ISG 2000 User’s Guide
16 IPSec VPN
IPSec VPN
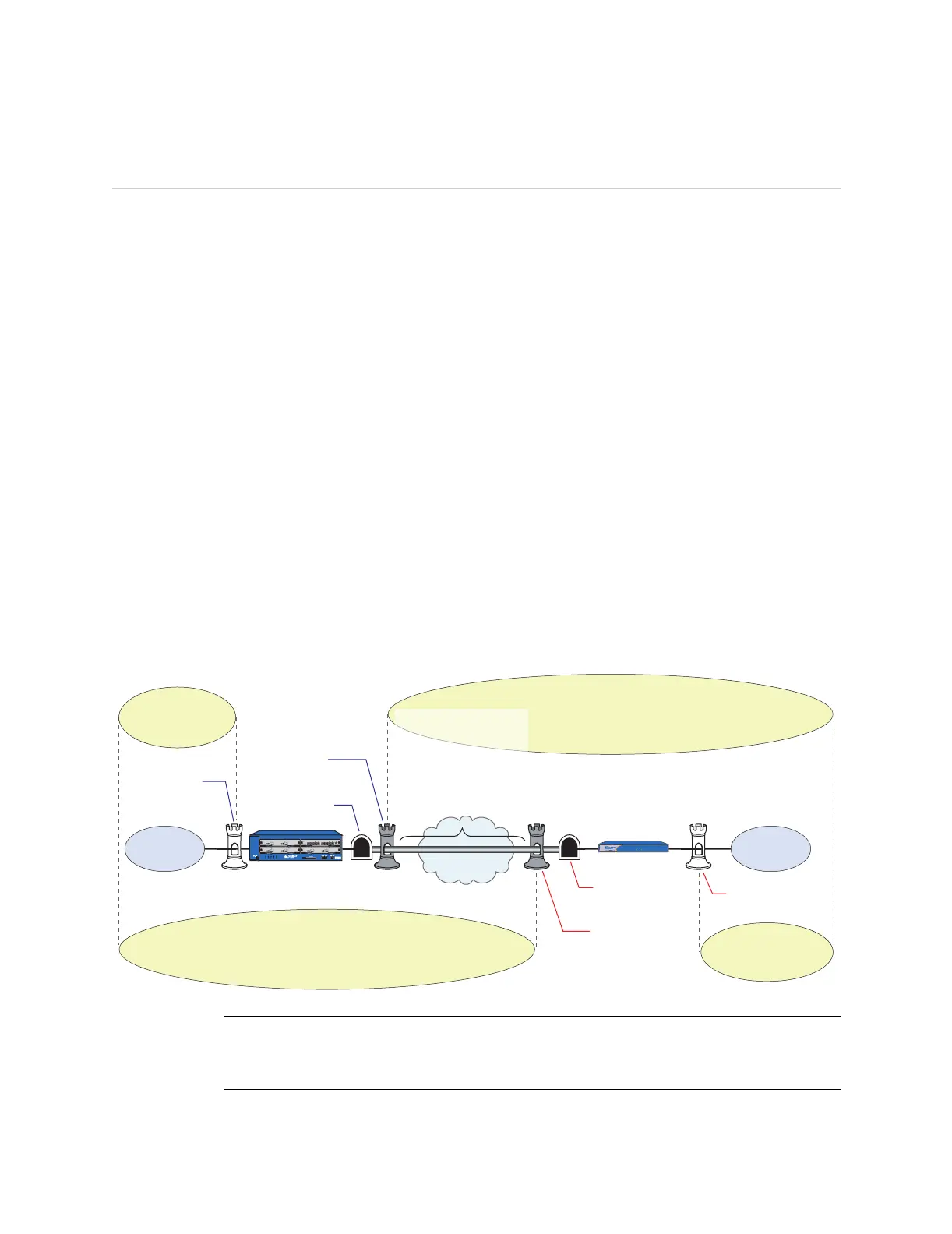
This section presents a configuration for a route-based VPN tunnel between the ISG
2000 and a remote peer with a dynamically assigned IP address. The NetScreen
device at the remote peer site is a NetScreen-5GT in Trust-Untrust mode. Because it
receives its address dynamically through PPPoE or DHCP, Phase 1 negotiations
must be in aggressive mode. The tunnel configuration uses the following elements:
Tunnel interface: tunnel.1 in Untrust zone
Outgoing interface:
ISG 2000: ethernet1/1
NetScreen-5GT: Untrust
Phase 1 exchange mode: Aggressive
Phase 1 and Phase 2 proposal security levels: Compatible
Proxy IDs: local 0.0.0.0/0; remote 0.0.0.0/0; service ANY
Preshared key: Iwb715iSF
IKE ID for remote peer: peer1@jnpr.net
Figure 10: IPSec VPN Tunnel
The VPN tunnel configuration for the NetScreen devices at both ends is provided.
HA
FLASH
PWR
FAN
ALARM
MOD1
TEMP
MOD2
STATUS
MOD3
ISG 2000
Untrust Zone
ethernet2/1
10.1.1.1/24
ethernet1/1
1.1.1.1/30
Tunnel Interface
tunnel.1
Internet
VPN Tunnel: vpn1
Agressive Mode
Security Level for P1 and P2:
Compatible
IKE ID for NetScreen-5GT:
peer1@jnpr.net
Preshared Key: Iwb715iSF
NetScreen-ISG 2000
NetScreen-5GT
Trust Zone
Untrust Zone Trust Zone
Untrust Interface
Dynamically
Assigned
IP Address
Tunnel Interface
tunnel.1
unnumbered
Trust Interface
10.2.2.1/24
®
POWER STATUS
1 2 3 4
LINK/ACTIVITY
10/100
UNTRUSTED
10.1.1.0/24 10.2.2.0/24
NOTE: NetScreen ScreenOS offers a rich variety of options for IPSec VPN tunnels. For
information about the many available options, refer to the VPNs volume in the
NetScreen Concepts & Examples ScreenOS Reference Guide.

 Loading...
Loading...