9-37
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 9 Network Address Translation (NAT)
Identity NAT
hostname(config)# object network MAPPED_IPv4_POOL
hostname(config-network-object)# range 10.1.2.1 10.1.2.254
hostname(config)# nat (inside,outside) source static INSIDE_NW MAPPED_IPv6_NW
destination static OUTSIDE_IPv6_NW OUTSIDE_IPv6_NW
hostname(config)# nat (inside,outside) source dynamic INSIDE_NW pat-pool MAPPED_IPv4_POOL
destination static OUTSIDE_IPv4_NW OUTSIDE_IPv4_NW
Identity NAT
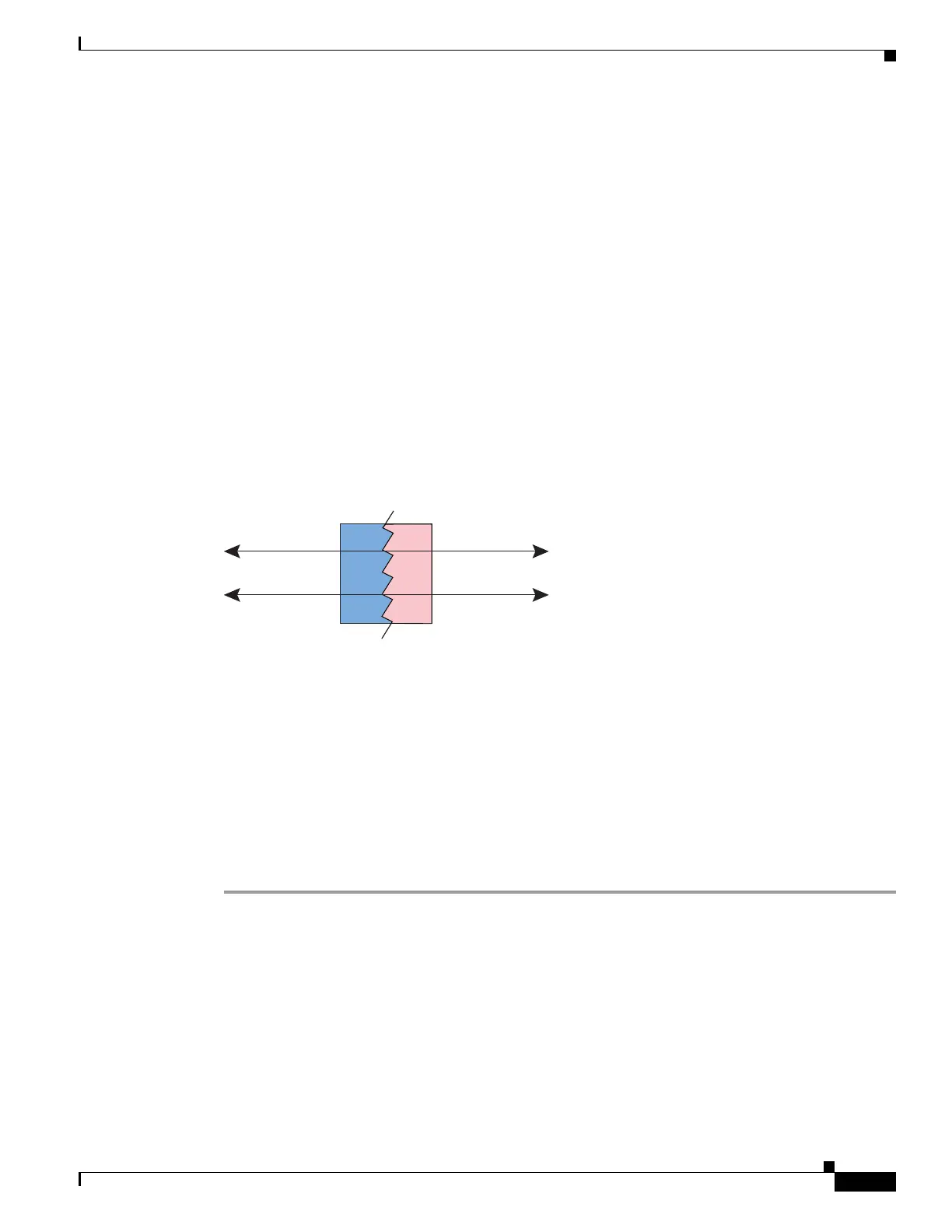
You might have a NAT configuration in which you need to translate an IP address to itself. For example,
if you create a broad rule that applies NAT to every network, but want to exclude one network from NAT,
you can create a static NAT rule to translate an address to itself. Identity NAT is necessary for remote
access VPN, where you need to exempt the client traffic from NAT.
The following figure shows a typical identity NAT scenario.
Figure 9-12 Identity NAT
The following topics explain how to configure identity NAT.
• Configure Identity Network Object NAT, page 9-37
• Configure Identity Twice NAT, page 9-39
Configure Identity Network Object NAT
This section describes how to configure an identity NAT rule using network object NAT.
Procedure
Step 1 (Optional.) Create a network object (object network command), or a network object group
(object-group network command), for the mapped addresses.
• Instead of using an object, you can configure an inline address.
• If you use an object, the object must match the real addresses you want to translate.
Step 2 Create or edit the network object for which you want to configure NAT. The object must be a different
one than what you use for the mapped addresses, even though the contents must be the same in each
object.
object network obj_name
Example
209.165.201.1 209.165.201.1
Inside Outside
209.165.201.2 209.165.201.2
130036
Security
Appliance

 Loading...
Loading...



