5-3
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 5 Identity Firewall
About the Identity Firewall
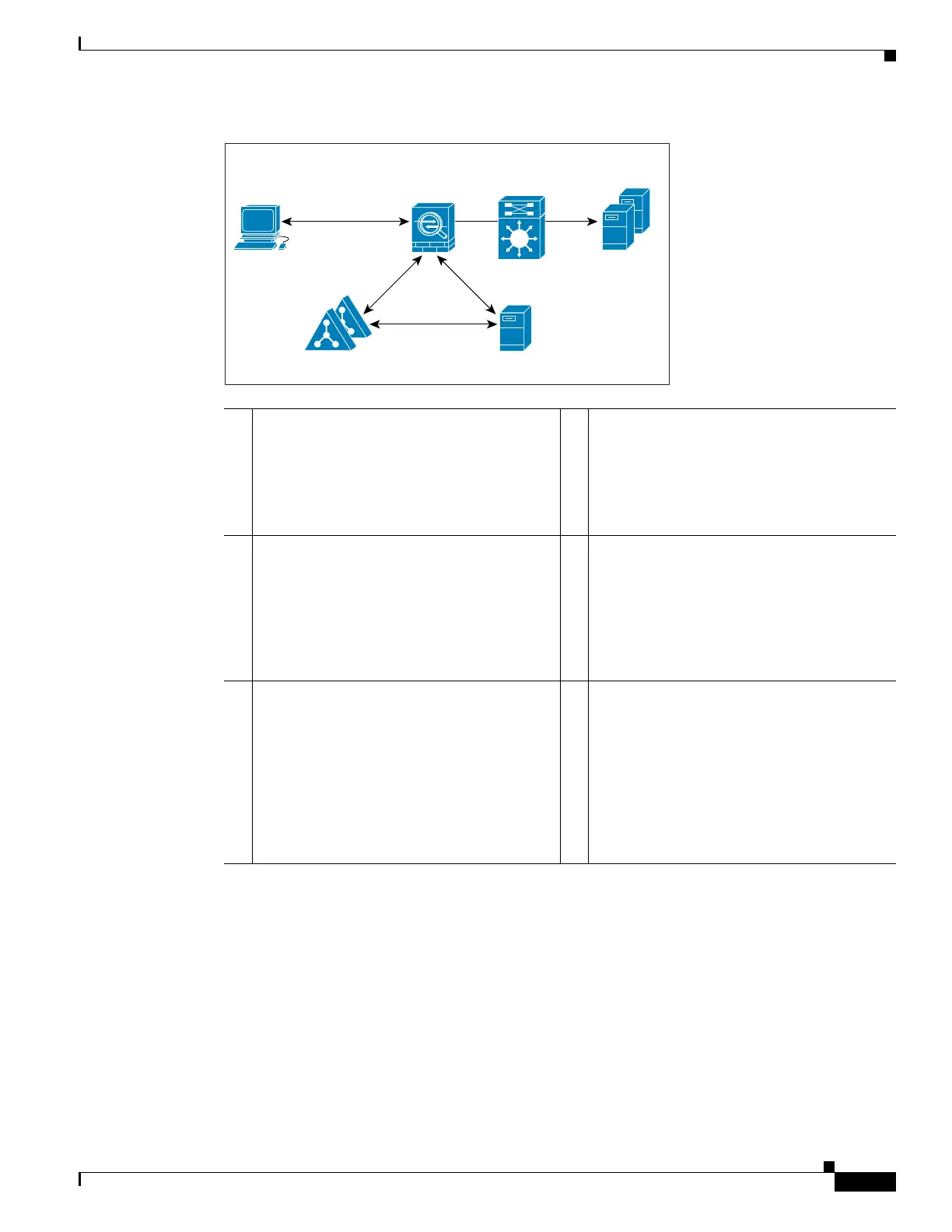
Figure 5-1 Identity Firewall Components
Features of the Identity Firewall
The Identity Firewall includes the following key features.
Flexibility
• The ASA can retrieve user identity and IP address mapping from the AD Agent by querying the AD
Agent for each new IP address or by maintaining a local copy of the entire user identity and IP
address database.
• Supports host group, subnet, or IP address for the destination of a user identity policy.
Client ASA
AD Servers AD Agent
304003
LAN
NetBIOS Probe
mkg.example.com
10.1.1.2
WMI
LDAP
RADIUS
1 On the ASA: Administrators configure local
user groups and Identity Firewall policies.
4 Client <-> ASA: The client logs into the
network through Microsoft Active Directory.
The AD Server authenticates users and
generates user login security logs.
Alternatively, the client can log into the
network through a cut-through proxy or VPN.
2 ASA <-> AD Server: The ASA sends an
LDAP query for the Active Directory groups
configured on the AD Server.
The ASA consolidates local and Active
Directory groups and applies access rules and
Modular Policy Framework security policies
based on user identity.
5 ASA <-> Client: Based on the policies
configured on the ASA, it grants or denies
access to the client.
If configured, the ASA probes the NetBIOS of
the client to pass inactive and no-response
users.
3 ASA <-> AD Agent: Depending on the
Identity Firewall configuration, the ASA
downloads the IP-user database or sends a
RADIUS request to the AD Agent that asks
for the user’s IP address.
The ASA forwards the new mapped entries
that have been learned from web
authentication and VPN sessions to the AD
Agent.
6 AD Agent <-> AD Server: The AD Agent
maintains a cache of user ID and IP address
mapped entries. and notifies the ASA of
changes.
The AD Agent sends logs to a syslog server.
 Loading...
Loading...















