fingerprint sha1 7a34d94624b1c1bcbf6d763c4a67035d5b578eaf
#
return
12.8.2 Example for Configuring PKI in IPSec
Networking Requirements
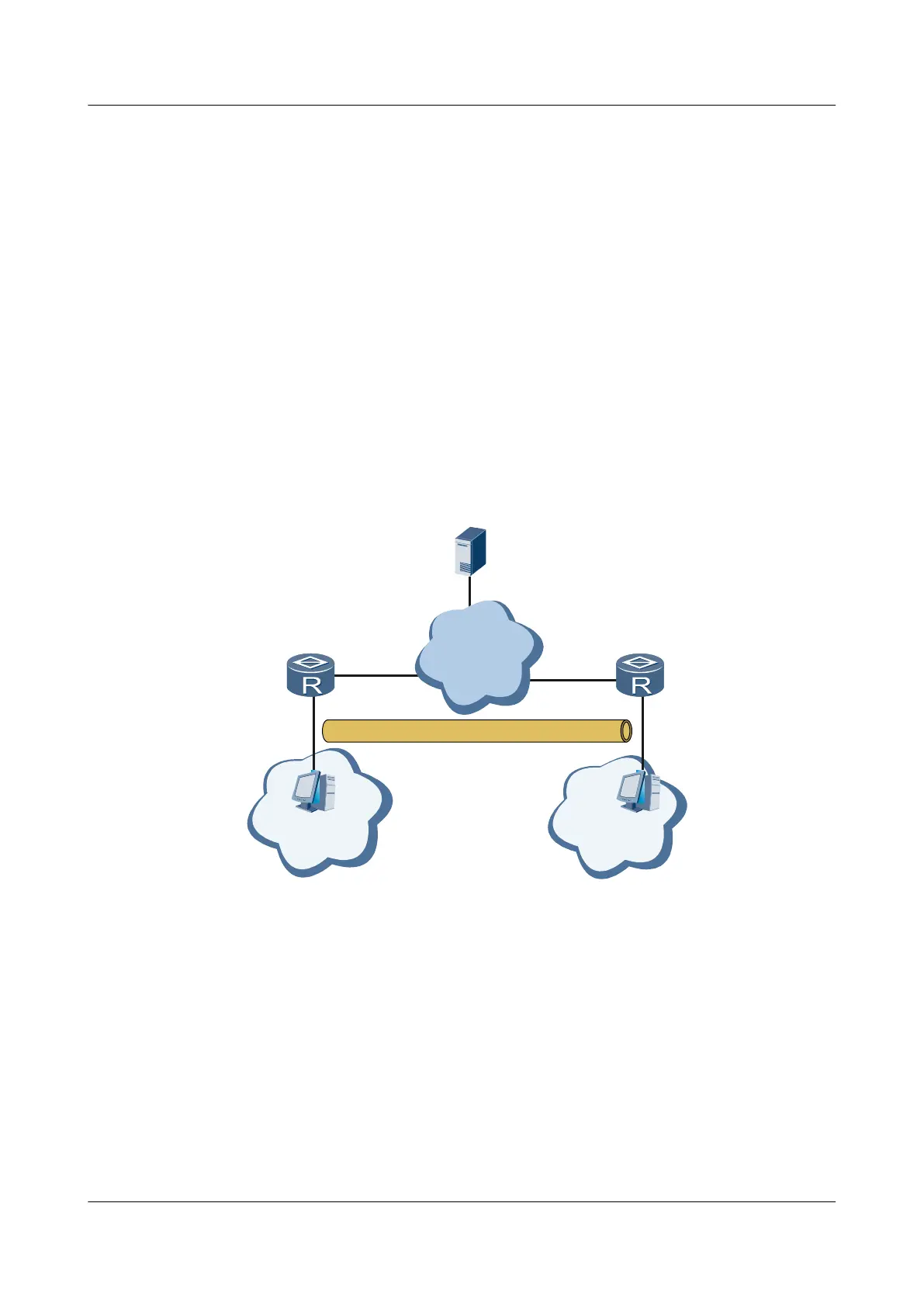
As shown in Figure 12-4, devices in two subnets communicate with the Internet using respective
gateways and need to establish an IPSec tunnel to transmit data flows. To meet this requirement,
perform the following operations:
l Establish an IPSec tunnel between the two gateways to protect security of data flows
transmitted between subnet 1 at 10.1.1.0/24 and subnet at 11.1.1.0/24.
l Establish a security tunnel between the two gateways using Internet Key Exchange (IKE)
negotiation. During IKE negotiation, PKI certificates are used for identity authentication.
Figure 12-4 Configuring PKI in IPSec
Internet
Internet
10.1.1.2/24
11.1.1.2/24
10.1.1.1/24
11.1.1.1/24
Eth2/0/0
Eth2/0/0
CA
GE0/0/1
GE0/0/1
IPSec Tunnel
Group 1
Group 2
RouterA
RouterB
1.1.1.1/24 2.2.2.1/24
Huawei AR1200-S Series Enterprise Routers
Configuration Guide - Security 12 PKI Configuration
Issue 02 (2012-03-30) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
254

 Loading...
Loading...