Manage Device Security
276
Insight Managed 28-Port Gigabit Ethernet Smart Cloud Switch with 2 SFP 1G & 2 SFP+ 10G Fiber Ports
9. To refresh the page with the latest information about the switch, click the Refresh button.
The following table describes the nonconfigurable data that is displayed.
Configure Access Rule Settings
You can add security access rules. You can apply changes an the access rule only when
the access profile is in a deactivated state.
Note: Make sure that you create the access profile before you add rules.
To configure access rules:
1. Connect your computer to the same network as the switch.
You can use a WiFi or wired connection to connect your computer to the network, or
connect directly to a switch that is off-network using an Ethernet cable.
2. Launch a web browser.
3. In the address field of your web browser, enter the IP address of the switch.
If you do not know the IP address of the switch, see Access the Switch on page 13.
The login window opens.
4. Enter the switch’s password in the password field.
The default password is password. If you added the switch to a network on the Insight
app before and you did not yet change the password through the local browser interface,
enter your Insight network password.
The System Information page displays.
5. Select Security > Access > Access Control > Access Rule Configuration.
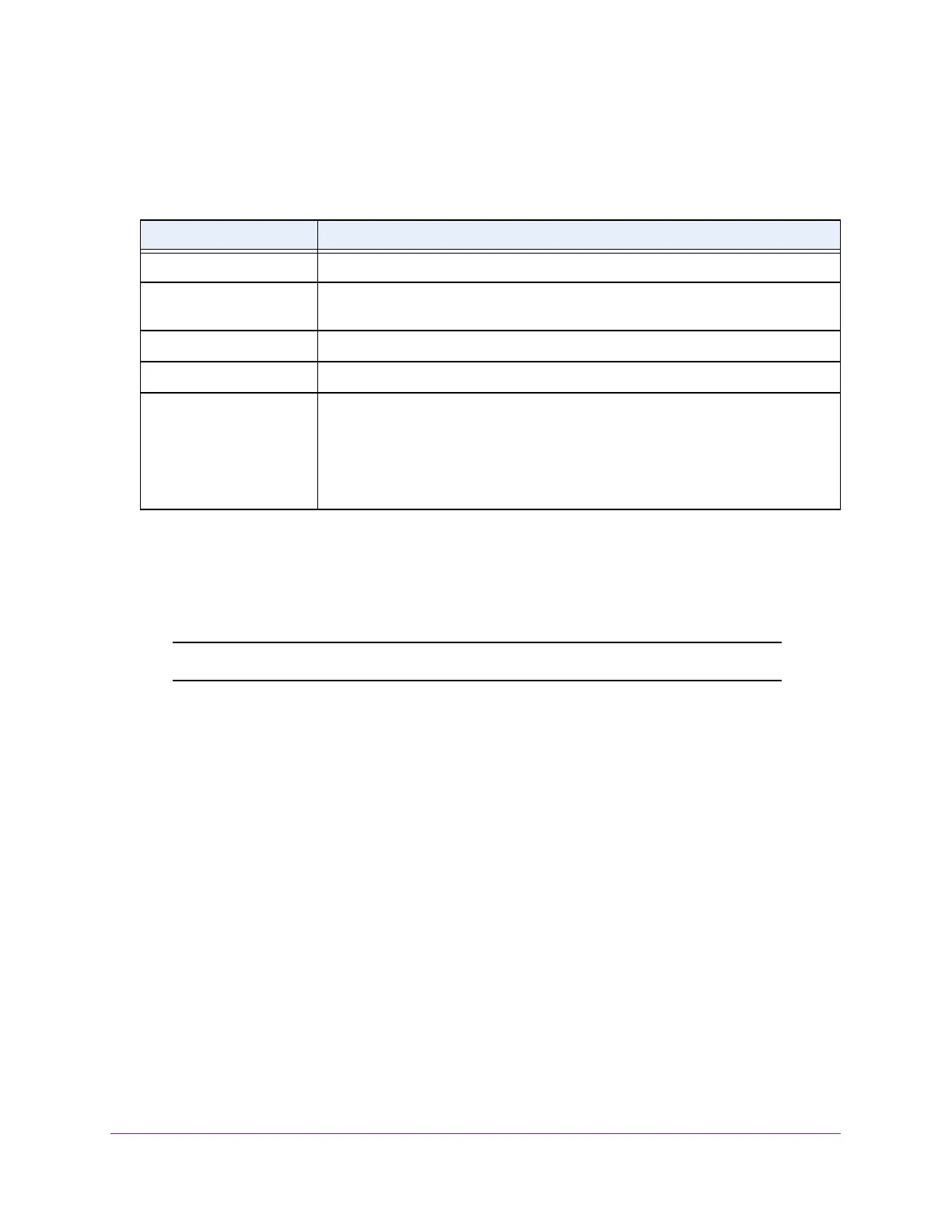
Table 70. Access profile configuration profile summary
Field Description
Rule Type The action performed when the rules match.
Service Type The selected service type. The policy is restricted by the selected service type
chosen. The possible methods are HTTP, and secure HTTP (SSL).
Source IP Address Source IP address of the client originating the management traffic.
Mask The subnet mask of the IP Address of the client originating the management traffic.
Priority The priority of the rule. The rules are validated against the incoming management
request in the ascending order of their priorities. If a rule matches, action is
performed and subsequent rules are ignored. For example, if a source IP address
of 10.10.10.10 is configured with priority 1 to permit and source IP address
10.10.10.10 is configured with priority 2 to deny, access is permitted if the profile is
active, and the second rule is ignored.
 Loading...
Loading...