Protection from unauthorized access
14
6.5
Port authentication according to 802.1X
Basic - L3P
Release
4.0
11/07
6.5 Port authentication accord-
ing to 802.1X
6.5.1 Description of port authentication according
to 802.1X
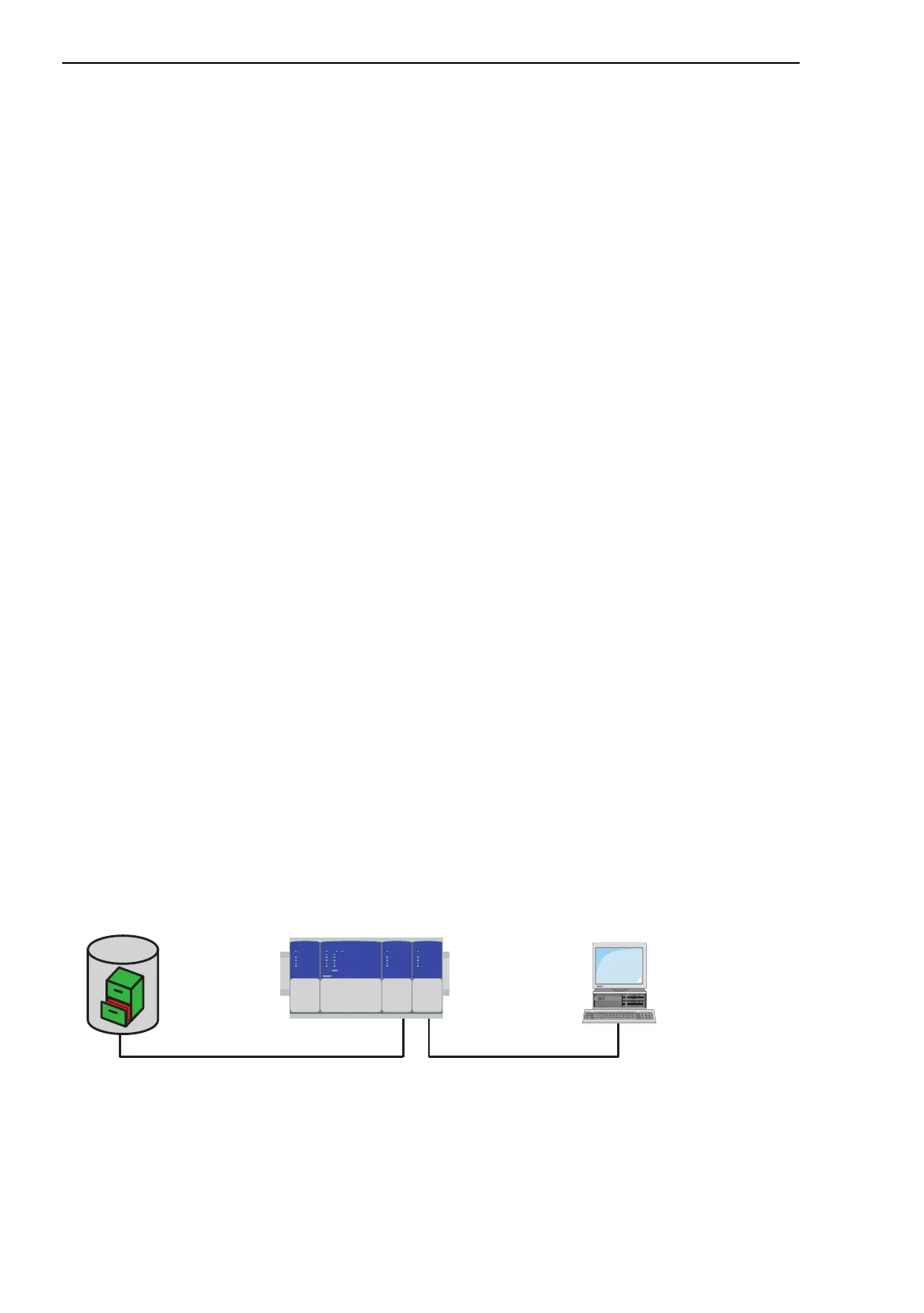
The port-based network access control is a method described in norm IEEE
802.1X to protect IEEE 802 networks from unauthorized access. The proto-
col controls the access at a port by authenticating and authorizing a device
that is connected to this port of the Switch.
The authentication and authorization is carried out by the authenticator, in
this case the Switch. The Switch authenticates (or does not authenticate) the
supplicant (the querying device, e.g. a PC), which means that it permits the
access to the services it provides (e.g. access to the network to which the
Switch is connected), or else refuses it. In the process, the Switch accesses
an external authentication server (RADIUS server), which checks the au-
thentication data of the supplicant. The Switch exchanges the authentication
data with the supplicant and the server via the Extensible Authentication Pro-
tocol over LANs (EAPOL) and the RADIUS protocol respectively.
Figure 24: Radius server connection
802.1X SupplicantSwitch/AuthenticatorRADIUS Server
hhhh
Power MICE

 Loading...
Loading...











