Security: SSH Client
Overview
337 Cisco Sx350, SG350X, SG350XG, Sx550X & SG550XG Series Managed Switches, Firmware Release 2.2.5.x
19
Authentication information must be entered by the user, both on the device and on the SSH
server, although this guide does not describe server operations.
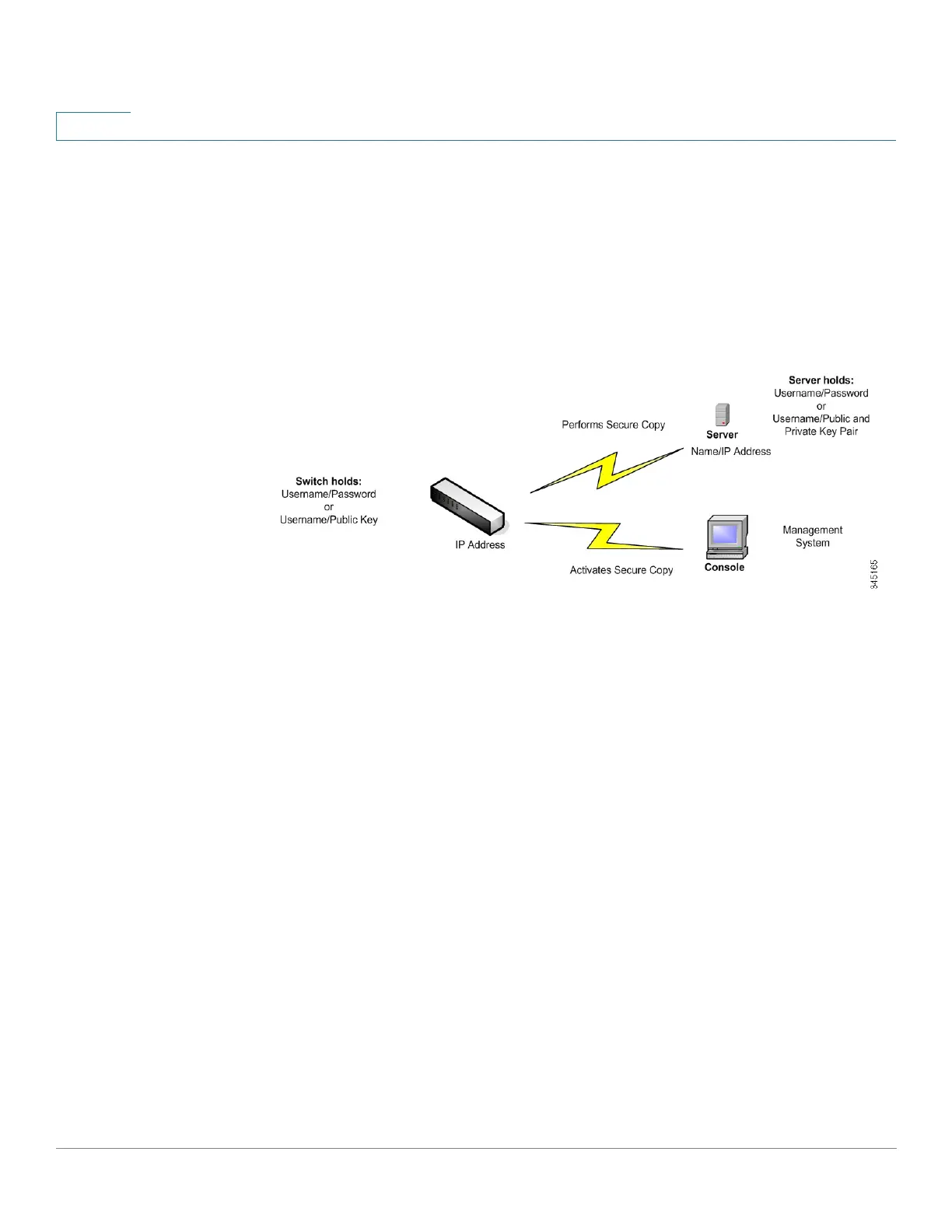
The following illustrates a typical network configuration in which the SCP feature might be
used.
Typical Network Configuration
SSH Server Authentication
A device, as an SSH client, only communicates with a trusted SSH server. When SSH server
authentication is disabled (the default setting), any SSH server is considered trusted. When
SSH server authentication is enabled, the user must add an entry for the trusted servers to the
Trusted SSH Servers Table. This table stores the following information per each SSH Trusted
server for a maximum of 16 servers, and contains the following information:
• Server IP address/host name
• Server public key fingerprint
When SSH server authentication is enabled, the SSH client running on the device
authenticates the SSH server using the following authentication process:
• The device calculates the fingerprint of the received SSH server’s public key.
• The device searches the SSH Trusted Servers table for the SSH server’s IP address/
host name. One of the following can occur:
- If a match is found, both for the server’s IP address/host name and its fingerprint,
the server is authenticated.
 Loading...
Loading...