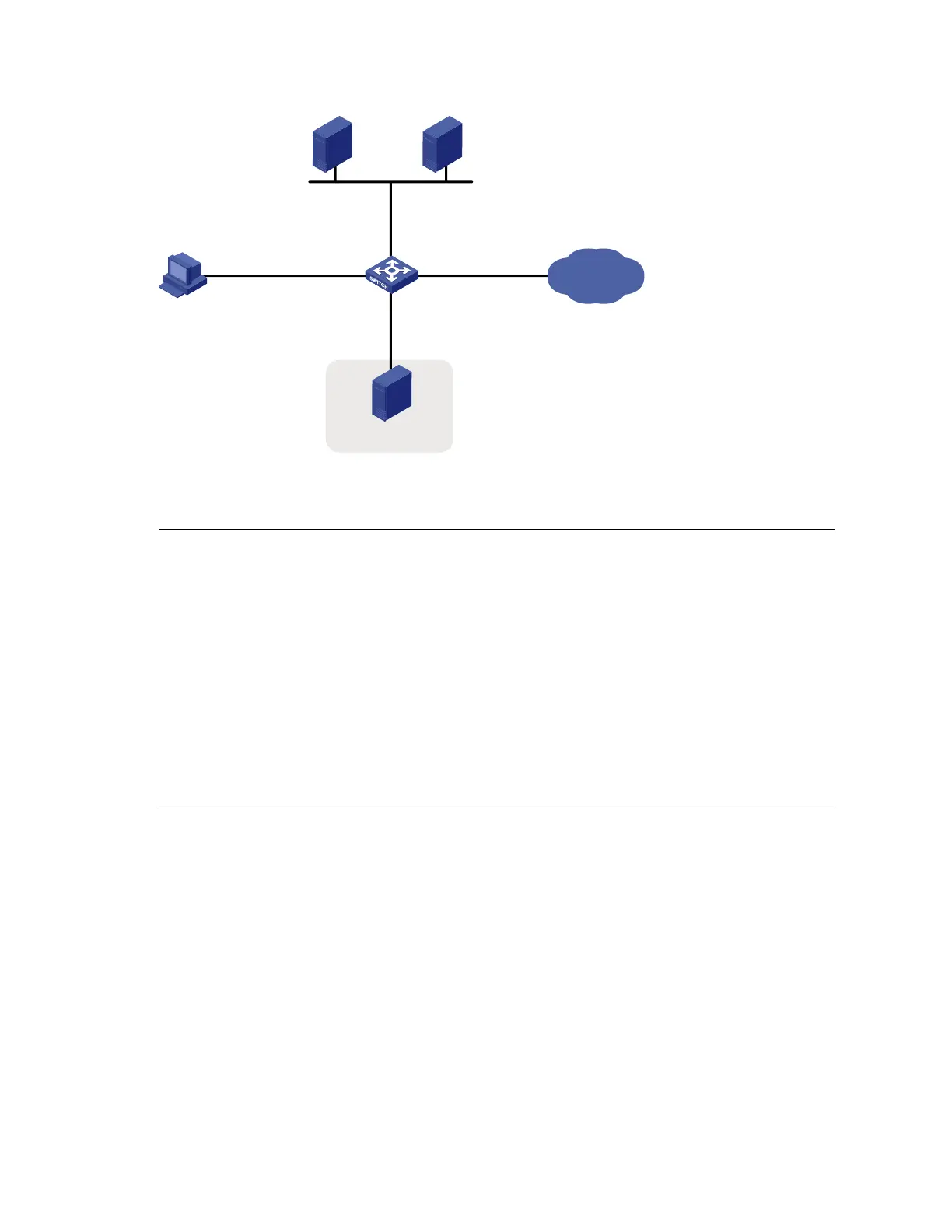
Figure 43 Network diagram for Layer 2 portal authentication configuration
IP network
RADIUS server
Switch
1.1.1.2/24
Host
Vlan-int3
3.3.3.1
Vlan-int8
192.168.1.1/24
GE1/0/1
Vlan-int1
1.1.1.1
DHCP server
Update server
2.2.2.2/24
1.1.1.3/24
(DHCP relay)
Vlan-int2
2.2.2.1/24
Configuration procedures
NOTE:
Ensure that the host, switch, and servers can reach each other before portal authentication is enabled.
Configure the RADIUS server properly to provide normal authentication/authorization/accounting functions for
users. In this example, you need to create a portal user account with the account name userpt on the RADIUS
server, and configure an authorized VLAN for the account.
On the DHCP server, you need to specify the IP address ranges (192.168.1.0/24, 3.3.3.0/24, 2.2.2.0/24),
specify the default gateway addresses (192.168.1.1, 3.3.3.1, 2.2.2.1), specify the device to not assign the update
server’s address 2.2.2.2 to any host, specify the leases of the assigned IP addresses (set a short lease duration
for each address to shorten the IP address update time in case of an authentication state change) and make sure
there is a route to the host.
As the DHCP server and the DHCP client are not in the same subnet, you need to configure a DHCP relay agent
on the subnet of the client. For more information about DHCP relay agent, see the
Layer 3—IP Services
Configuration Guide
.
1. Configure portal authentication
# Add Ethernet ports to related VLANs and configure IP addresses for the VLAN interfaces. (Details not
shown)
# Configure PKI domain pkidm, and apply for a local certificate and CA certificate. For more
configuration information, see the chapter ―PKI configuration.‖
# Edit the user-defined authentication pages file, compress it into a zip file named defaultfile, and save
the file in the root directory of the access device.
# Configure SSL server policy sslsvr, and specify to use PKI domain pkidm.
<Switch> system-view
[Switch] ssl server-policy sslsvr
[Switch-ssl-server-policy-sslsvr] pki pkidm
[Switch-ssl-server-policy-sslsvr] quit
 Loading...
Loading...











