16-11
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 16 Connection Settings
Configure Connection Settings
the session management path, then there is no entry in the fast path for the connection, and the packets
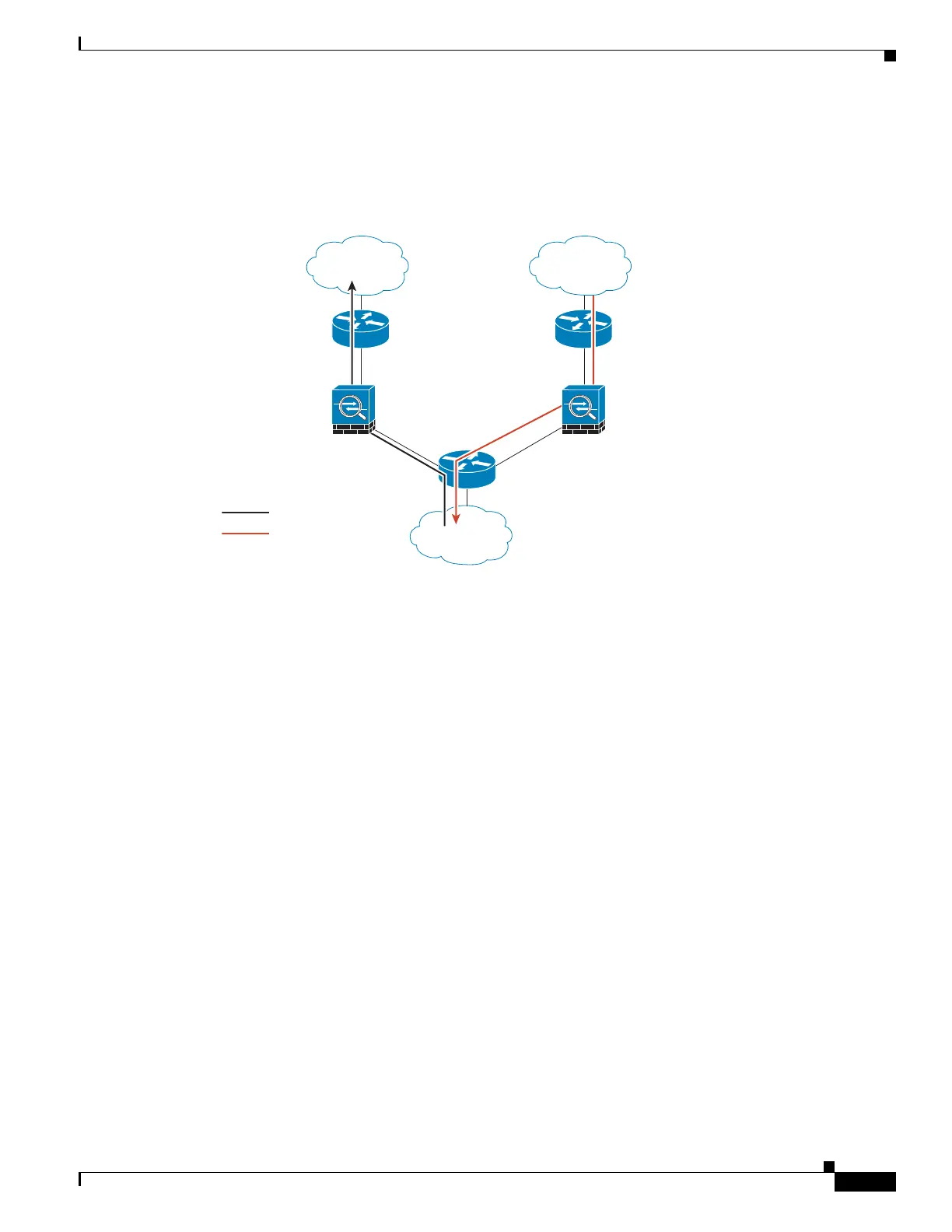
are dropped. The following figure shows an asymmetric routing example where the outbound traffic goes
through a different ASA than the inbound traffic:
Figure 16-1 Asymmetric Routing
If you have asymmetric routing configured on upstream routers, and traffic alternates between two
ASAs, then you can configure TCP state bypass for specific traffic. TCP state bypass alters the way
sessions are established in the fast path and disables the fast path checks. This feature treats TCP traffic
much as it treats a UDP connection: when a non-SYN packet matching the specified networks enters the
ASA, and there is not an fast path entry, then the packet goes through the session management path to
establish the connection in the fast path. Once in the fast path, the traffic bypasses the fast path checks.
Guidelines for TCP State Bypass
TCP State Bypass Unsupported Features
The following features are not supported when you use TCP state bypass:
• Application inspection—Application inspection requires both inbound and outbound traffic to go
through the same ASA, so application inspection is applied TCP state bypass traffic.
• AAA authenticated sessions—When a user authenticates with one ASA, traffic returning via the
other ASA will be denied because the user did not authenticate with that ASA.
• TCP Intercept, maximum embryonic connection limit, TCP sequence number randomization—The
ASA does not keep track of the state of the connection, so these features are not applied.
• TCP normalization—The TCP normalizer is disabled.
• Service module functionality—You cannot use TCP state bypass and any application running on any
type of service module, such as ASA FirePOWER.
• Stateful failover.
ISP A
Inside
network
Outbound?Traffic
Return?Traffic
ISP B
251155
Security
appliance 1
Security
appliance 2
 Loading...
Loading...















