154
Task Command Remarks
Display portal server statistics on a
specific interface or all interfaces.
display portal server statistics { all
| interface interface-type
interface-number } [ | { begin |
exclude | include }
regular-expression ]
Available in any view
Display TCP spoofing statistics.
display portal tcp-cheat statistics
[ | { begin | exclude | include }
regular-expression ]
Available in any view
Display information about portal
users on a specific interface or all
interfaces.
display portal user { all | interface
interface-type interface-number }
[ | { begin | exclude | include }
regular-expression ]
Available in any view
Clear portal connection statistics
on a specific interface or all
interfaces.
reset portal connection statistics
{all | interface interface-type
interface-number }
Available in user view
Clear portal server statistics on a
specific interface or all interfaces.
reset portal server statistics { all |
interface interface-type
interface-number }
Available in user view
Clear TCP spoofing statistics. reset portal tcp-cheat statistics Available in user view
Portal configuration examples
Configuring direct portal authentication
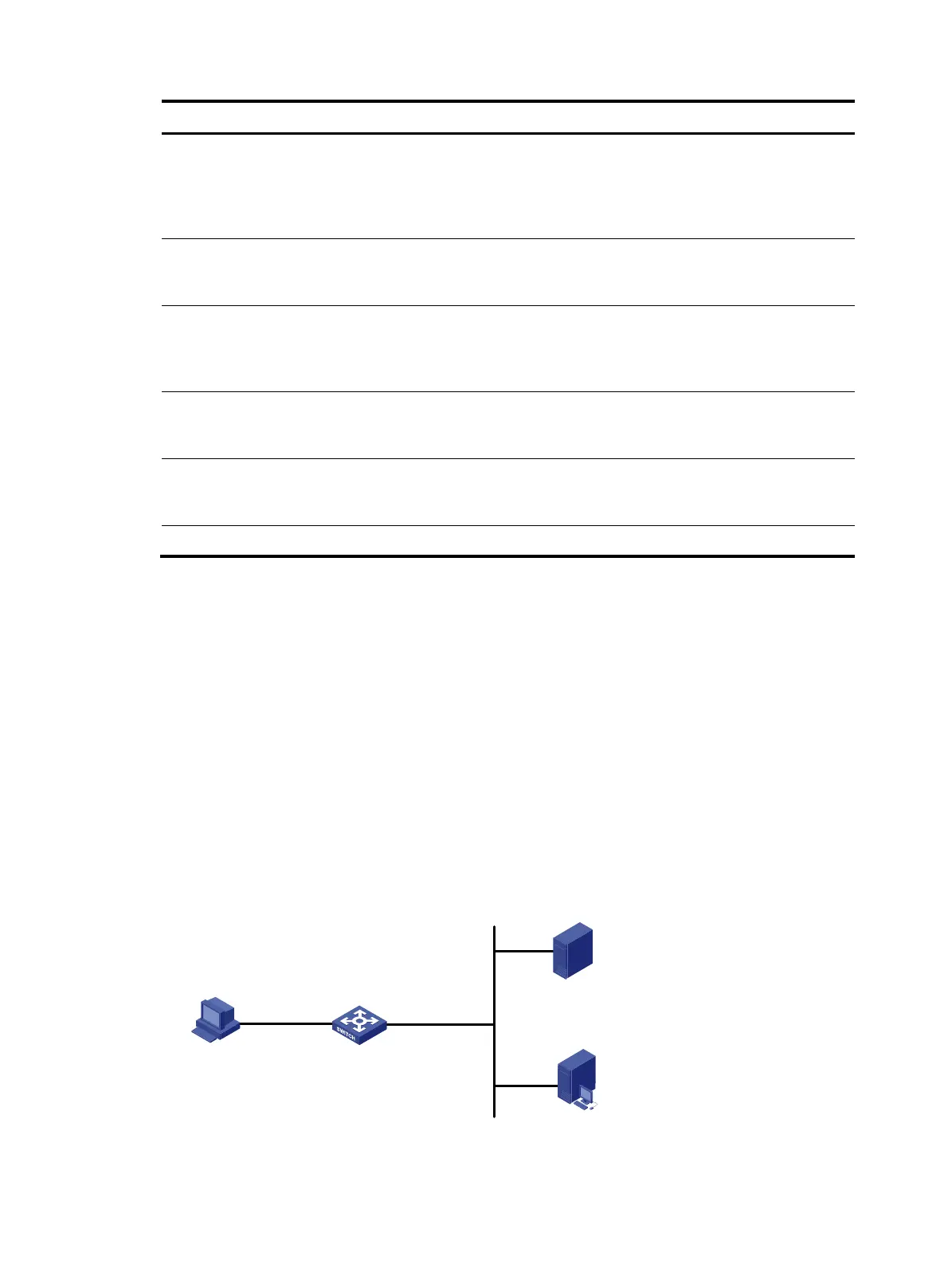
Network requirements
As shown in Figure 45:
• The host is directly connected to the switch and the switch is configured for direct authentication. The
host is assigned with a public network IP address either manually or through DHCP. Before passing
portal authentication, users can access only the portal server. After passing portal authentication,
users can access Internet resources.
• A RADIUS server serves as the authentication, authorization, and accounting server.
Figure 45 Network diagram
RADIUS server
Switch
Host
2.2.2.2/24
Gateway:2.2.2.1/24
Vlan-int100
2.2.2.1/24
Vlan-int2
192.168.0.100/24
Portal server
192.168.0.111/24
192.168.0.112/24
 Loading...
Loading...















