+7(495) 797-3311 www.qtech.ru
Москва, Новозаводская ул., 18, стр. 1
9. Configure the FLUSH mode once topology changes
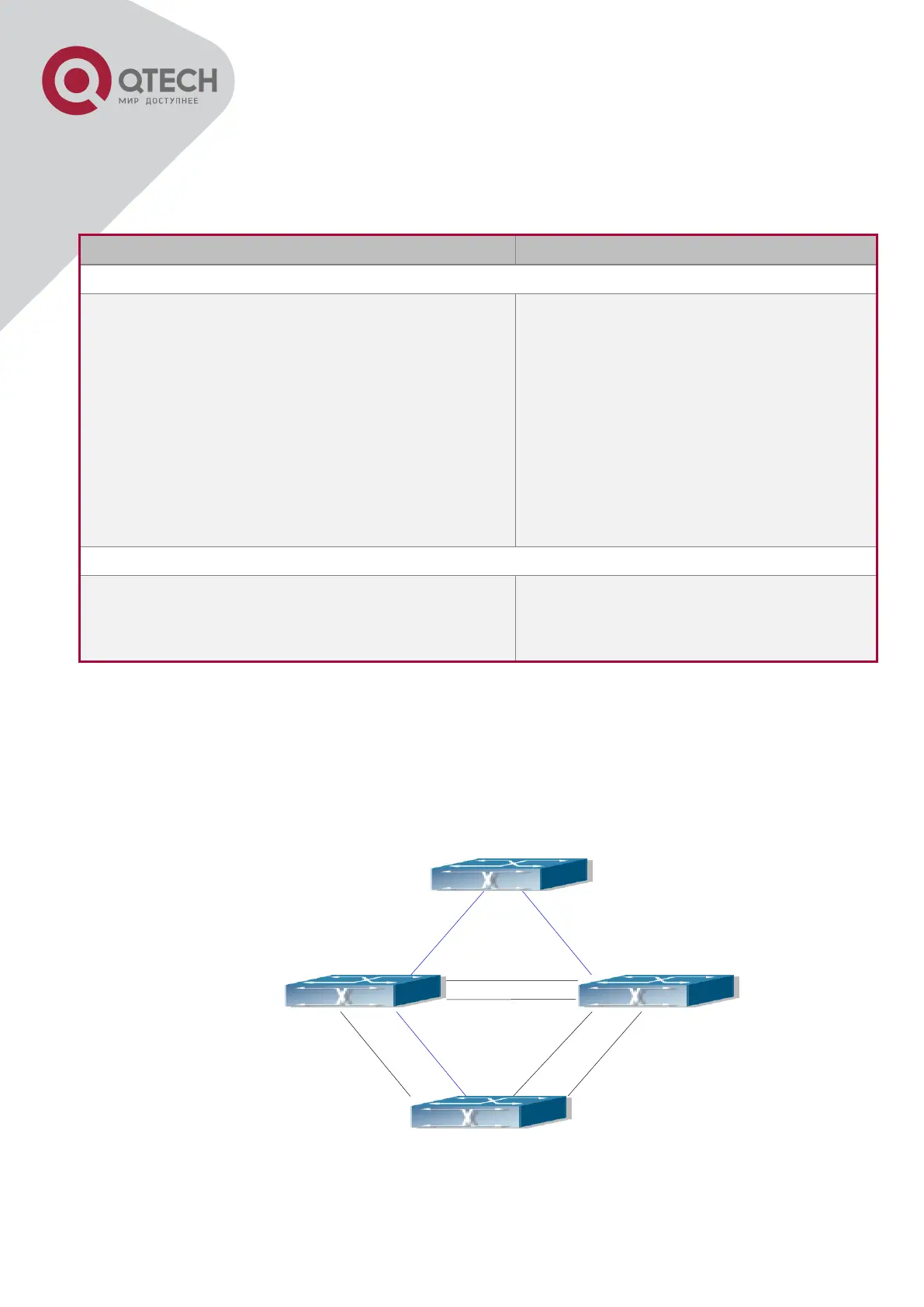
18.3 MSTP Example
The following is a typical MSTP application example:
Typical MSTP Application Scenario
spanning-tree tcflush {enable| disable| protect}
no spanning-tree tcflush
Enable: the spanning-tree flush once the
topology changes.
Disable: the spanning tree don’t flush
when the topology changes.
Protect: the spanning-tree flush not more
than one time every ten seconds.
The no command restores to default
setting, enable flush once the topology
changes.
spanning-tree tcflush {enable| disable| protect}
no spanning-tree tcflush
Configure the port flush mode.
The no command restores to use the
global configured flush mode.

 Loading...
Loading...