Enable SSH: Enabling SSH (Secure Shell) function is to encrypt and compress the data and to
reduce the transmission time.
3. Check the checkbox to enable the Illegal Login Lock function.
Illegal Login Lock: Enabling illegal login lock function is to automatically lock the device IP
after the admin user performing 7 failed password attempts (5 attempts for the
user/operator).
4. Click to save the settings.
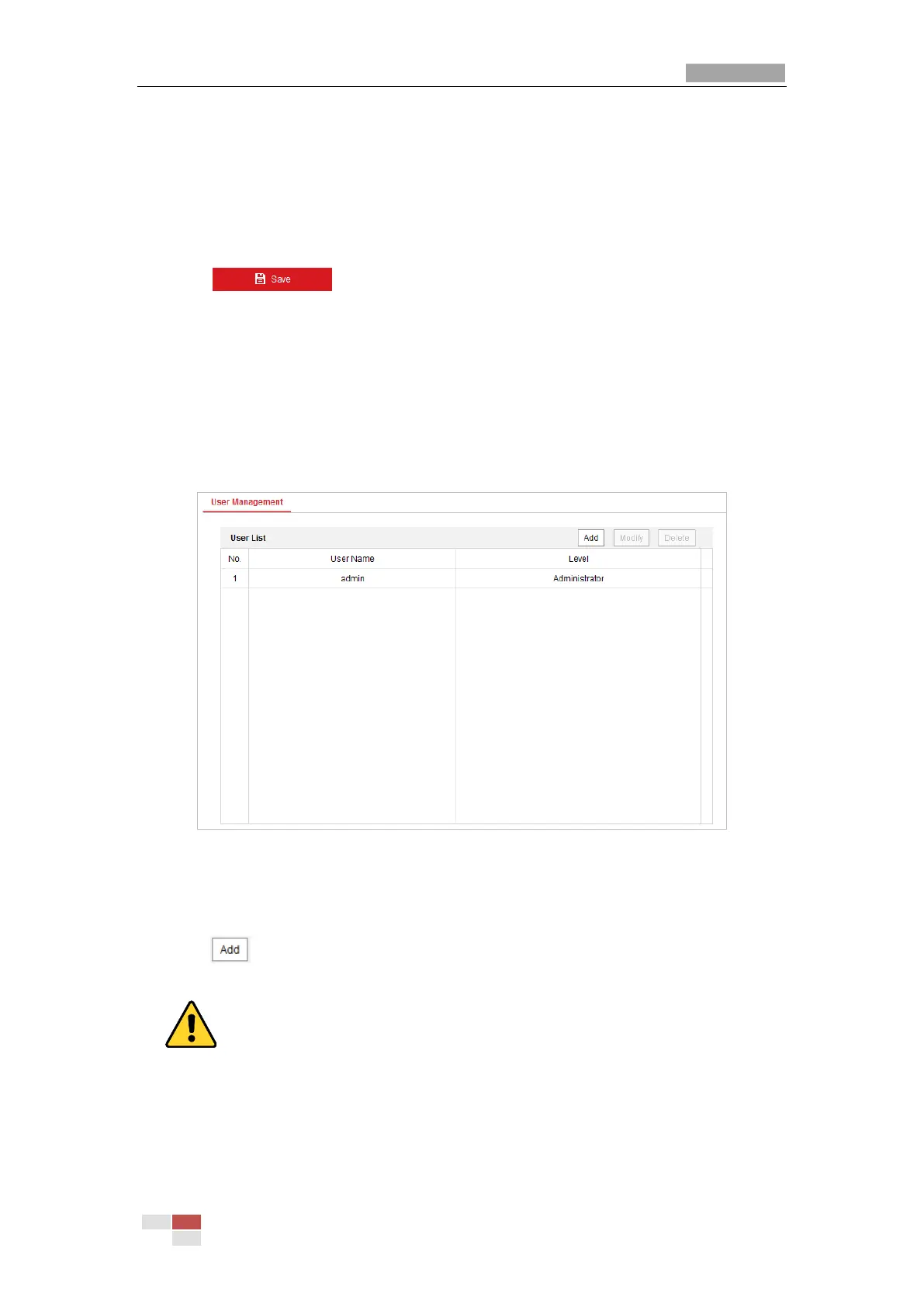
7.5.4 User Management
Enter the User Management interface:
Configuration > System > User Management
The admin user has access to create, modify or delete other accounts. Up to 32 user accounts can
be created.
Figure 7-74 User Information
Add a User
Steps:
1. Click to add a user.
2. Input the new User Name, select Level and input Password.
For your privacy and to better protect your system against security risks, we strongly recommend the use
of strong passwords for all functions and network devices. The password should be something of your
own choosing (Using a minimum of 8 characters, including at least three of the following categories:
upper case letters, lower case letters, numbers, and special characters.) in order to increase the security
of your product.

 Loading...
Loading...











