10-24
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 10 NAT Examples and Reference
DNS and NAT
If the user needs to access ftp.cisco.com using the real address, then no further configuration is required.
If there is also a static rule between the inside and DMZ, then you also need to enable DNS reply
modification on this rule. The DNS reply will then be modified two times.In this case, the ASA again
translates the address inside the DNS reply to 192.168.1.10 according to the static rule between inside
and DMZ.
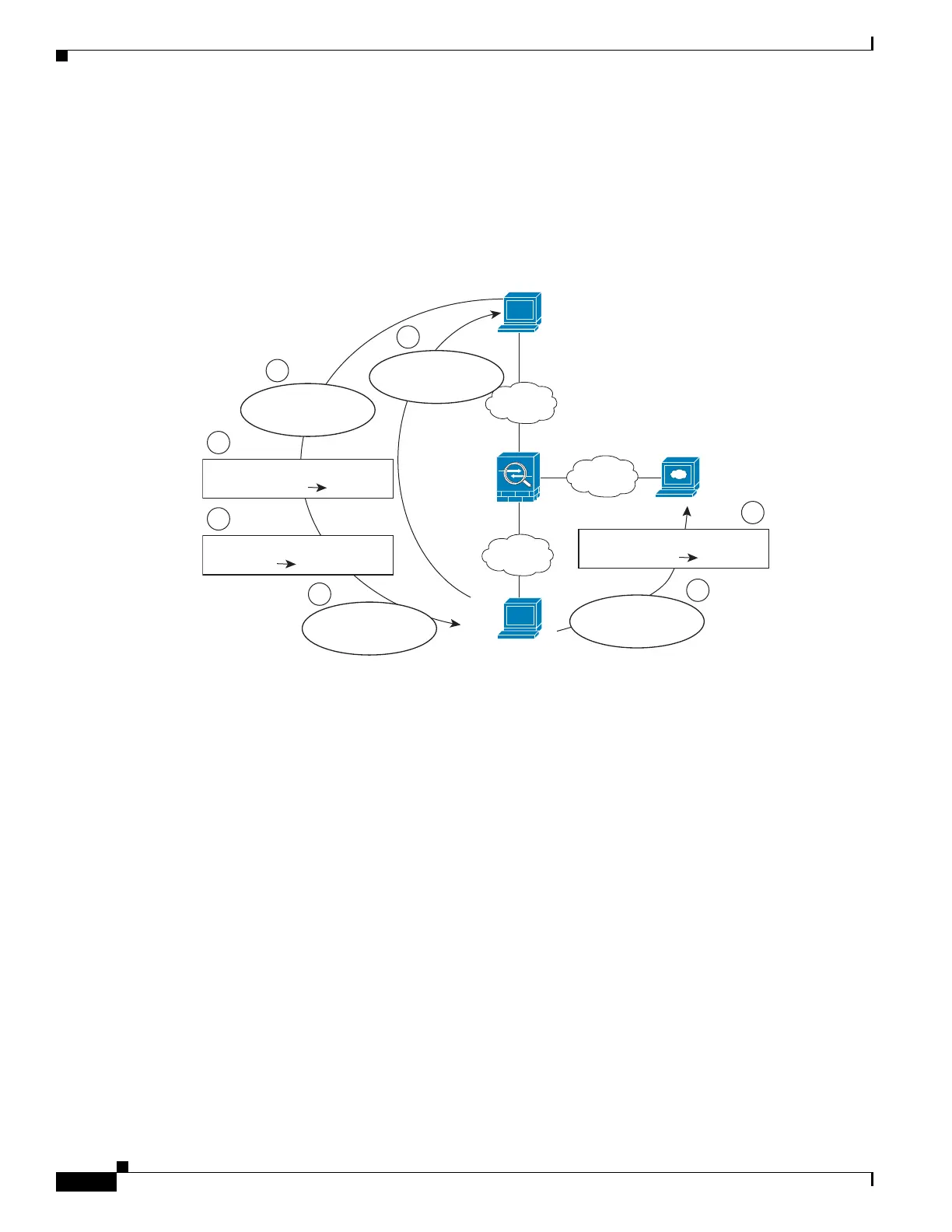
Figure 10-19 DNS Reply Modification, DNS Server, Host, and Server on Separate Networks
DNS Reply Modification, DNS Server on Host Network
The following figure shows an FTP server and DNS server on the outside. The ASA has a static
translation for the outside server. In this case, when an inside user requests the address for ftp.cisco.com
from the DNS server, the DNS server responds with the real address, 209.165.20.10. Because you want
inside users to use the mapped address for ftp.cisco.com (10.1.2.56) you need to configure DNS reply
modification for the static translation.
DNS Server
Outside
Inside
User
1
2
3
5
6
DNS Reply Modification 1
209.165.201.10 10.1.3.14
7
Translation
10.1.3.14
4
DNS Reply Modification 2
10.1.3.14
DNS Reply
209.165.201.10
DNS Reply
DNS Query
ftp.cisco.com?
FTP Request
ASA
ftp.cisco.com
10.1.3.14
Static Translation 1
on Outside to:
209.165.201.10
Static Translation 2
on Inside to:
192.168.1.10
192.168.1.10
192.168.1.10
192.168.1.10
192.168.1.10
DMZ
 Loading...
Loading...















