68
Works with any RADIUS server that
supports PAP or CHAP authentication.
Supports only MD5-Challenge
EAP authentication and the
"username + password" EAP
authentication initiated by an
iNode 802.1X client.
The processing is complex on
the network access device.
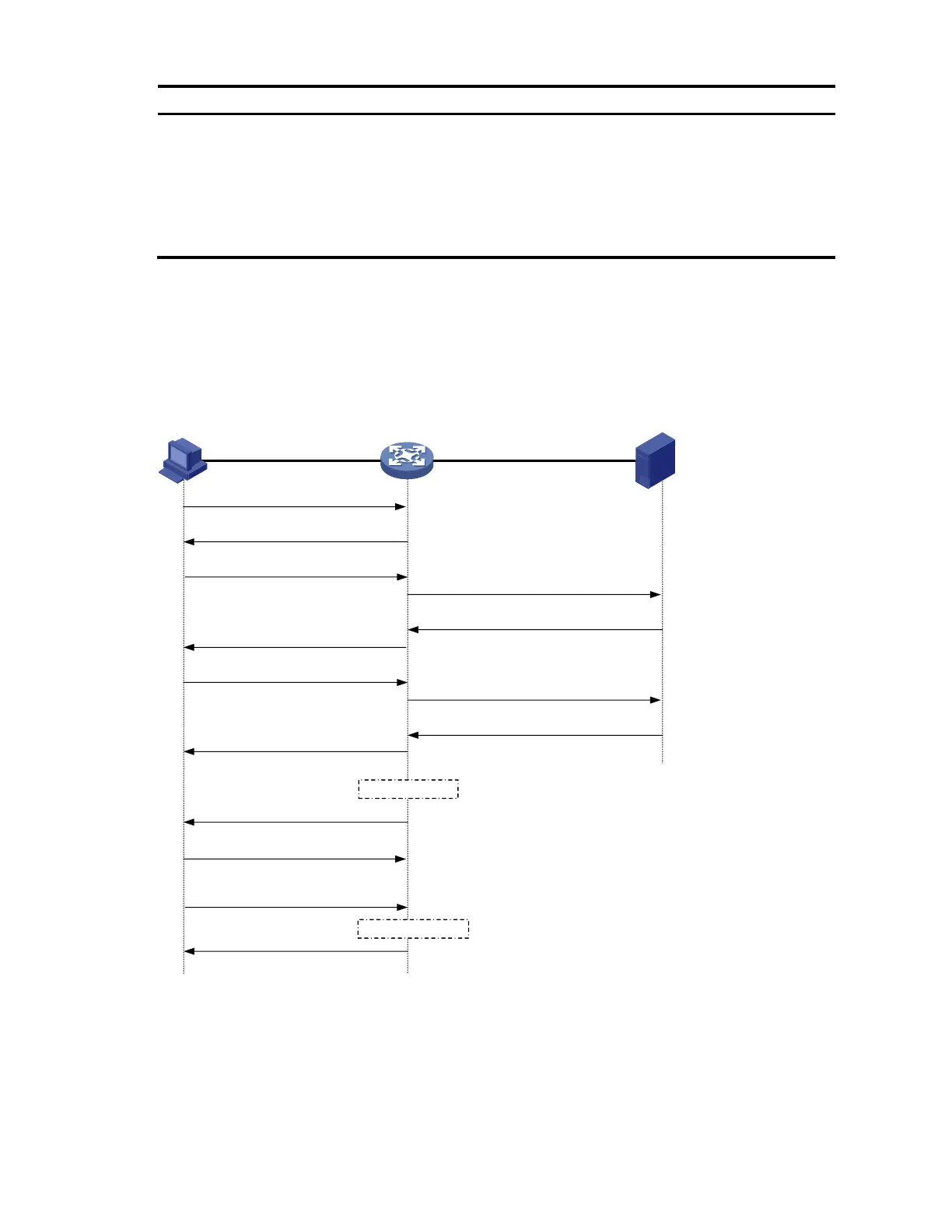
EAP relay
Figure 31 shows the basic 802.1X authentication procedure in EAP relay mode, assuming that EAP-MD5
is used.
Figure 31 802.1X authentication procedure in EAP relay mode
EAPOL
EAPOR
(1) EAPOL-Start
(2) EAP-Request/Identity
(3) EAP-Response/Identity
(6) EAP-Request/MD5 challenge
(10) EAP-Success
(7) EAP-Response/MD5 challenge
(4) RADIUS Access-Request
(EAP-Response/Identity)
(5) RADIUS Access-Challenge
(EAP-Request/MD5 challenge)
(9) RADIUS Access-Accept
(EAP-Success)
(8) RADIUS Access-Request
(EAP-Response/MD5 challenge)
(11) EAP-Request/Identity
(12) EAP-Response/Identity
(13) EAPOL-Logoff
...
Client Device Authentication server
Port authorized
Port unauthorized
(14) EAP-Failure
1. When a user launches the 802.1X client software and enters a registered username and password,
the 802.1X client software sends an EAPOL-Start packet to the network access device.
2. The network access device responds with an Identity EAP-Request packet to ask for the client
username.
 Loading...
Loading...











