Protection from unauthorized access
Basic - L3P
Release
4.0
11/07
6.6
Access Control Lists (ACL).
21
X PERMIT
X Source MAC: ANY
X Destination MAC: 01:15:4E:00:00:00
X Destination MAC mask: 00:00:00:00:00:03
X CLI command in the Config-mac-access mode:
permit any 01:15:4E:00:00:00 00:00:00:00:00:03
Note: MAC address masks in the rules of ACLs are inverse.
This means that if you want to mask a single MAC address, you select the
network mask 00:00:00:00:00:00.
If you want to mask MAC addresses in the range from 00:80:63:00:00:00 to
00:80:63:FF:FF:FF, you select the network mask 00:00:00:FF:FF:FF.
6.6.4 Configuring IP ACLs
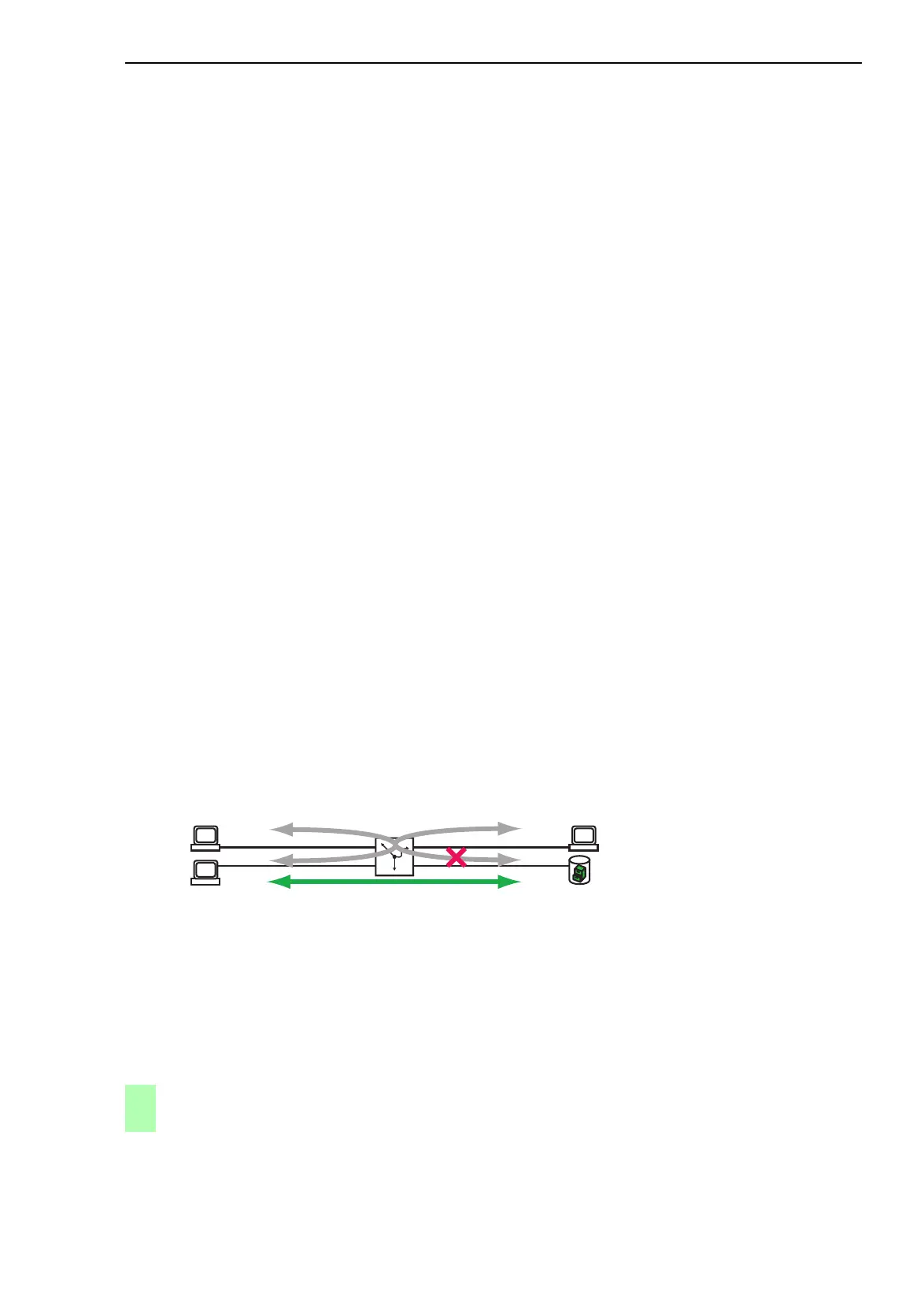
Example: Extended ACL
B and C are not allowed to communicate with A.
enable Switch to the Priviledged EXEC mode.
configure Switch to the Configuration mode.
CB
DA
IP: 10.0.1.13/24
IP: 10.0.1.158/24
IP: 10.0.1.11/24
IP: 10.0.1.159/24
Interface: 3.1
Interface: 2.1Interface: 1.3
Interface: 2.3

 Loading...
Loading...











