S350 Series 24-Port (PoE+) and 48-Port Gigabit Ethernet Smart Managed Pro Switches
Manage Device Security User Manual275
6. To delete a MAC ACL-to-interface binding, do the following:
a. Select the check box next to the interface.
b. Click the Delete button.
The binding is removed.
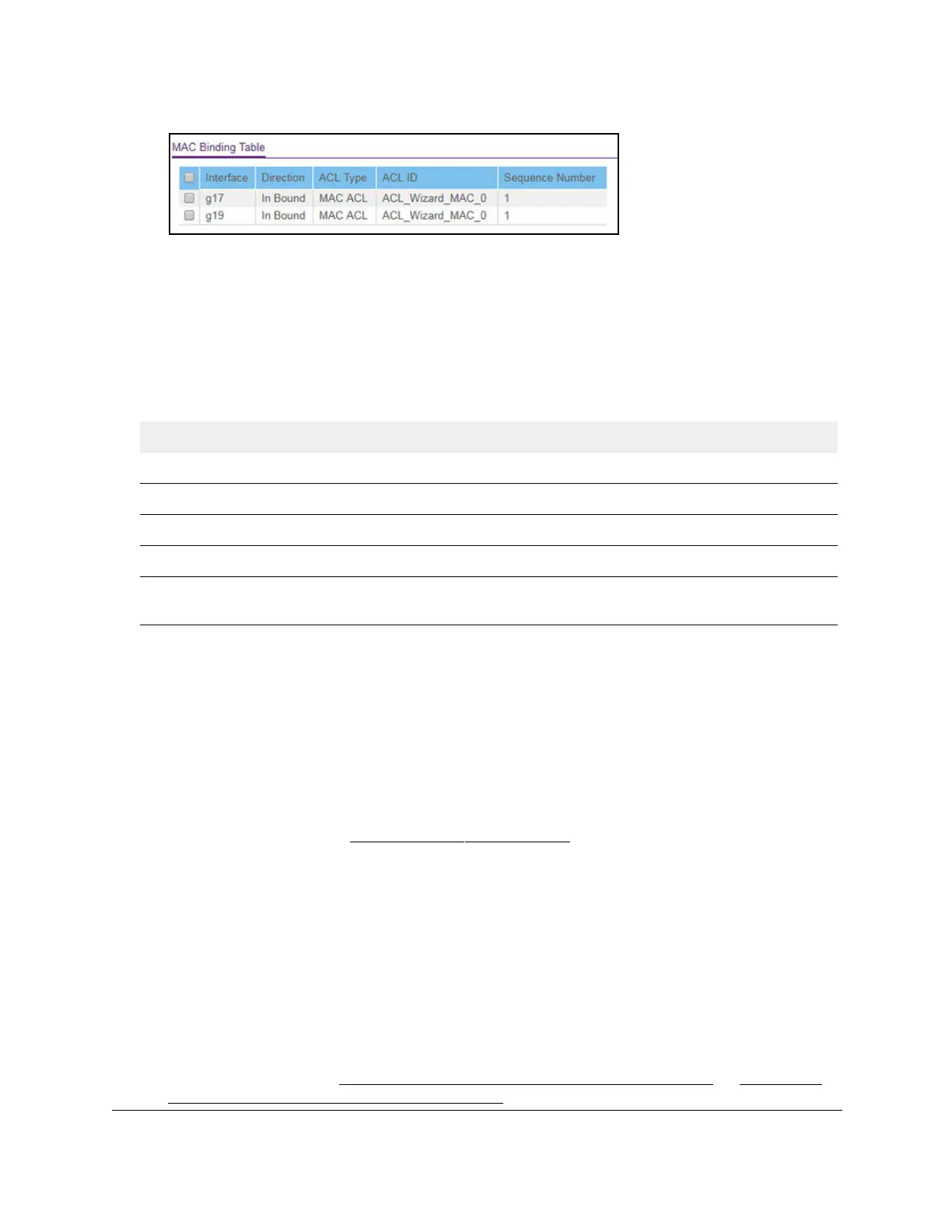
The following table describes the information that is displayed in the MAC Binding Table.
Table 62. MAC Binding Table
Field Description
Interface The interface of the ACL assigned.
Direction The selected packet filtering direction for the ACL.
ACL Type The type of ACL assigned to the selected interface and direction.
ACL ID The ACL name identifying the ACL assigned to the selected interface and direction.
Sequence Number The sequence number signifying the order of the specified ACL relative to other ACLs
assigned to the selected interface and direction.
Configure a Basic or Extended IP ACL
An IP ACL consists of a set of rules that are matched sequentially against a packet. When a
packet meets the match criteria of a rule, the specified rule action (Permit or Deny) is taken,
and the additional rules are not checked for a match. You must specify the interfaces to
which an IP ACL applies, as well as whether it applies to inbound or outbound traffic.
Multiple steps are involved in defining an IP ACL and applying it to the switch:
1. Add an IP ACL ID (see
Add an IP ACL on page 276).
The differences between a basic IP ACL and an extended IP ACL are as follows:
• Numbered ACL from 1 to 99. Creates a basic IP ACL, which allows you to permit or
deny traffic from a source IP address.
•
Numbered ACL from 100 to 199. Creates an extended IP ACL, which allows you to
permit or deny specific types of Layer 3 or Layer 4 traffic from a source IP address to
a destination IP address.
This type of ACL provides more granularity and filtering
capabilities than the basic IP ACL.
• Named IP ACL. Create an extended IP
ACL with a name string that is up to 31
alphanumeric characters in length. The name must start with an alphabetic character
.
2. Create an IP rule (see
Configure Rules for a Basic IP ACL on page 278 or Configure
Rules for an Extended IP ACL on page 282).
 Loading...
Loading...