18
Grounding an A5800AF-48G/A5820AF-24XG switch
To connect the grounding cable:
1. Attach the two-hole grounding lug at one end of the grounding cable to a grounding point on the
switch chassis see ―Connecting the grounding cable to the chassis.‖
2. Remove the hex nut of a grounding post on the grounding strip.
3. Attach the OT terminal at the other end of the grounding cable to the grounding strip through the
grounding post, and fasten the OT terminal with the removed hex nut.
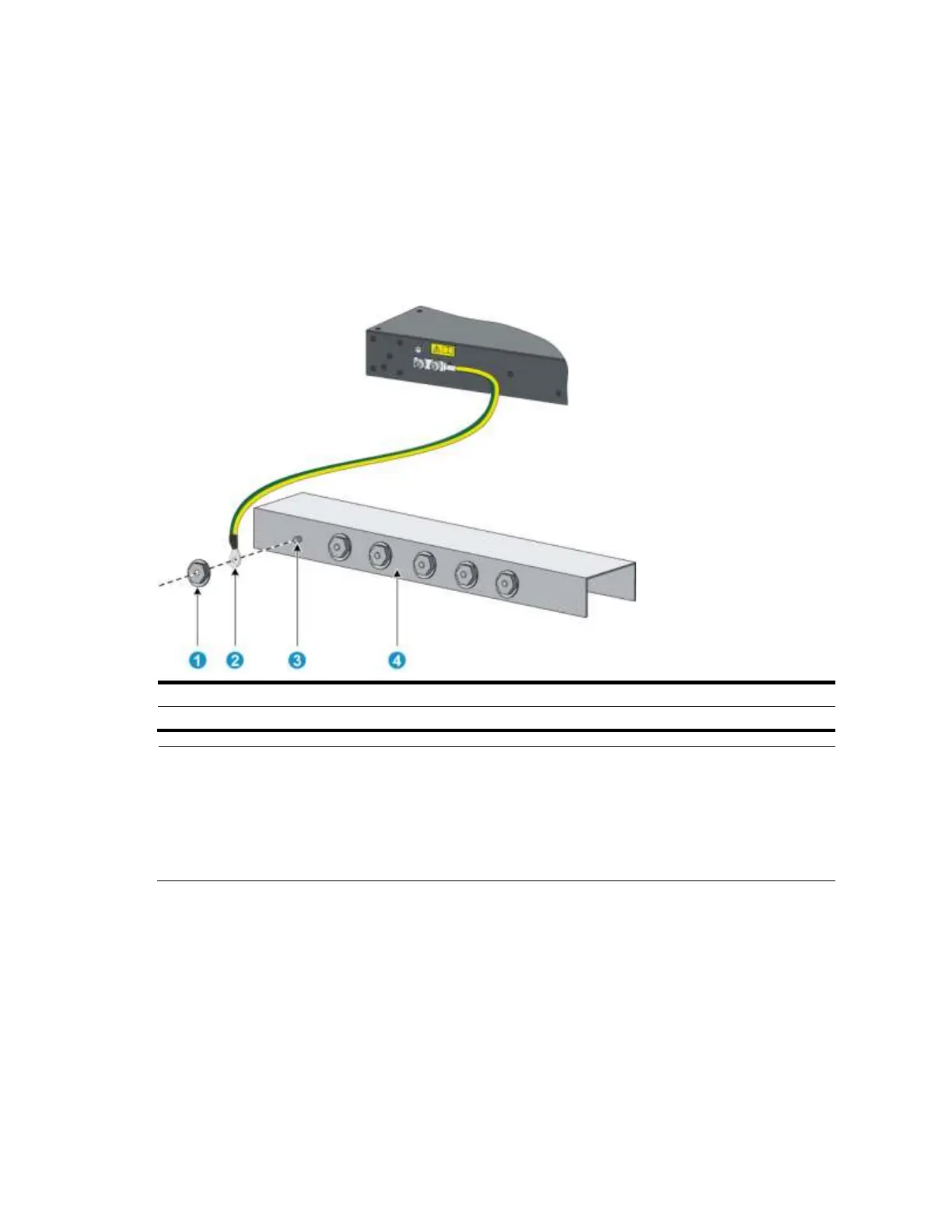
Figure 20 Connecting the grounding cable to a grounding strip
NOTE:
HP recommends that you use the primary grounding point or auxiliary grounding point 1, because the
grounding cable and grounding screw provided with the switch are applicable only to these two grounding
points.
To use auxiliary grounding point 2, you must prepare a grounding cable yourself. The connection method is the
same as connecting to the other two grounding points.
Grounding an A5800/A5820X switch (except the A5800AF-48G/A5820AF-24XG)
All A5800 and A5820X switches except the A5800AF-48G and the A5820AF-24XG have a grounding
point (with a grounding sign) on their rear panels.
To connect the grounding cable:
1. Remove the grounding screw from the rear panel of the switch chassis.
2. Attach the grounding screw to the OT terminal of the grounding cable.
3. Use a screwdriver to fasten the grounding screw into the grounding screw hole.
 Loading...
Loading...











