120
ACL assignment configuration example
Network requirements
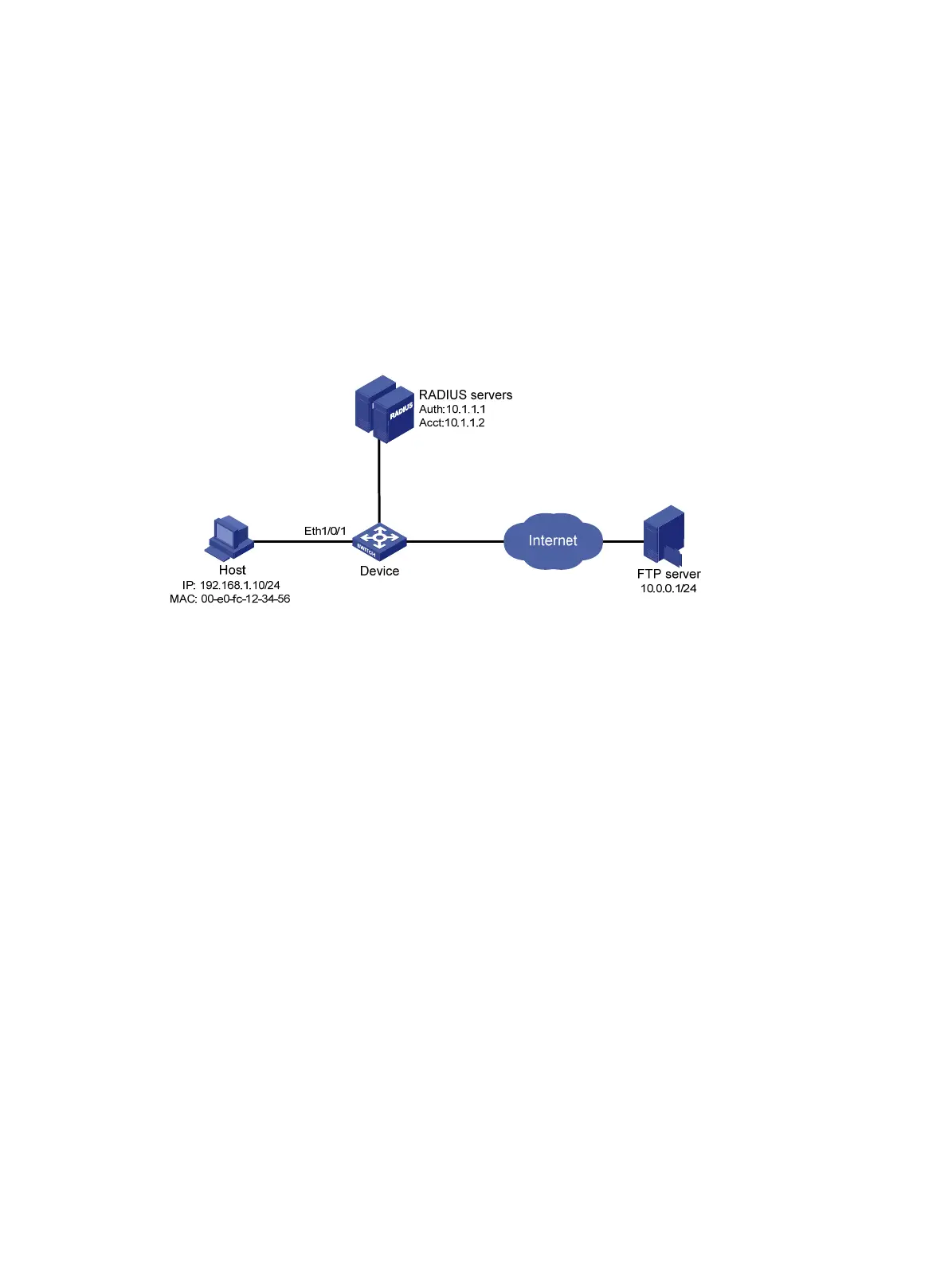
As shown in Figure 35, a host connects to the device's port Ethernet 1/0/1, and the device uses RADIUS
servers to perform authentication, authorization, and accounting.
Perform MAC authentication on port Ethernet 1/0/1 to control Internet access. Make sure that an
authenticated user can access the Internet but the FTP server at 10.0.0.1.
Use MAC-based user accounts for MAC authentication users. The MAC addresses are hyphen separated
and in lower case.
Figure 35 Network diagram
Configuration procedure
1. Make sure the RADIUS server and the access device can reach each other.
2. Configure the ACL assignment:
# Configure ACL 3000 to deny packets destined for 10.0.0.1.
<Sysname> system-view
[Sysname] acl number 3000
[Sysname-acl-adv-3000] rule 0 deny ip destination 10.0.0.1 0
[Sysname-acl-adv-3000] quit
3. Configure RADIUS-based MAC authentication on the device:
# Configure a RADIUS scheme.
[Sysname] radius scheme 2000
[Sysname-radius-2000] primary authentication 10.1.1.1 1812
[Sysname-radius-2000] primary accounting 10.1.1.2 1813
[Sysname-radius-2000] key authentication simple abc
[Sysname-radius-2000] key accounting simple abc
[Sysname-radius-2000] user-name-format without-domain
[Sysname-radius-2000] quit
# Apply the RADIUS scheme to an ISP domain for authentication, authorization, and accounting.
[Sysname] domain 2000
[Sysname-isp-2000] authentication default radius-scheme 2000
[Sysname-isp-2000] authorization default radius-scheme 2000
[Sysname-isp-2000] accounting default radius-scheme 2000
[Sysname-isp-2000] quit
 Loading...
Loading...















