Cookbook Configuration
108
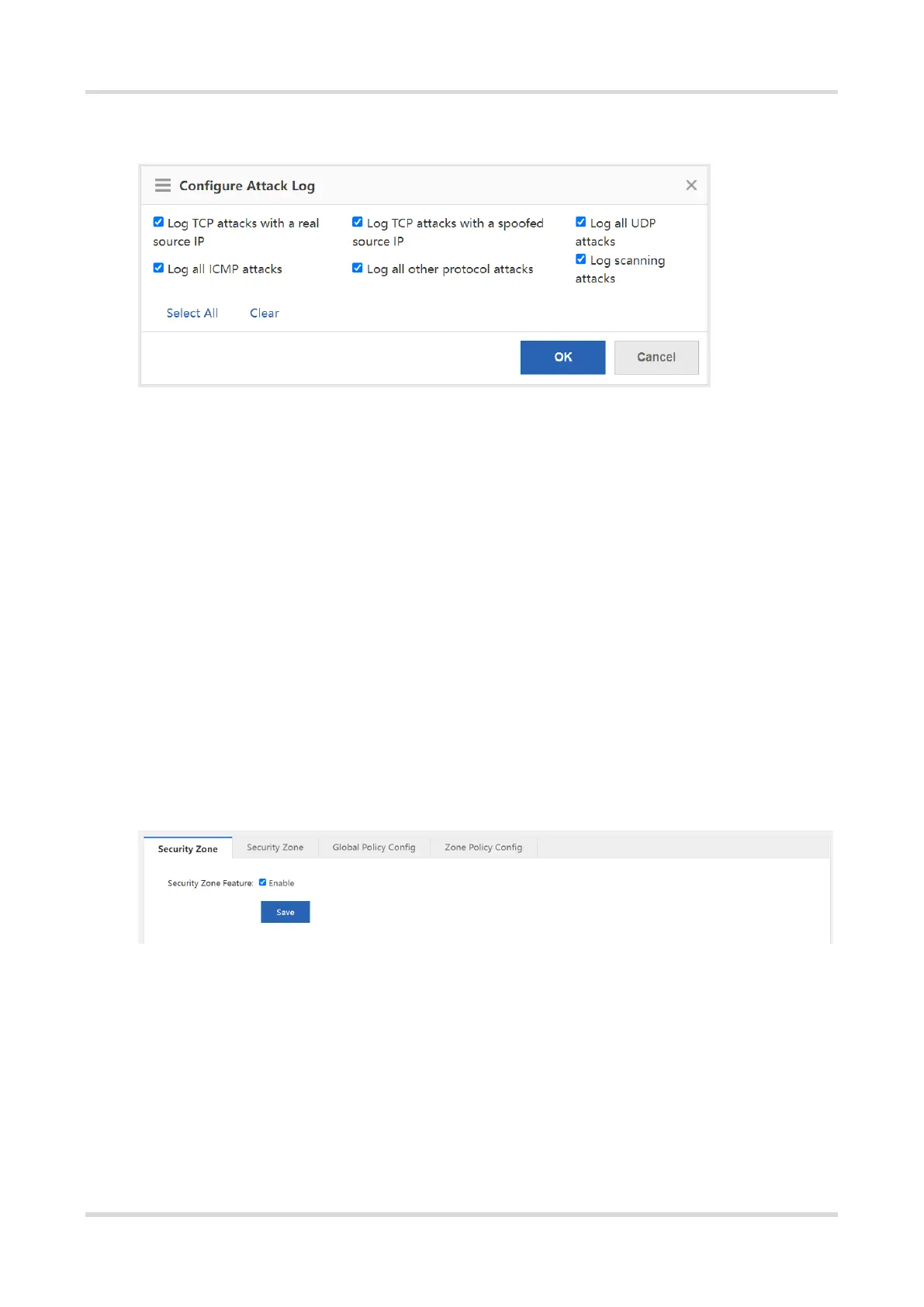
(9) (Optional) Click Config of the attack log to enable logging and printing of the specified type of policy. Select
the log types as required, and click OK.
3.12.2 Security Zone Configuration
A security zone is a logical concept that the objects in a security zone have same security requirements, security
access control, and border control policies. You can group multiple interfaces or IP addresses with the same
security requirements on the device into the same security zone to implement hierarchical management of
policies and precise protection. For example, the subnet A is connected to the interface 1 of the router device
which belongs to the security zone 1, and the subnet B is connected to the interface 2 of the router device which
belongs to the security zone 2. You can only configure the access policy between the security zone 1 and the
security zone 2 to perform the access control on the subnet A and the subnet B.
1. Enabling the Security Zone Feature
The security zone feature is used to display and configure the security zone menu. You can enable this feature
to view and configure the security zone and related policies.
Procedure
(1) Choose Firewall > Security Zone Config > Security Zone Feature.
(2) Select the security zone feature and click Save.
2. Security Zone
The device supports creating a security zone based on the IP address (IPv4 only) or the device interface. You
cannot use the two types of security zones simultaneously. The existing security zone and zone policies will be
cleared if you switch the creating mode. An interface-based security zone is created by default.
The default access rules between different security zones are as follows.
The clients or interfaces in the same security zone cannot access each other.
The security zone of higher priority can access the security zone of lower priority, but not vice versa.

 Loading...
Loading...








