RADIUS Authentication and Accounting
Configuring a RADIUS Server To Specify Per-Port CoS and Rate-Limiting Services
Configuring an ACL in a RADIUS Server
This section provides general guidelines for configuring a RADIUS server to
specify RADIUS-based ACLs. Also included is an example configuration for a
FreeRADIUS server application. However, to configure support for these
services on a specific RADIUS server application, please refer to the docu
-
mentation provided with the application.
Elements in a RADIUS-Based ACL Configuration. A RADIUS-based
ACL configuration in a RADIUS server has the following elements:
■ vendor and ACL identifiers:
• ProCurve Vendor-Specific ID: 11
• Vendor-Specific Attribute for ACLs: 61 (string = HP-IP-FILTER-RAW)
• Setting: HP-IP-FILTER-RAW = < “permit” or “deny” ACE >
(Note that the “string” value and the “Setting” specifier are identical.)
■ ACL configuration, including:
• one or more explicit “permit” and/or “deny” ACEs created by the
system operator
• implicit deny any any ACE automatically active after the last operator-
created ACE
Example of Configuring a RADIUS-based ACL Using the FreeRADIUS
Application. This example illustrates one method for configuring RADIUS-
based ACL support for two different client identification methods (username/
password and MAC address). For information on how to configure this
functionality on other RADIUS server types, refer to the documentation
provided with the server.
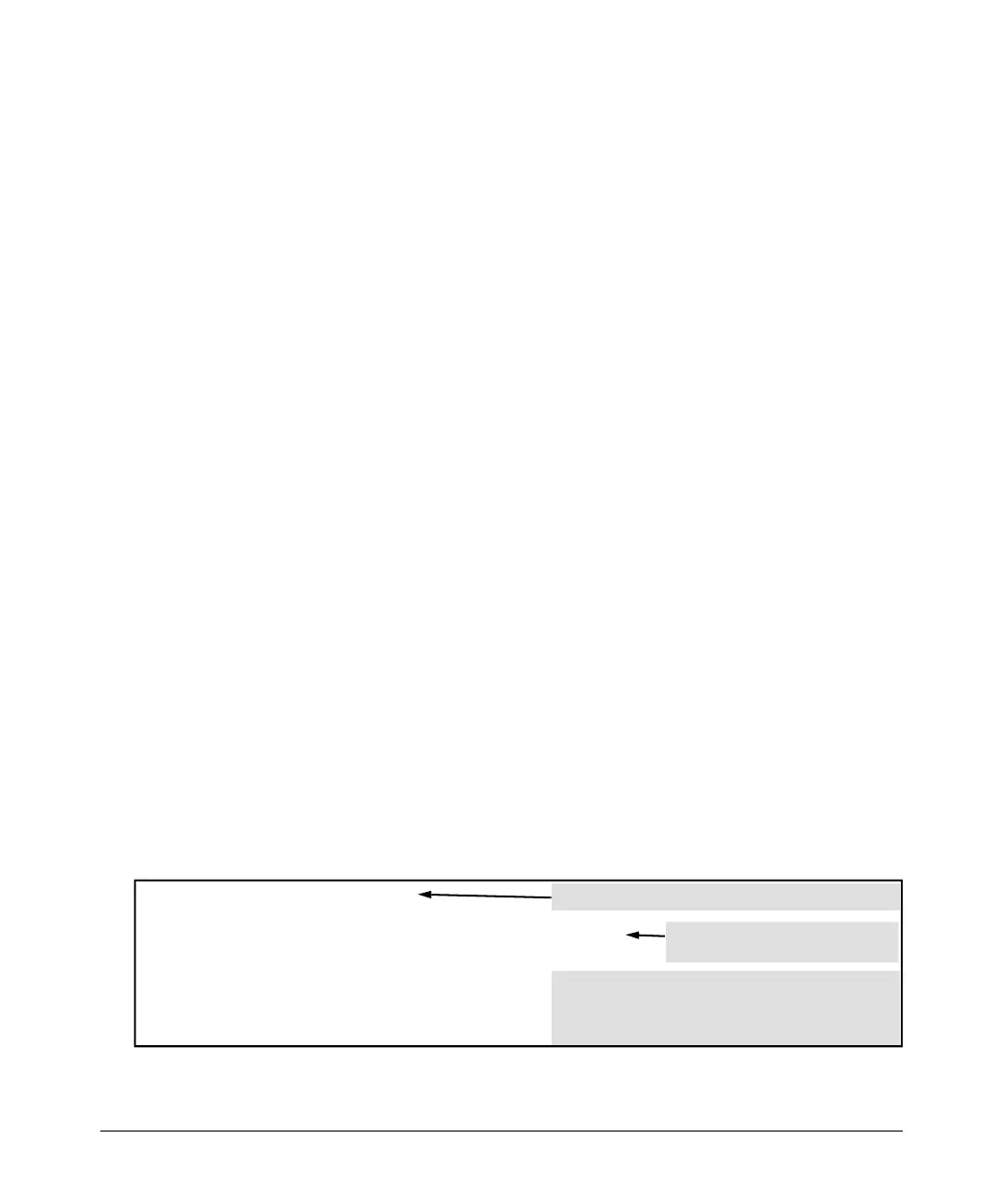
1. Enter the HP vendor-specific ID and the ACL VSA in the FreeRADIUS
dictionary file:
VENDOR HP
BEGIN-VENDOR HP
11
ProCurve (HP) Vendor-Specific ID
ProCurve (HP) Vendor-Specific
ATTRIBUTE HP-IP-FILTER-RAW 61 STRING
Attribute for RADIUS-Based ACLs
END-VENDOR HP
Note that if you were also using the RADIUS server to
administer 802.1p (CoS) priority and/or Rate-Limiting, you
would also insert the ATTRIBUTE entries for these
functions above the END-VENDOR entry.
Figure 6-13. Example of Configuring the VSA for RADIUS-Based ACLs in a FreeRADIUS Server
6-38

 Loading...
Loading...











