66
66
SME2-IS - Manual - 06 - 2021
INSTALLATION
— Network communication security
The device does not use unencrypted protocols like telnet, ftp. All communications required to con-
gure the equipment, such as calibrations, CID transmission, etc. are handled by the “SSH” protocol
in encrypted mode.
Protocols for data exchange with SCADA, e.g. IEC61850 / DNP3 / MODBUSTCP, are not encrypted, if
implementation of IEC62351 specications is not expressly requested.
The NTP, PTP synchronisation protocols are not normally encrypted.
— Cybersecurity application scheme
The conguration of the SME2-IS and monitoring functions pose problems relating to the security
and privacy of the data trafc exchanged between the equipment and the remote control centre.
The following aspects must be considered:
• Data trafc encryption, to prevent hijacking, analysis and free modication by third parties
• Implementation of an authentication mechanism to prevent the generation of false third party mes-
sages and prevent their recognition as valid
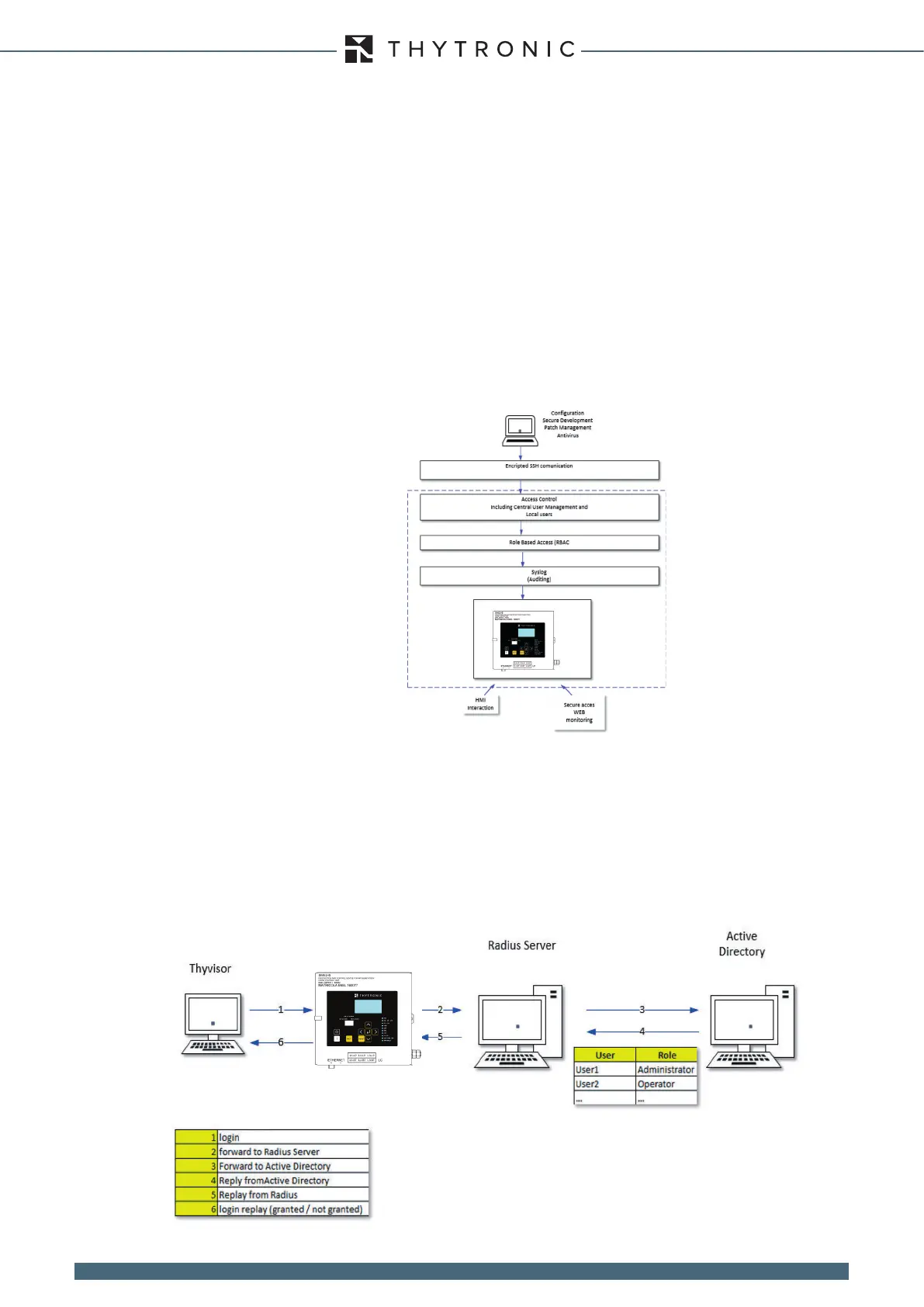
— Access procedure
The authentication mechanism consists in sending authentication requests from the incoming board
to a remote RADIUS authentication server which handles user validation, and returns positive or
negative feedback to the CPU depending on whether the user's credentials are valid or not, along
with user level information.
RADIUS authentication employs a remote server and uses a secret shared by the board and the serv-
er to validate requests for access. The congurator enables denition of all the parameters required
for this type of authentication.

 Loading...
Loading...