Virus Throttling (5300xl Switches Only)
Introduction
signature updates will still need to be deployed to hosts, the network remains
functional and the overall distribution of the malicious code is limited.
Connection-Rate filtering is a countermeasure tool you can use in your inci-
dent-management program to help detect an manage worm-type IT security
threats received in inbound routed traffic. Major benefits of this tool include:
■ Behavior-based operation that does not require identifying details
unique to the code exhibiting the worm-like operation.
■ Handles unknown worms.
■ Needs no signature updates.
■ Protects network infrastructure by slowing or stopping routed traffic
from hosts exhibiting high connection-rate behavior.
■ Allows network and individual switches to continue to operate, even
when under attack.
■ Provides Event Log and SNMP trap warnings when worm-like
behavior is detected
■ Gives IT staff more time to react before the threat escalates to a crisis.
Note When configured on a port, connection-rate filtering is triggered by routed
IPv4 traffic received inbound with a relatively high rate of IP connection
attempts. (Connection-Rate filtering is not triggered by such traffic when
both the SA and DA are in the same VLAN—that is, switched traffic). Note
that connection-rate filtering applies only to routed traffic. Switched traffic
from a blocked or throttled host is not blocked or throttled.
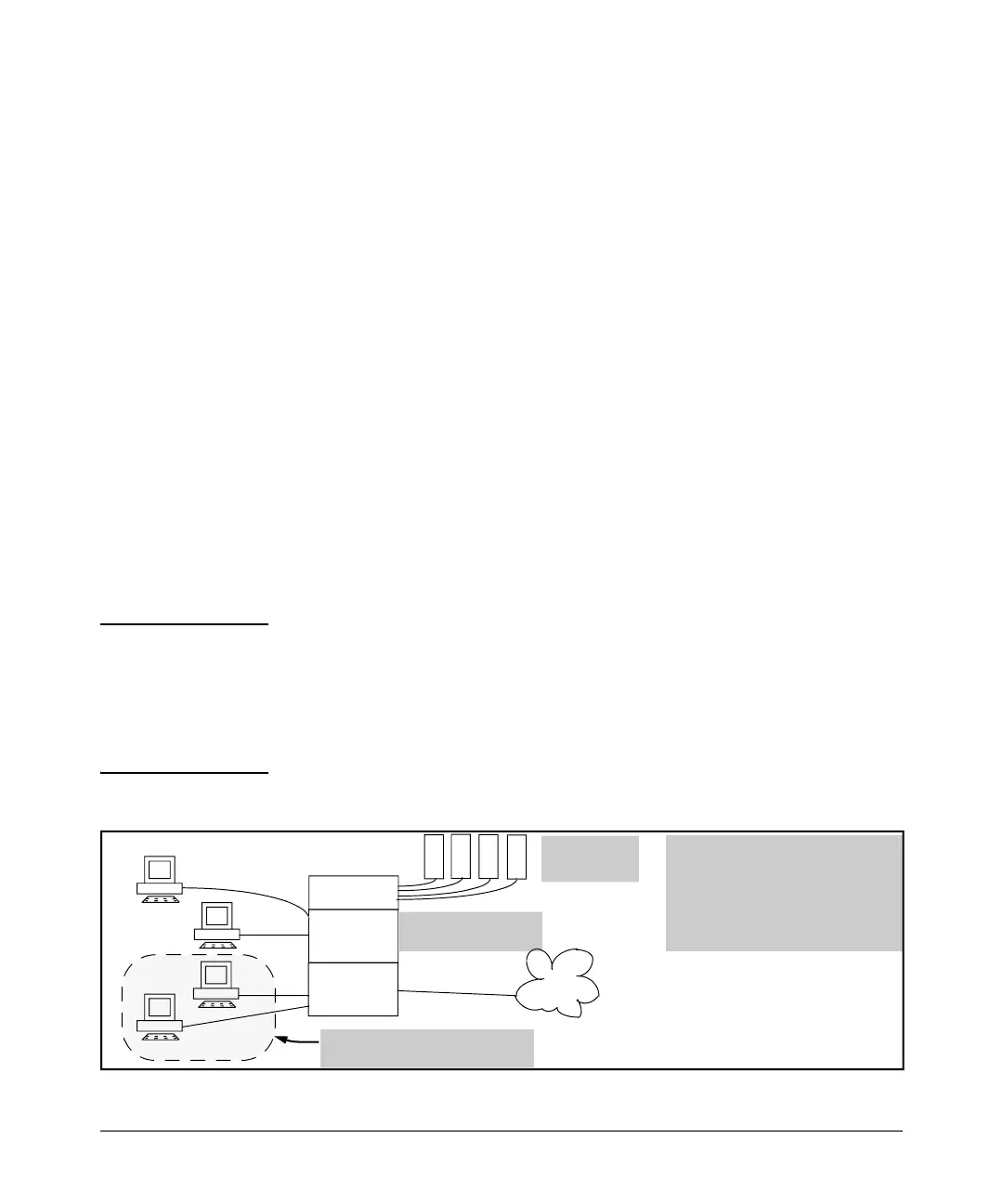
Networked
hi
i
i
A
B
C
D
5300xl with Routing
Configured
Servers
Internet
Configuring connection-rate filtering
on the 5300xl switch protects the
devices on VLANs 1 and 2 from the
gh connection-rate traffic
(character stic of worm attacks) that
s being routed from VLAN 3.
Devices on VLAN 3 Infected
with Worm-Like Malicious Code
VLAN 1
VLAN 2
VLAN 3
Figure 3-1. Example of Protecting a Network from Agents Using a High IP Connection Rate To Propagate
3-4
 Loading...
Loading...











