Chapter 13 - Configuring The Firewall
Policies are defined in the file /etc/shorewall/policy and are modified from the
Default Policy menu.
Masquerading And SNAT
Masquerading and Source NAT (SNAT) are forms of dynamic NAT.
Masquerading substitutes a single IP address for an entire internal network. Use
masquerading when your ISP assigns you an IP address dynamically at connection
time.
SNAT substitutes a single address or range of addresses that you been assigned by
your ISP. Use SNAT when your ISP assigns you one or more static IP addresses that
you wish to one or more internal hosts.
The masquerading/SNAT entries are defined in the file /etc/shorewall/masq and are
modified from the Masquerading menu. Each entry is of the form:
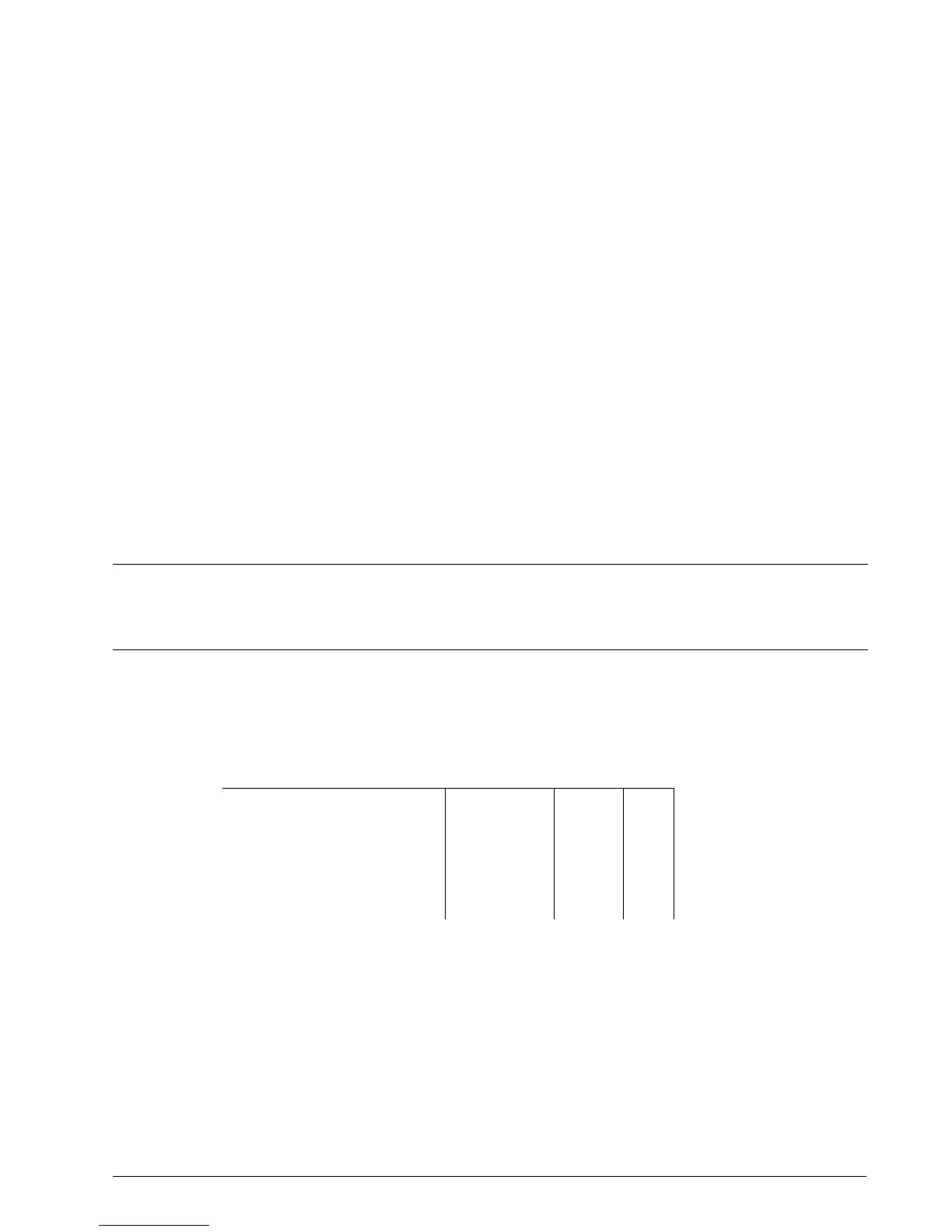
Interface Subnet Address Protocol Port(s)
Interface is the outgoing (WAN or Ethernet) interface and is usually your Internet
interface.
Subnet is the subnet that you wish to hide. It can be an interface name (such as eth1)
or an subnetted IP address.
Address is an (optional IP) address that you wish to masquerade as.
Note: The presence of the Address field determines whether masquerading or SNAT is
being used. Masquerading is used when only Interface and Subnet are present. SNAT
is used when Interface, Subnet and Address are present.
Protocol (optionally) takes on the name of protocols (e.g. tcp, udp..) that you wish to
masquerade.
Ports (optionally) takes on the ports to masquerade when protocol is set to tcp or udp.
These can be raw port numbers or names as found in file /etc/services.
Some examples should illustrate the use of masquerading:
Rule Interface Subnet Address Protocol Ports
1 eth1 eth2
2 ppp+ eth2 66.11.180.161
3 ppp+ 192.168.0.0/24 66.11.180.161
4 w1ppp eth1 100.1.101.16
5 w1ppp eth1 100.1.101.16 tcp smtp
1) In this masquerading rule, port eth2 is connected to the local network and eth1 is
connected to a DSL modem. Traffic from the subnet handled by eth2 should be
translated to whatever IP is assigned to the modem. Internet clients will not be able
to determine the router's public address unless some form of dynamic dns is
employed.
2) In this SNAT rule a static address of 66.11.180.161 is acquired from the ISP.
Traffic from the subnet handled by eth2 should be translated to 66.11.180.161 as it
sent to the Internet over ppp. The + at the end of “ppp+” causes Shorewall to
match any ppp interface.
RuggedCom 115

 Loading...
Loading...